
Introduction
Resecurity was the first company to identify the Smishing Triad, a group of Chinese cybercriminals targeting consumers across the globe. In August 2023, our team was able to identify their activity and locate the smishing kit they were using, successfully exploiting a vulnerability, which exposed the threat actors and their infrastructure. Since then, the group has become stealthier and upgraded its tooling, tactics, and procedures (TTPs). A group of this scale is not limited to just one threat actor; it has numerous associates with different roles, blurring its public profile. Such groups leverage a "Crime-as-a-Service" model, enabling other cybercriminals to use their smishing kit and scale their operations targeting consumers in different countries.
"No Fear of FBI"
Notably, the Chinese cybercriminal syndicates involved in smishing are brazen because they feel untouchable. They have emphasized in their communications that they do not care about U.S. law enforcement agencies. Residing in China, they enjoy complete freedom of action and engage in many illegal activities. According to the latest chatter, one identified threat actor can send up to 2,000,000 smishing messages daily. The negative aspect of this is that cybercriminals have everything needed for this, which may mean that the Smishing Triad and similar groups could easily target up to 60,000,000 victims per month, or 720,000,000 per year, enough to target every person in the US at least twice every year.
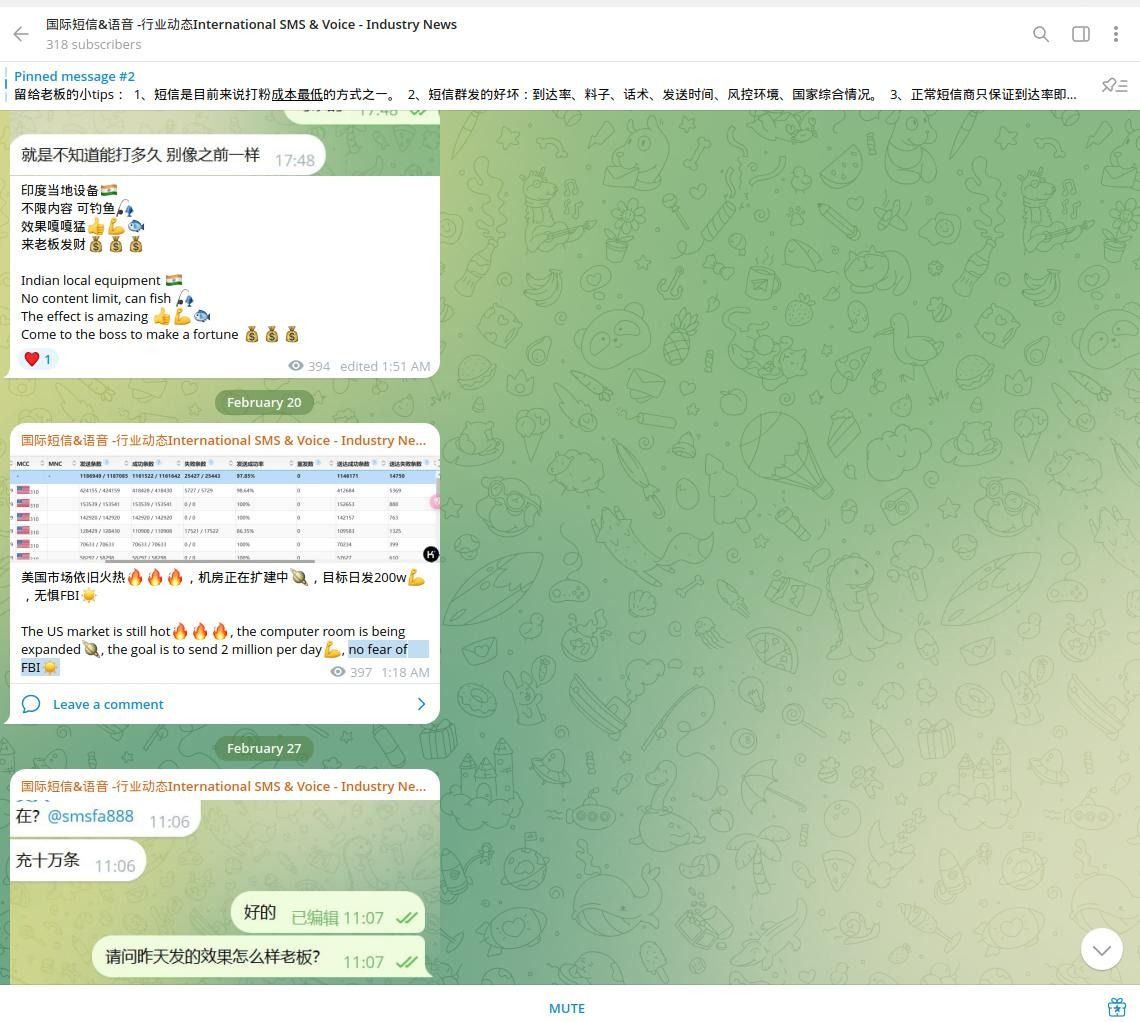
Our investigators noted that, besides Google RCS and Apple iMessage being used as the primary smishing delivery methods, the group also uses SMS gateways, specialized equipment for network operators. Telemarketing companies also use similar devices to send messages to mobile subscribers