Counterparty Assessment
Counterparty risk assessment with intelligence-led transparency
In today’s hyper-connected and high-risk global economy, superficial due diligence is no longer sufficient. Traditional KYC processes often fail to detect shell structures, indirect ties to sanctioned entities, or hidden reputational red flags. Organizations need deeper insight into counterparties — not just to meet regulatory standards, but to avoid financial, legal, and operational fallout.
Counterparty risk is no longer theoretical. It’s systemic. Whether you’re extending credit, entering into a joint venture, onboarding a new vendor, or facilitating a cross-border transaction — your counterparty’s exposure becomes yours.
Real-World Risk Example: A global logistics provider entered a partnership with a seemingly compliant third party. Months later, leaked documents exposed the counterparty’s proxy ownership links to a sanctioned country. The reputational damage and financial penalties could have been avoided with deeper upfront assessment.
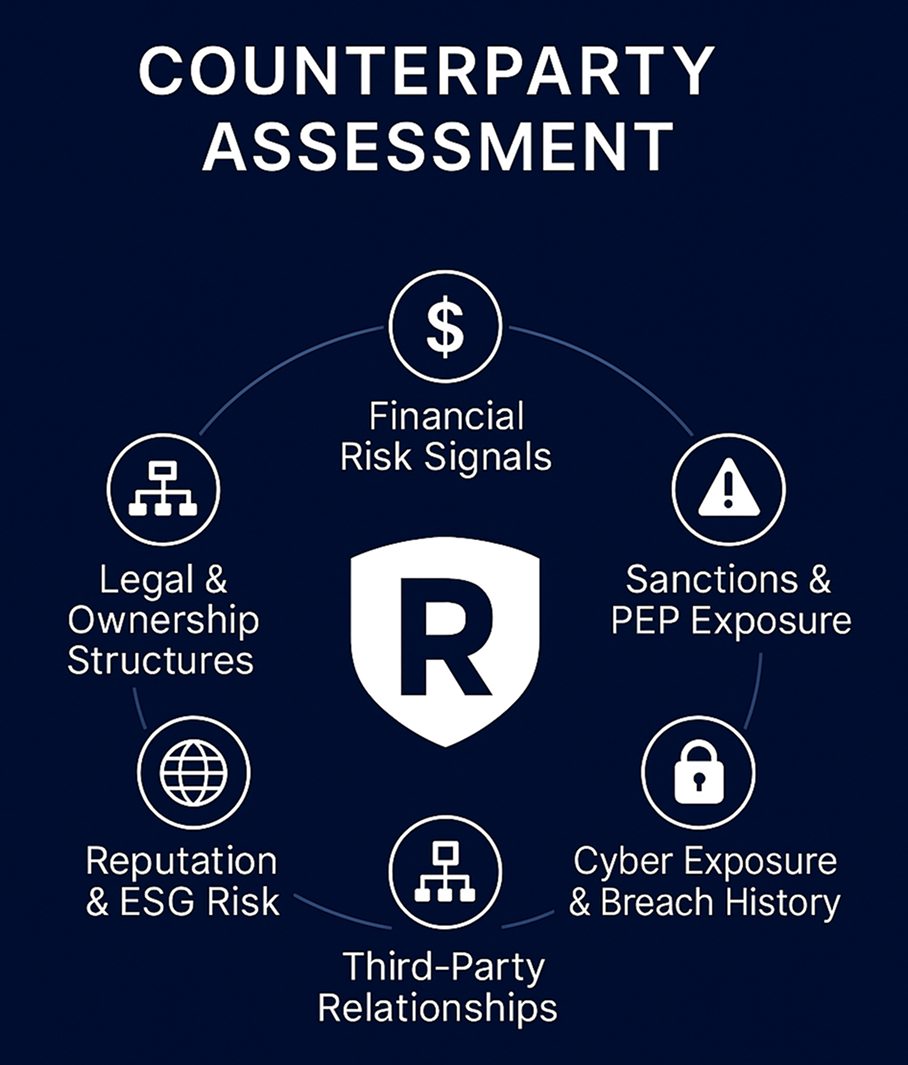
Resecurity delivers multi-layered, intelligence-driven counterparty assessments that go far beyond conventional due diligence.
| Assessment Dimension | Scope of Analysis |
|---|---|
| Legal & Ownership Structures | Corporate registries, nominee directors, offshore setups, UBO tracing |
| Financial Risk Signals | Tax evasion patterns, insolvency indicators, historical non-compliance |
| Sanctions & PEP Exposure | Screening against OFAC, EU, UN, SAMA, FATF, and other blacklists |
| Cyber Exposure & Breach History | Leaked credentials, dark web exposure, ransomware mentions |
| Reputation & ESG Risk | Adverse media, human rights violations, environmental impact flags |
| Third-Party Relationships | Mapping vendors, subsidiaries, and beneficial affiliations |
Each category is scored based on weighted risk criteria, enriched by threat intelligence and verified with open-source and proprietary data.
Client provides target entity, desired jurisdictional scope, and level of depth (screening vs. deep dive).
Data from government filings, OSINT, darknet monitoring, leaked datasets, and industry sources.
Proprietary algorithms assess the risk across six dimensions; analysts flag escalations manually.
Diagrams show ties to risky entities, shell companies, and high-risk individuals.
Receive a structured PDF report with scoring, recommendations, and a consultation if required.
Activate continuous monitoring for high-risk counterparties and trigger alerts upon risk change.
Financial Services
EDD for onboarding clients, investors, and commercial borrowers.
Defense & Aerospace
Screening suppliers, subcontractors, and international procurement chains.
Government & Public Sector
Verifying third-party affiliations and contractor integrity.
Energy & Infrastructure
Pre-qualifying vendors in regulated, high-risk geographies.
Corporate Legal & M&A
Vetting acquisition targets and strategic partners in emerging markets.
- Cyber-Enhanced Assessments – Intelligence that includes dark web, breach data, and digital footprint analysis.
- Global Regulatory Alignment – Built to support AMLD, FATF, CFT, DORA, SAMA, and OFAC requirements.
- Deeper Than Data – Not just databases, but human intelligence and proprietary investigative tools.
- Actionable Outputs – Clear scoring, visual maps, and decision-ready summaries for your team.
- Secure & Confidential – All investigations handled with strict confidentiality and legal alignment.
Whether you're conducting routine diligence or investigating complex offshore relationships, Resecurity empowers your compliance and risk teams to make informed decisions — before exposure becomes a liability.
Keep up to date with the latest cybersecurity news and developments.
By subscribing, I understand and agree that my personal data will be collected and processed according to the Privacy and Cookies Policy

Los Angeles, CA 90071 Google Maps