for legitimate purposes, which appears to be misused by Chinese cybercriminals in combination with other methods. To do this, actors are looking for routes to reach subscribers of specific mobile carriers abroad. Notably, some operators try to combat this type of malicious activity by detecting possible malicious content and blocking the sources of such activity. Cybercriminals use new routes in such cases, and such offers are in high demand on the Dark Web.
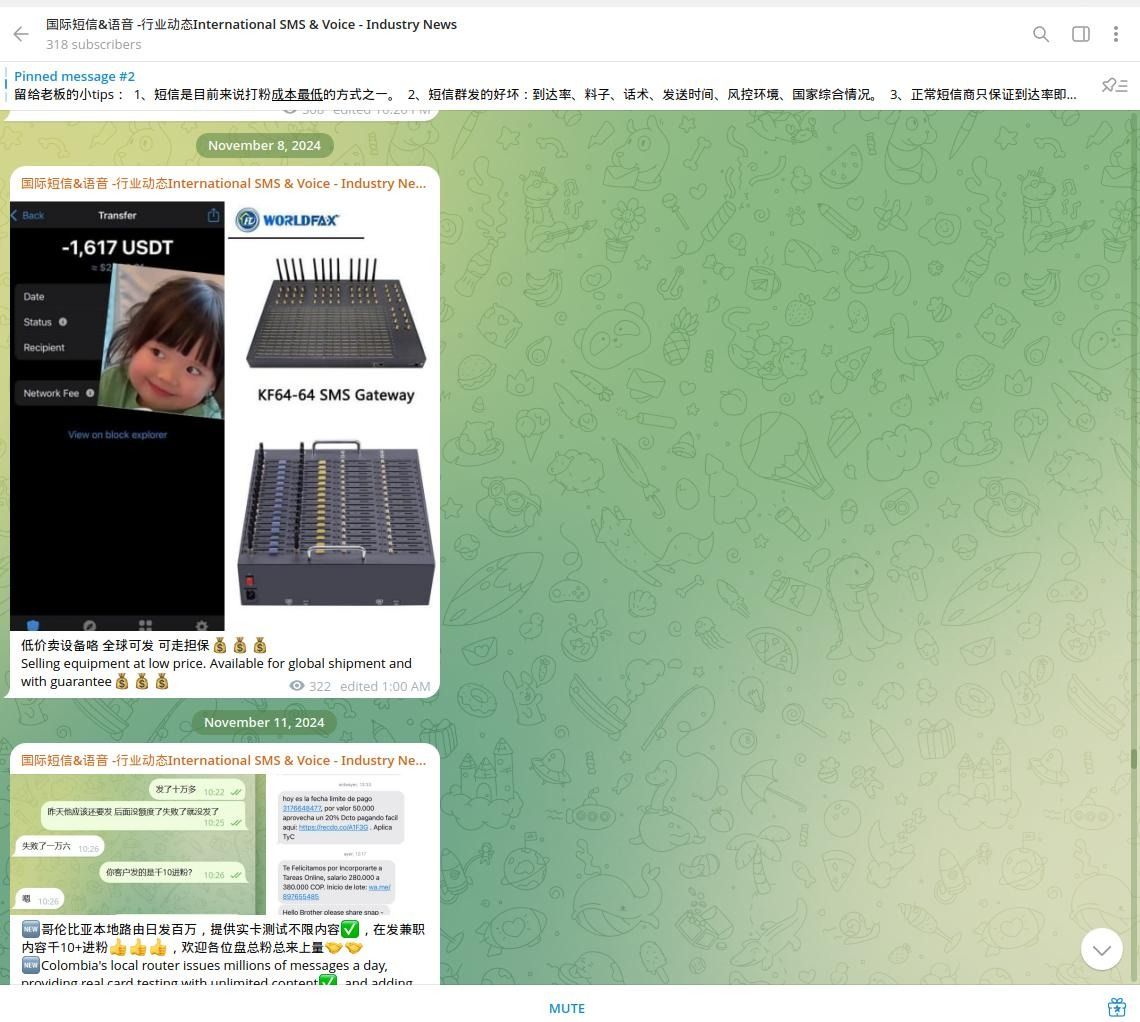
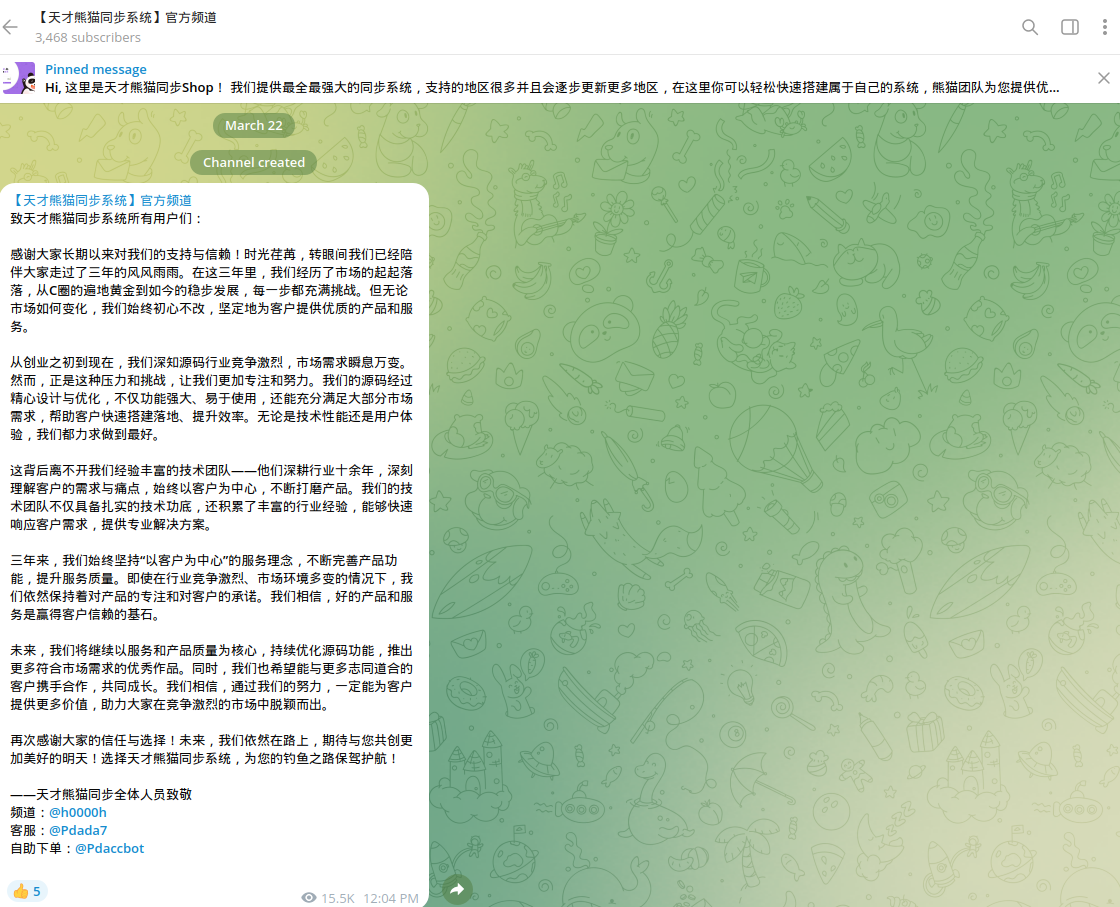
On March 22, 2025, Resecurity identified a new smishing kit known as "Panda Shop," based on the same principles used by the Smishing Triad. Notably, the giant panda is a prominent and iconic symbol of China. It's recognized domestically and internationally as a symbol of the country, representing peace, friendship, and soft power. But in this case, it doesn’t seem to bring anything good besides financial losses to consumers.
"Panda Shop" has multiple Telegram channels and interactive bots to automate service delivery. Resecurity observed an interesting trend: Chinese cybercriminals are more comfortable using Telegram IM than domestic Chinese IMs such as QQ or WeChat when involved in illegal activity. Multiple actors investigated by our HUNTER unit provided Telegram contact information and identified it as their main communication channel.
Like Smishing Triad, the group also provides smishing distribution services via Apple IM and Android RCS. Such "Crime-as-a-Service" offerings are extremely popular in the Chinese underground ecosystem.
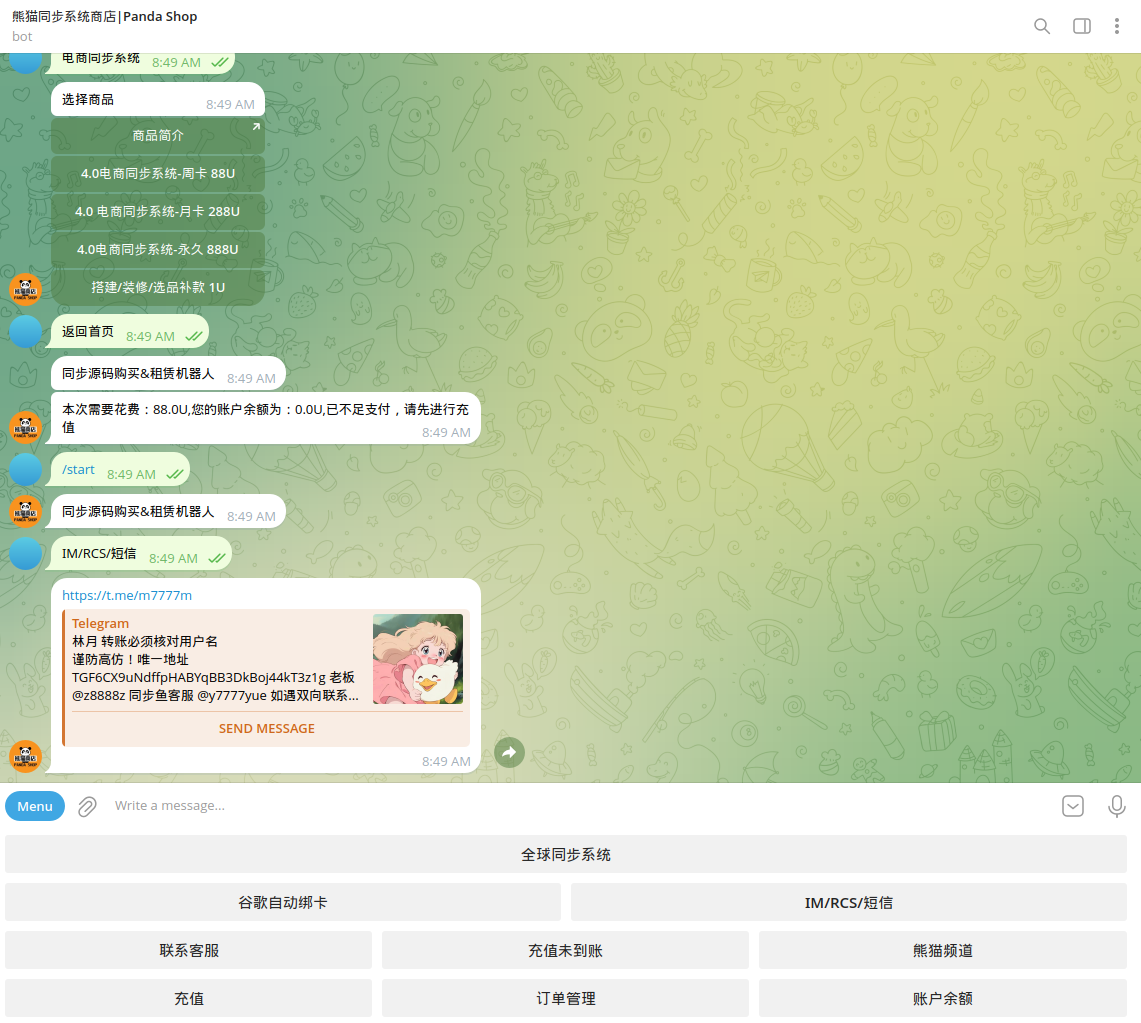
The bad actors buy compromised Apple and Gmail accounts in bulk to facilitate distribution. Multiple requests by their peers to acquire such large volumes of accounts were identified.

Unlike SMS, which relies on cellular networks, Apple iMessage and Android RCS use internet-based communication. Cybercriminals prefer modern messaging platforms because they provide a richer set of tools for creating convincing attacks, better engagement features, and more sophisticated methods of deception. The ability to leverage internet-based communication and platform-specific features makes these attacks more effective and challenging to detect than traditional SMS-based approaches
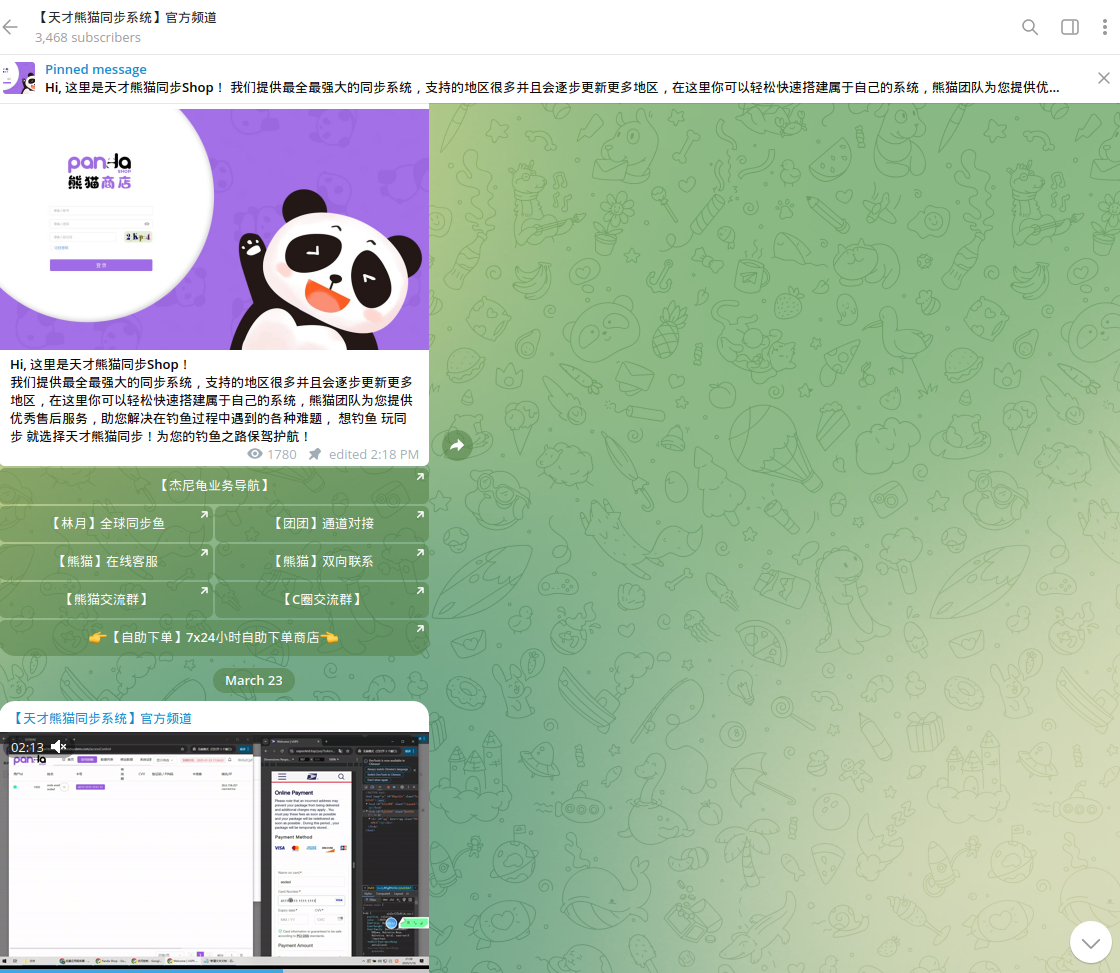
Like the Smishing Triad, Panda Shop offers a customized smishing kit that can be deployed on any server. Our investigators suspect the group includes Smishing Triad members who transitioned their operations under the new brand after being publicly shamed. The kit's structure and scripting scenarios analyzed by Resecurity mimic the same product but include specific improvements and new supported templates.
The smishing kit can be purchased via customer support or an automated Telegram bot. The actors behind the kit also provide interactive manuals on how to use it.
Resecurity identified multiple actors leveraging the Panda Shop smishing kit for Google Wallet and Apple Pay, harvesting traditional credit card and PII data, and intercepting transactions. This approach is widely used in NFC-enabled fraud, where cybercriminals use tools like Z-NFC, X-NFC, and UFO NFC, as described in our previous publications. Based on our observations, the actors behind smishing campaigns are tightly connected with those involved in merchant fraud and money laundering activity. Smishing is one of the main catalysts behind carding activities, providing cybercriminals with substantial volumes of compromised data collected from victims.
Panda Smishing Kit
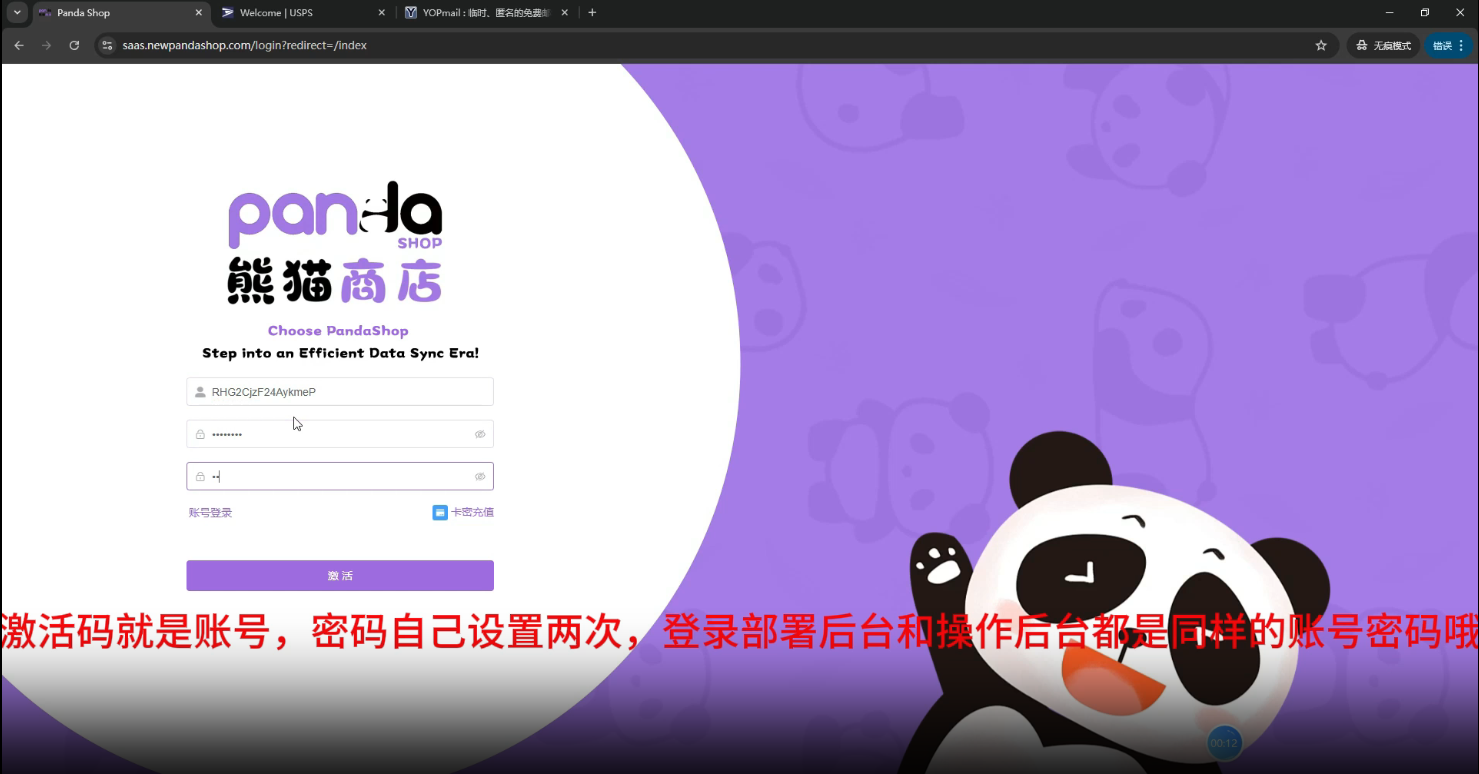
The smishing kit can be customized and installed on a virtual server. The operator must provide credentials, after which the kit will be unpacked and deployed.
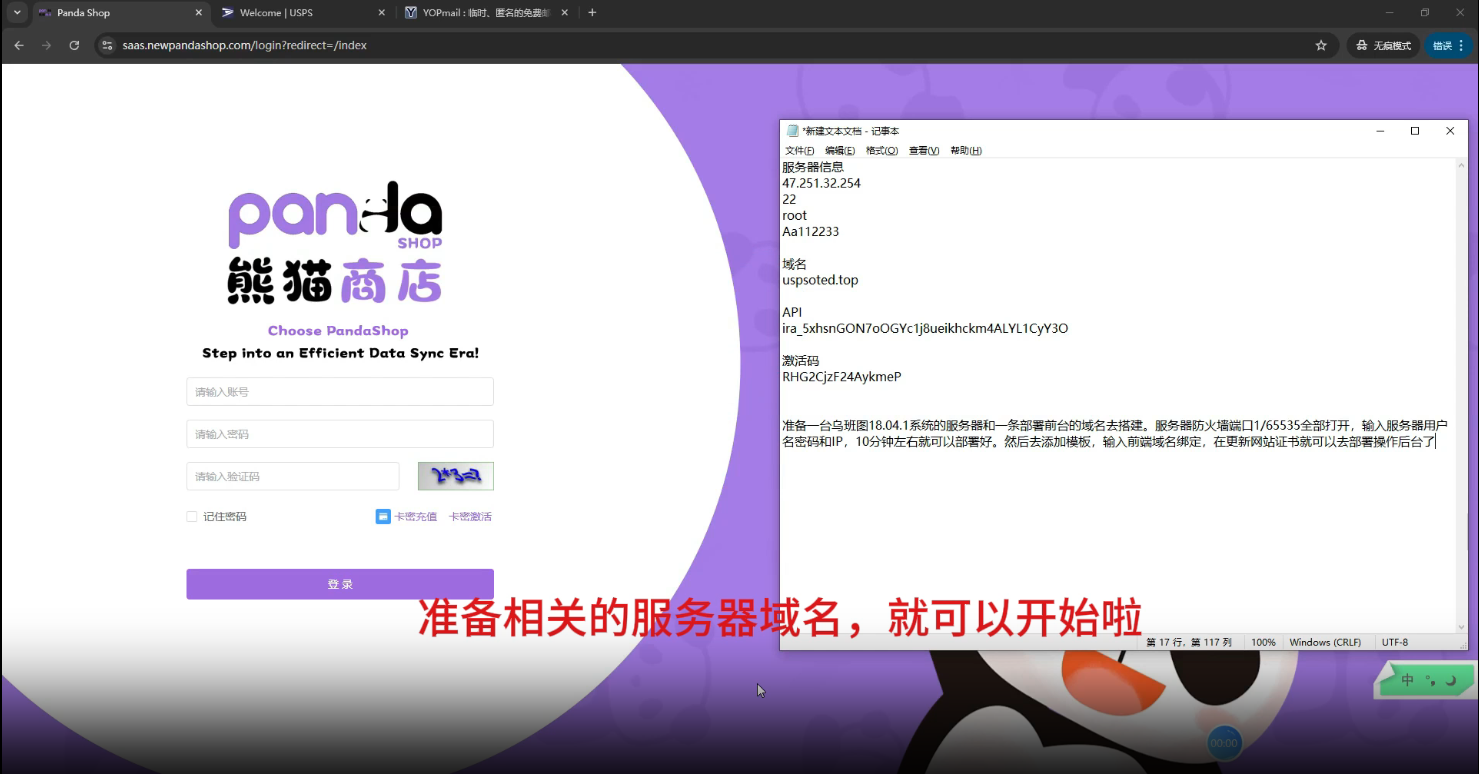
New clients need to contact "Panda Shop" customer support via Telegram to receive access credentials.
In addition to U.S.-based services, the smishing kit supports templates mimicking various brands from other countries, including popular ISPs such as Du (UAE), to intercept PII.
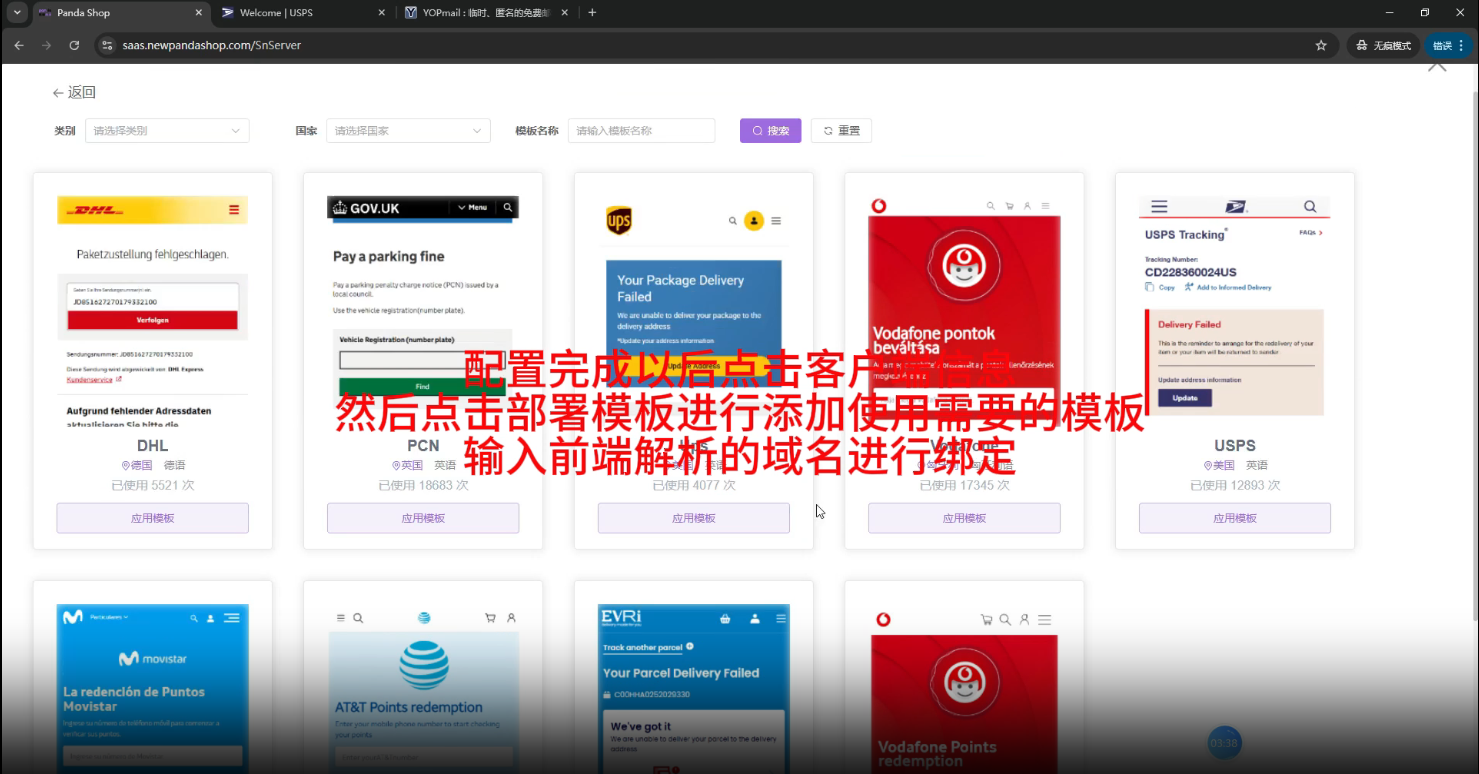
Multiple integrated templates that the operator can use for smishing were identified, including but not limited to:
- AT&T
- DHL
- Evri
- UPS
- USPS
- Movistar
- The UK government website for paying parking fines
- Vodafone
Examples:
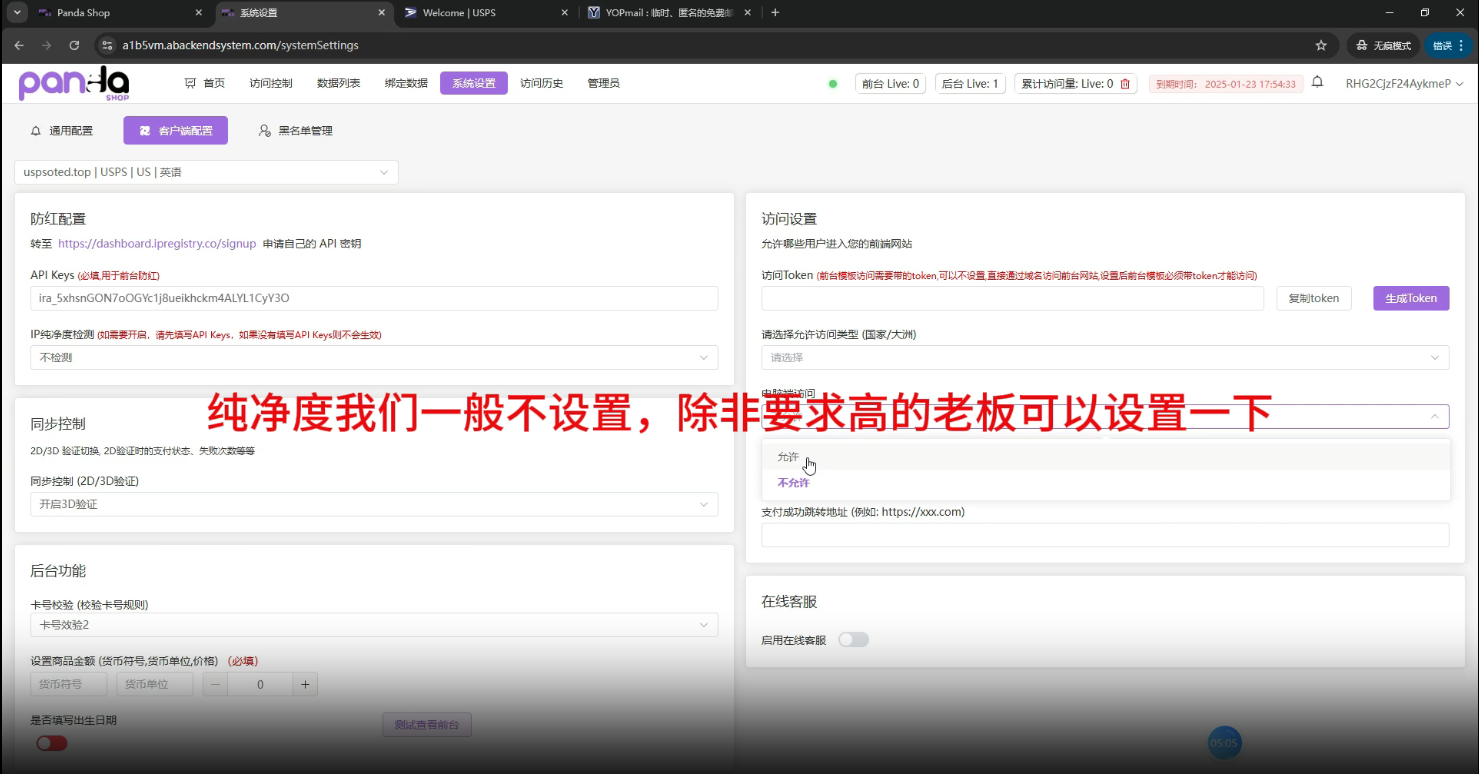
The actors used an API key from a legitimate IP reputation service called IP Registry Co. (https://ipregistry.co). This allows them to check if the victim is legitimate, not a search engine or antivirus bot, which may jeopardize their operations. By misusing IP reputation services, the actors protect their smishing kits from possible identification by cybersecurity researchers. This tactic is widely used by cybercriminals involved in Black SEO and malicious code distribution. It often helps them prevent flagging by anti-phishing and anti-scam solutions.
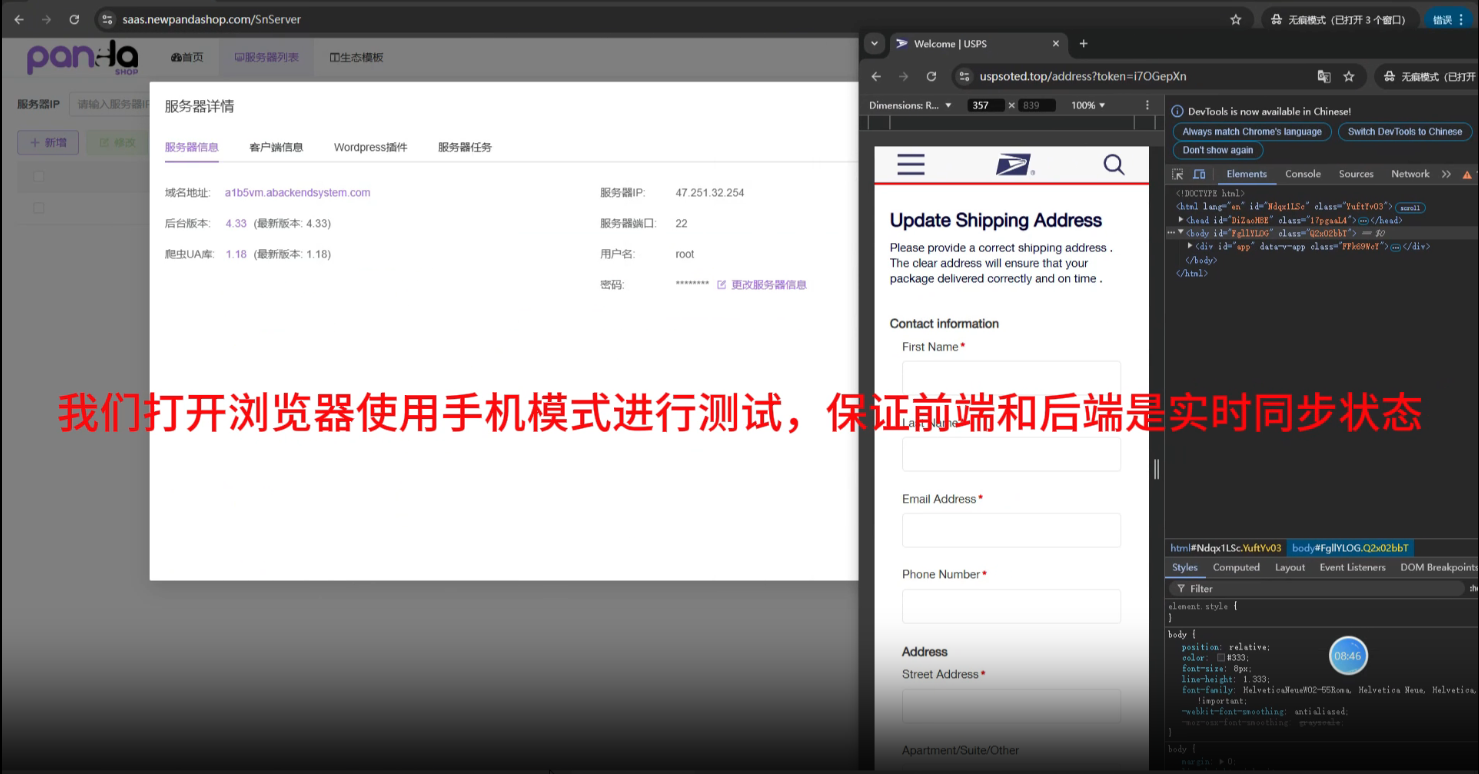
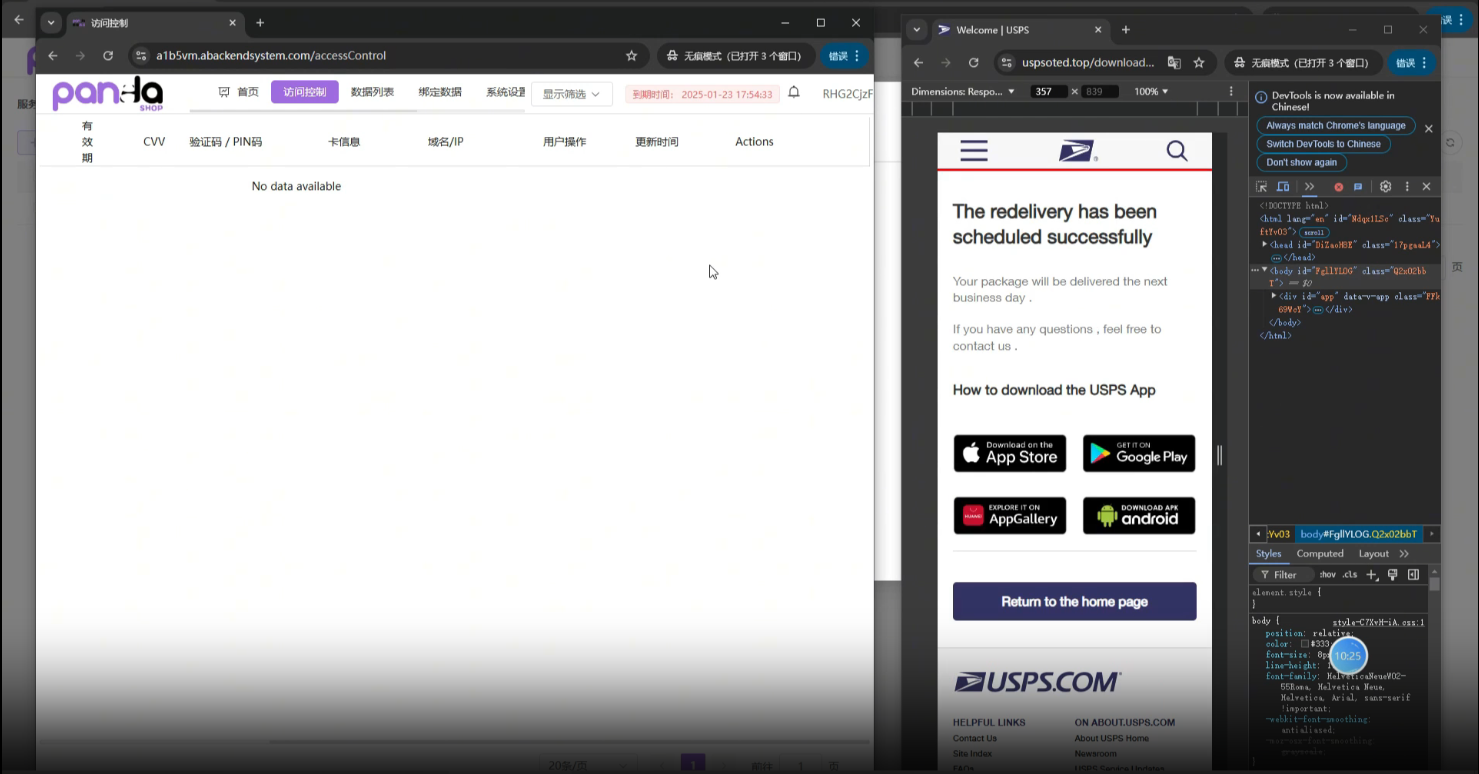
The identified smishing templates are customized for popular mobile platforms and browsers. When a victim opens such a page, it looks like they are visiting a legitimate USPS website, which sent a mobile notification requesting additional information to receive a parcel.
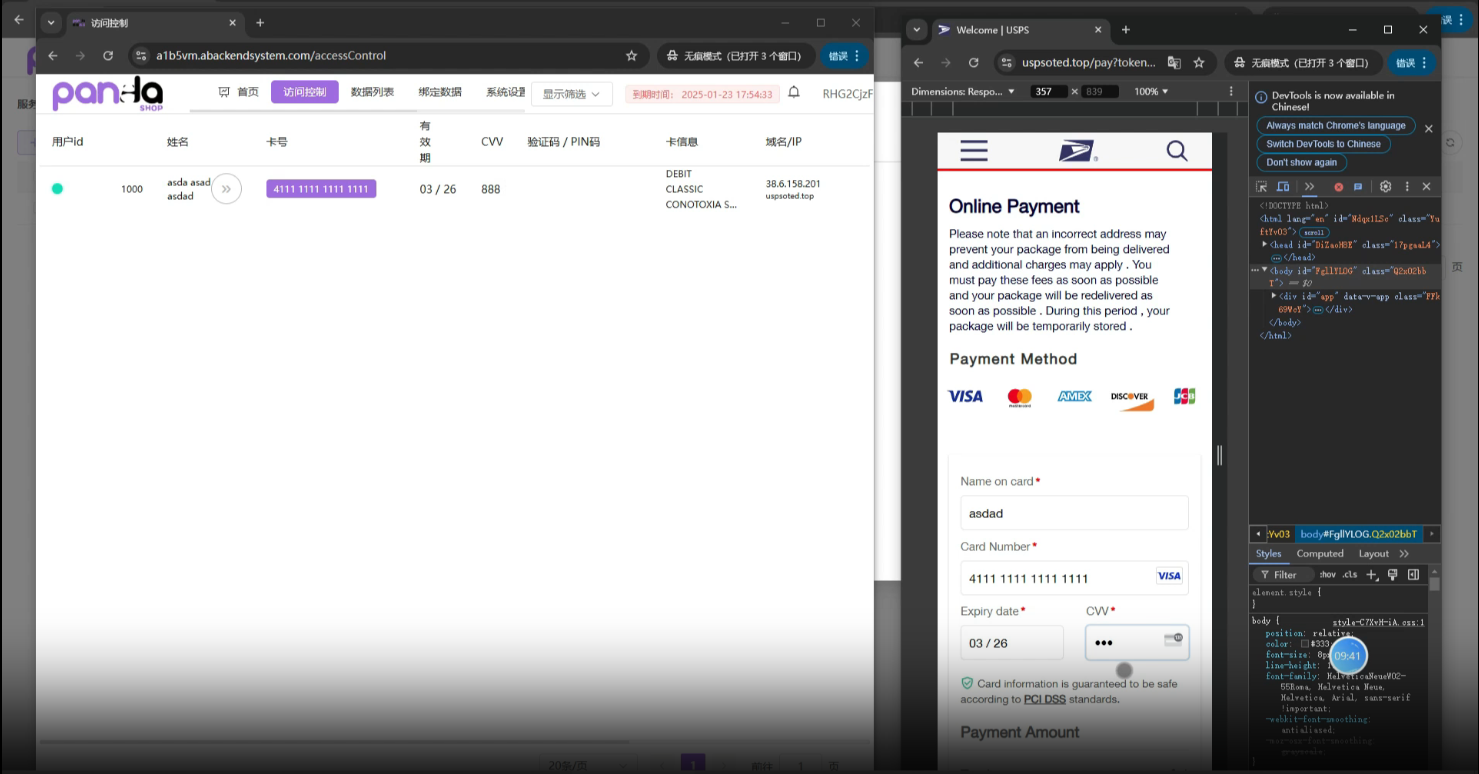
Once the victim provides the requested PII and credit card, it will be sent to Chinese cybercriminals. This type of fraud is probably one of the most rapidly developing targeting consumers.
Intercepted credit card data goes to underground carding shops and is sold to other cybercriminals.
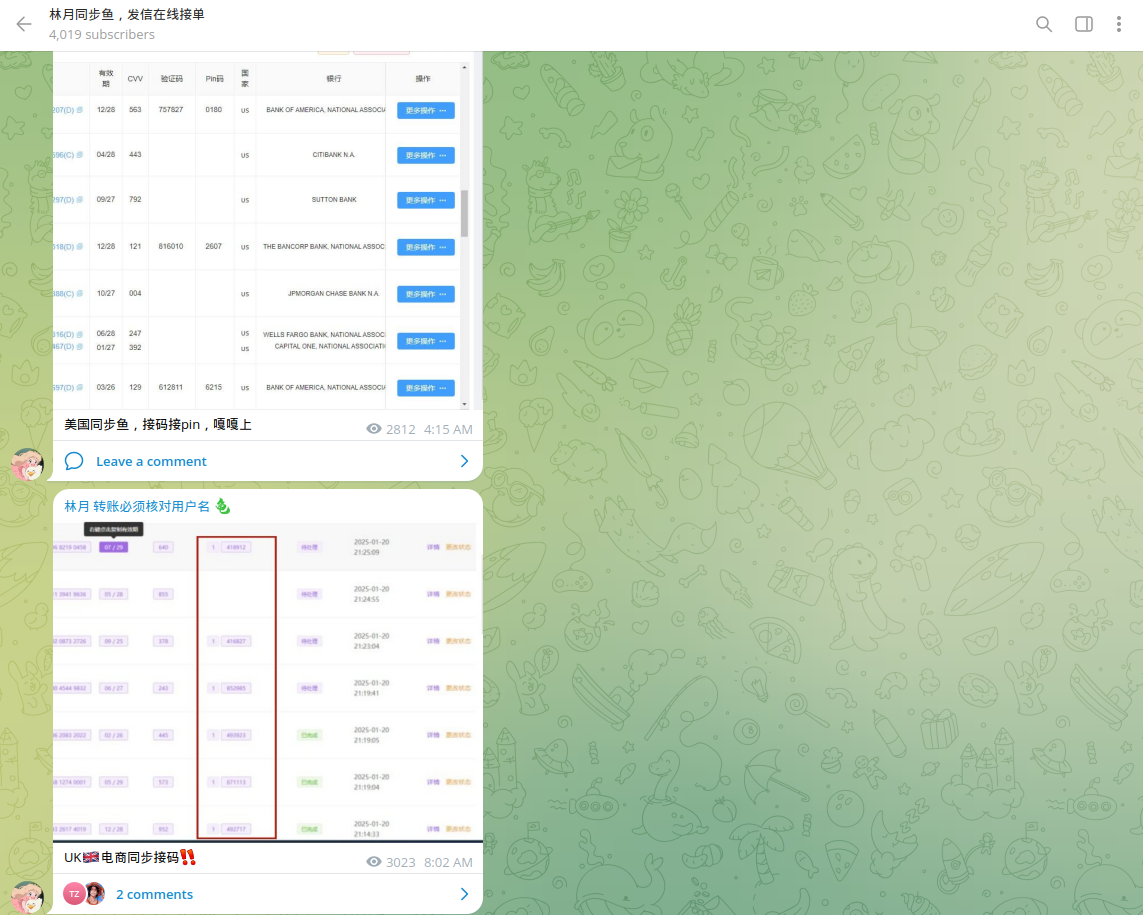
Resecurity observed chats in which threat actors targeted top US banks, including Bank of America, Citibank, JP Morgan Chase, Capital One, and many others, as well as UK financial institutions.
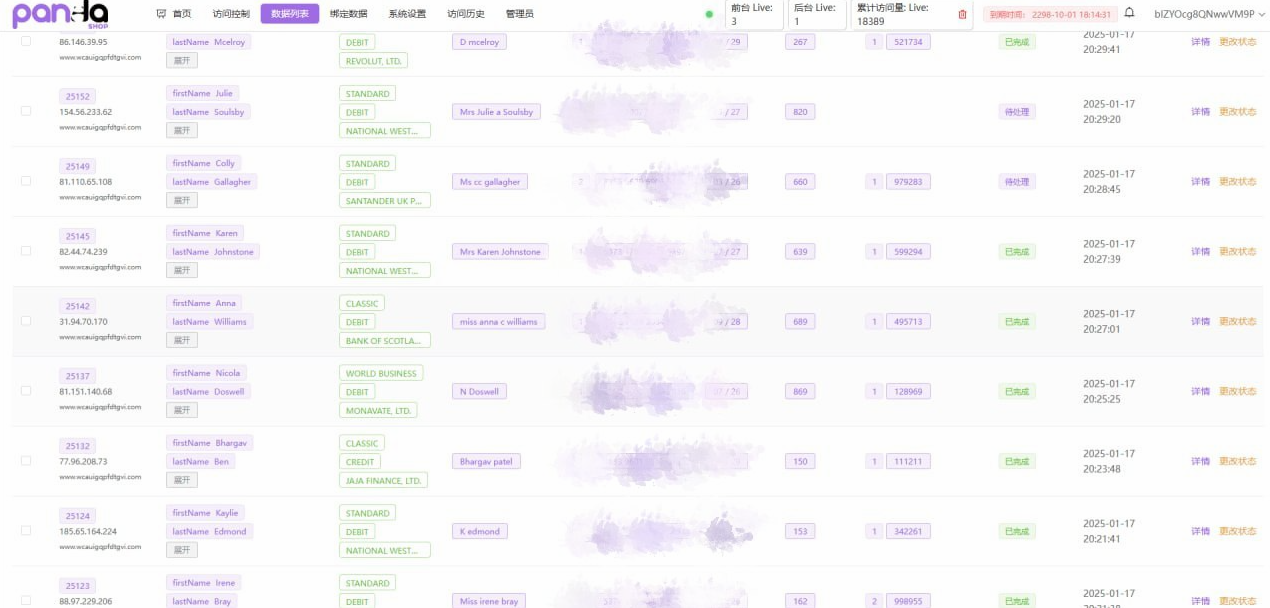
Collected compromised payment data is available via an interactive administration panel that allows users to review statistics and information about the victims.
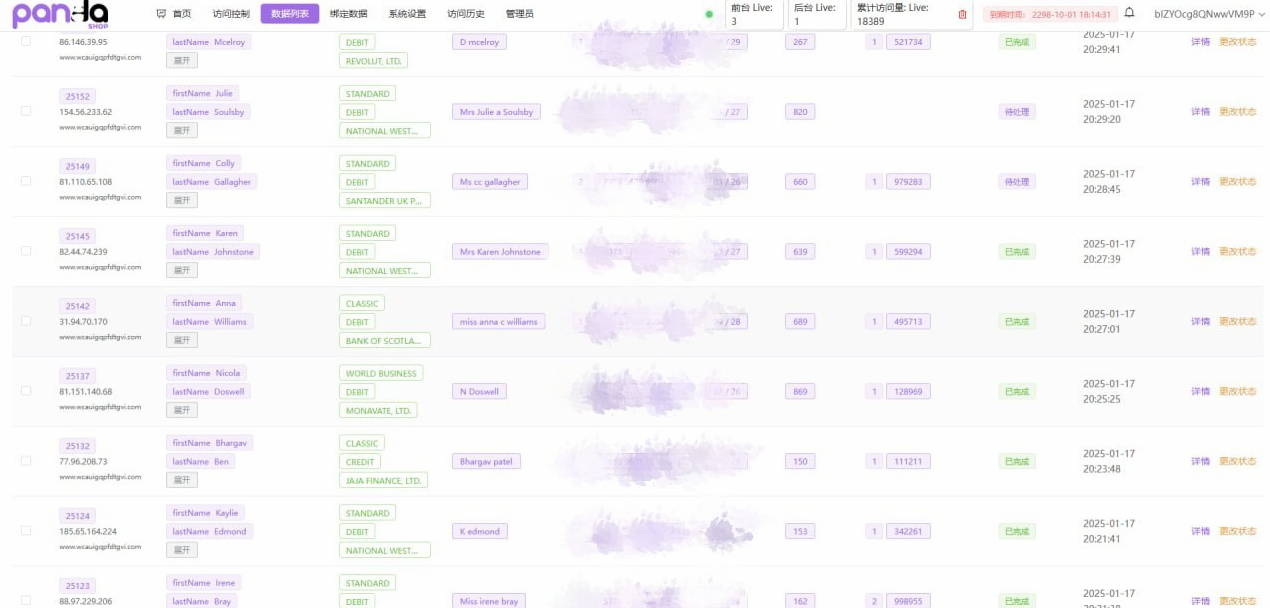
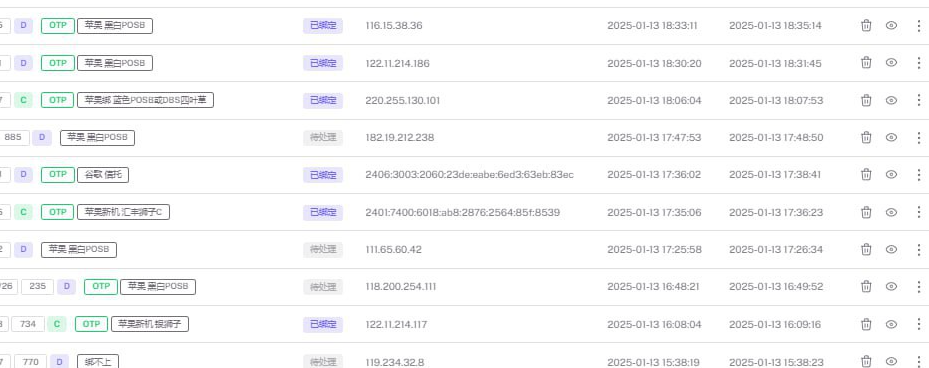
Similar to EvilProxy, the kit also supports OTP collection by establishing live sessions with the victim.
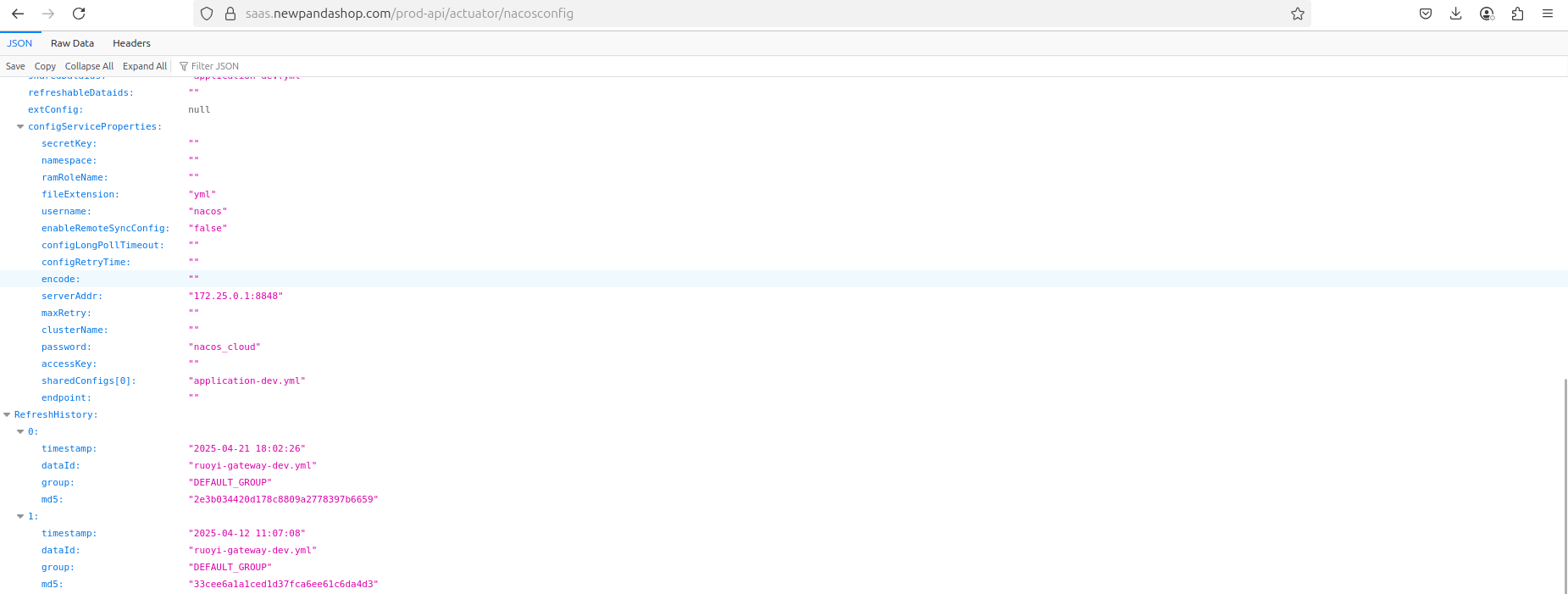
Resecurity identified an exposed ".env" file on the webserver managed by Panda Shop, which stores sensitive application configuration data (like database credentials, API keys, etc.). The settings contained a reference to NACOS (https://nacos.io/en/), a Chinese service management platform by Alibaba for building cloud-native applications.
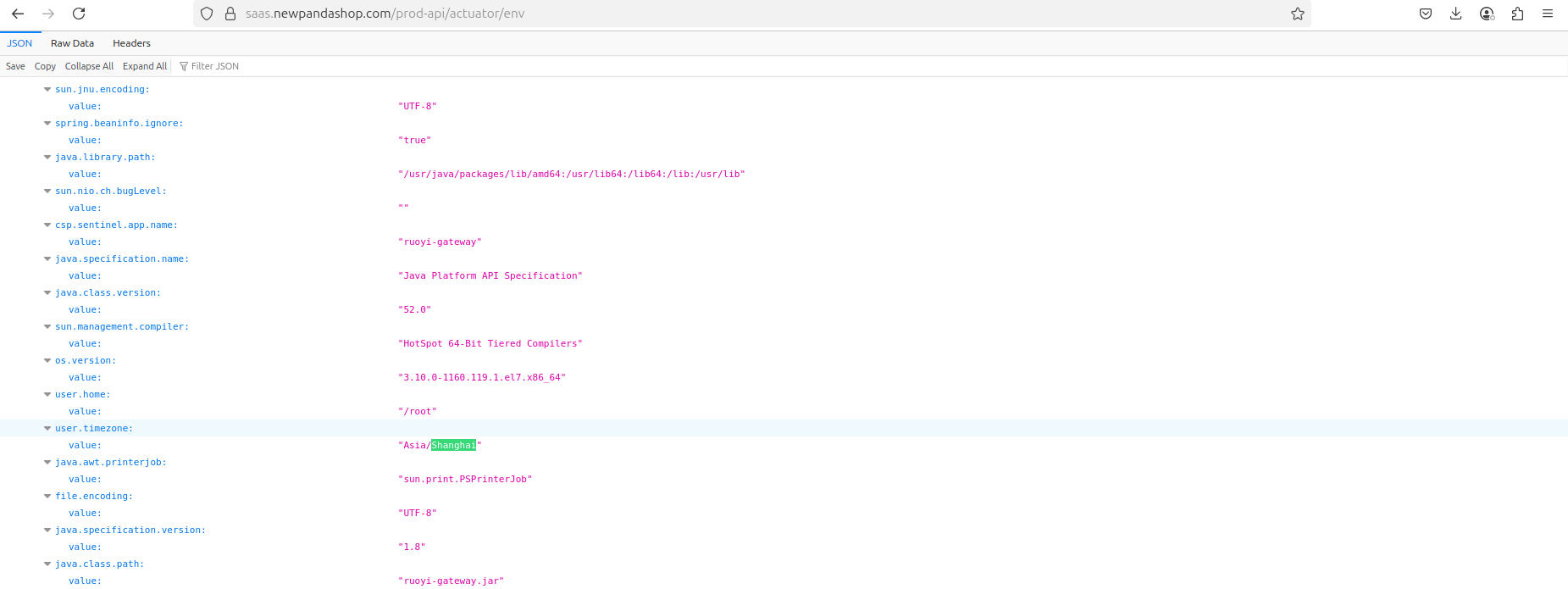
The time zone configured on the server was specified as Shanghai, confirming that the bad actors were located in China.
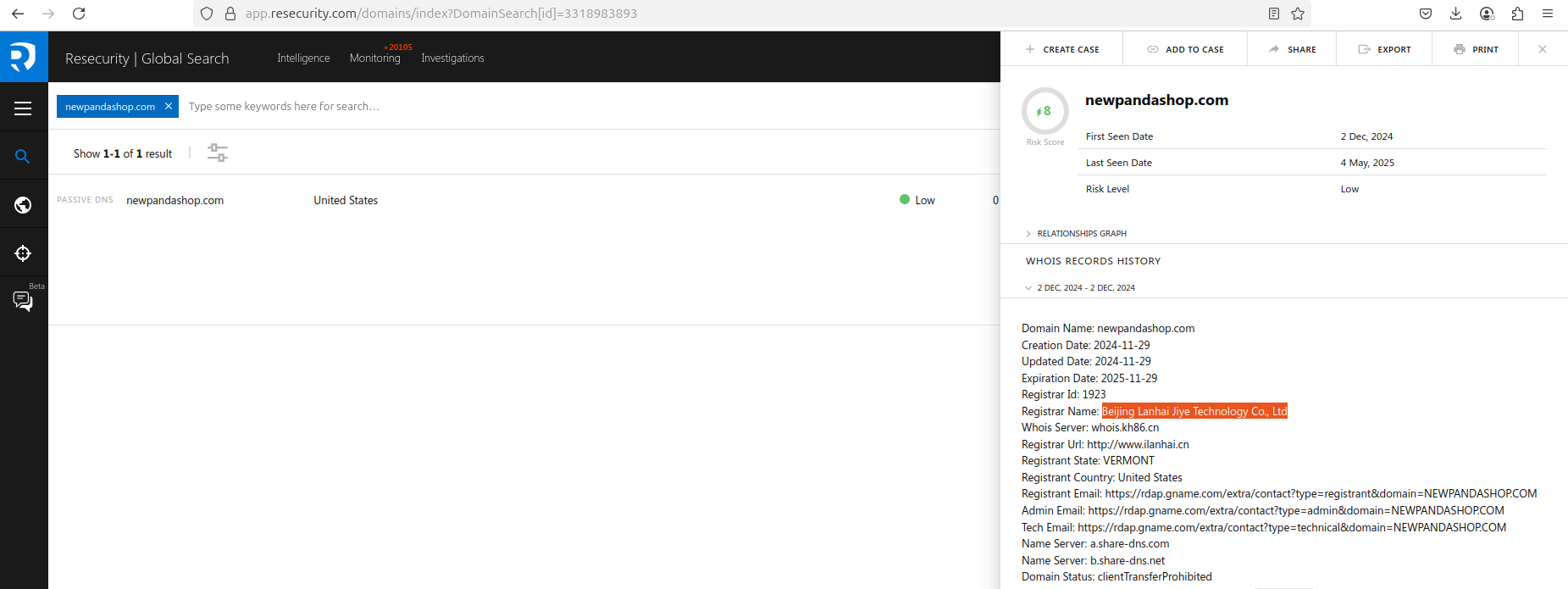
The domain name was registered on November 29, 2024 via Beijing Lanhai Jiye Technology Co., Ltd. Earlier, this Chinese company located in the Center of China Aviation International Exchange Building in Chengdu (Sichuan Province) has been accused of breaching registrar accreditation agreement by ICANN due to severe violations. In the letter, addressed to Li Yongmei by ICANN, the company was declared non-compliant in multiple areas. Ironically, last year, over 470 domain names involved in smishing campaigns impersonating Indian Post and targeting Indian consumers were registered via this company.
With moderate level of confidence, the members of Smishing Triad have overlap with Panda Shop, a rebranded version of their previous project.
Video Demonstration
Resecurity acquired an interactive video demonstrating the Panda Shop's functionality in practice. The quality of the smishing templates mimicking popular online services is impressive. This makes smishing campaigns easy, extremely effective, scalable, and affordable for cybercriminals.
Panda Shop is one of many smishing kits delivered in combination with "Crime-as-a-Service" offerings available in the Chinese underground ecosystem.
What is Android RCS?
Rich Communication Services (RCS) is a communication protocol designed to enhance the messaging experience beyond traditional SMS (Short Message Service) and MMS (Multimedia Messaging Service). Developed by the GSM Association and championed by Google, RCS allows users to send high-resolution images, videos, and larger files and utilize features like read receipts, typing indicators, and group chat functionalities. RCS is a modernized messaging standard that operates over cellular and Wi-Fi networks, making it more versatile than SMS/MMS, which are limited to cellular connections. It aims to provide a richer messaging experience similar to popular messaging apps like WhatsApp and iMessage, but integrated into the default messaging app on Android smartphones.
What is Apple iMessage?
iMessage is Apple's proprietary messaging service that allows users to send texts, photos, videos, and more between Apple devices (iPhones, iPads, Macs, etc.) and other devices over Wi-Fi or cellular data. iMessages are indicated by blue text bubbles, while messages sent via SMS/MMS appear in green bubbles. iMessage supports features like end-to-end encryption, read receipts, and typing indicators, making it a robust messaging platform for iMessage users.
Significance
The scale of global smishing activity generated by Chinese cybercriminals is impressive. The damages they generate could be estimated at tens to hundreds of millions of dollars for consumers and businesses. The spectrum of the crimes conducted due to smishing ranges from traditional carding and NFC-enabled fraud to money laundering chains, enabling fraudsters to process stolen funds. Based on Resecurity's engagements with financial institutions globally, this activity generates millions in losses annually.
Compared to wire fraud, which could be much larger, this activity is driven by the number of victims and the automation of illegal transactions. Unfortunately, since 2014, there has been a minimal number of arrests related to smishing. Most of them are related not to the main perpetrators behind the crime, but to money mules facilitating the second stage of operations at ATMs or POS merchants. However, this becomes unnecessary with NFC technology and the ability to organize their controlled merchant for further laundering registered in a money mule's name.
One of the latest efforts to combat smishing was undertaken by DHS HSI within the scope of Project Red Hook (Operation Doubletap), which focused on identifying actors involved in smishing and their associates. Nevertheless, while this helps to address the money mules’ issue, unfortunately, the root cause of smishing—cybercriminals residing in China—is not easily accessible by U.S. law enforcement. The geopolitical situation between China and the U.S. complicates timely legal action to contain this illegal activity, opening the doors for cybercrime and fraud at scale.

