PDFSIDER Malware - Exploitation of DLL Side-Loading for AV and EDR Evasion
Cyber Threat Intelligence
Overview
PDFSIDER is a newly identified malware variant distributed through DLL side-loading, designed to covertly deploy a backdoor with encrypted command-and-control (C2) capabilities. The malware uses a fake cryptbase.dll to bypass endpoint detection mechanisms.
The malware is identified as an Advanced Persistent Threat (APT), having characteristics commonly associated with APT tradecraft, including stealthy execution, anti-VM checks, and encrypted communications. PDFSIDER blends traditional cyber-espionage behaviors with modern remote-command functionality, enabling operators to gather system intelligence and remotely execute shell commands covertly.
The analyzed DLL contains a fully embedded Botan cryptographic library, configured for AES-256-GCM authenticated encryption - a strong indicator that the threat actors employ secure and structured C2 protocols. Once loaded, the malware provides attackers with an interactive, hidden command shell and can exfiltrate command output through its encrypted channel.
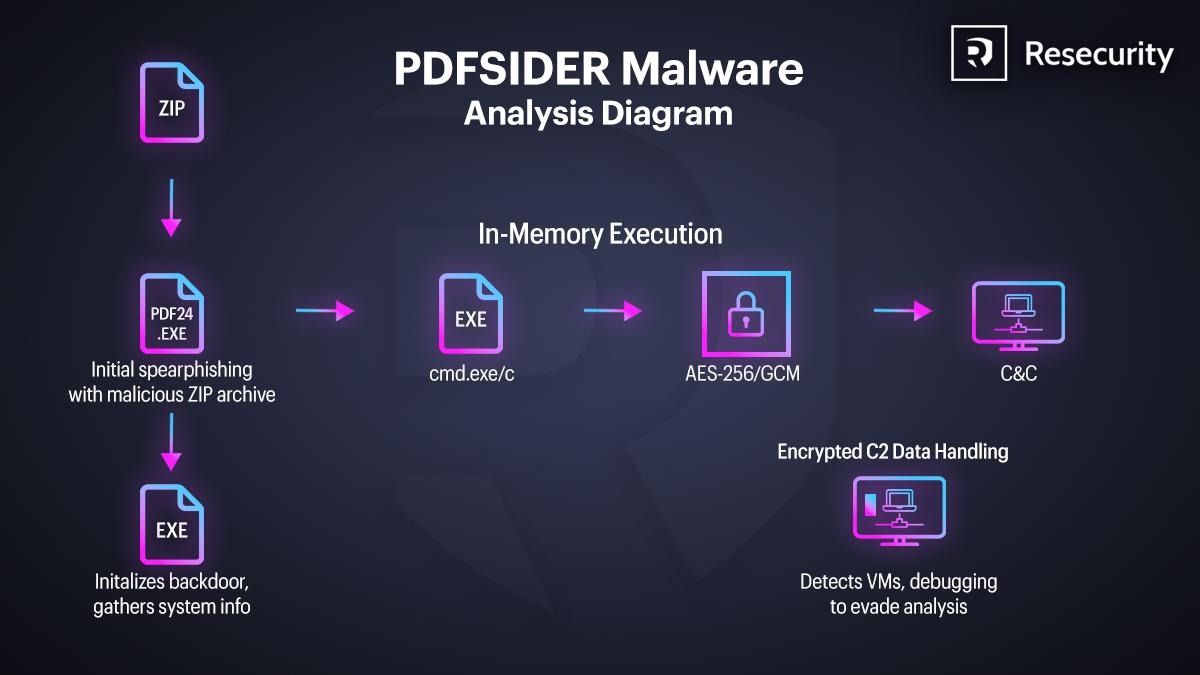
This report outlines the malware’s technical components, execution workflow, evasion mechanisms, and key indicators to support detection and response efforts.
Technical Details
1. Initial Infection and Delivery
PDFSIDER launched this campaign using spear-phishing emails that directed victims to a ZIP archive attached to the message. The ZIP archive contains a legitimate EXE file, labeled 'PDF24 App.' PDF24 Creator is an application software by Miron Geek Software GmbH used for creating PDF files from any application and for converting files to the PDF format.
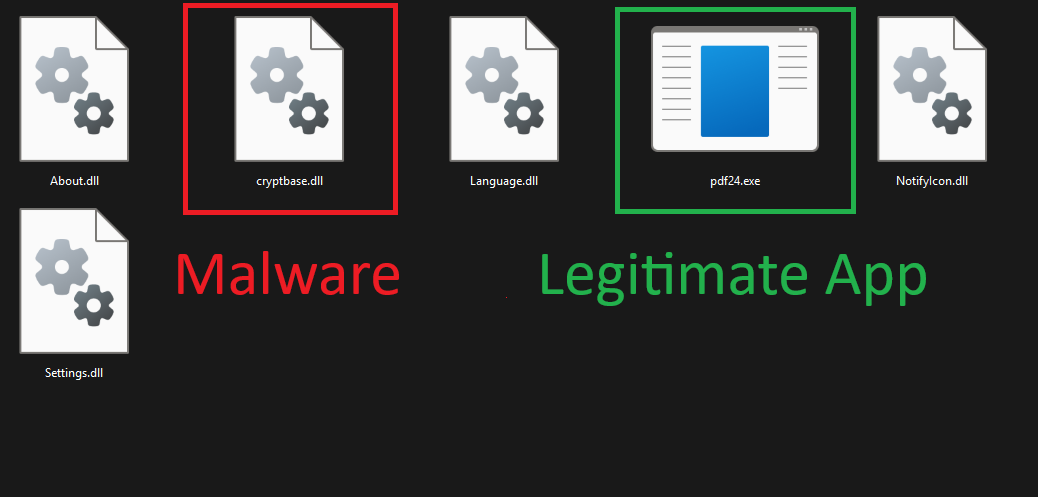
The infection chain begins when the victim opens the EXE file, which has no display when it runs on the machine; however, it will start to operate immediately on the machine when executed.
One of such certificates used for signing is still valid:
The EXE file has a legitimate signature; however, the PDF24 software has vulnerabilities that attackers were able to exploit to load this malware and bypass EDR systems effectively.
This is becoming more common nowadays due to the rise of AI coding, making it easier for cybercriminals to find vulnerable software and exploit it for their own purposes.
The malware appears to rely on DLL Side-Loading, a technique where a malicious DLL is placed next to a legitimate application that automatically loads it.
When the victim runs the legitimate program, The PDF24.exe loads the attacker’s DLL instead of the real system cryptbase.dll, granting code execution.
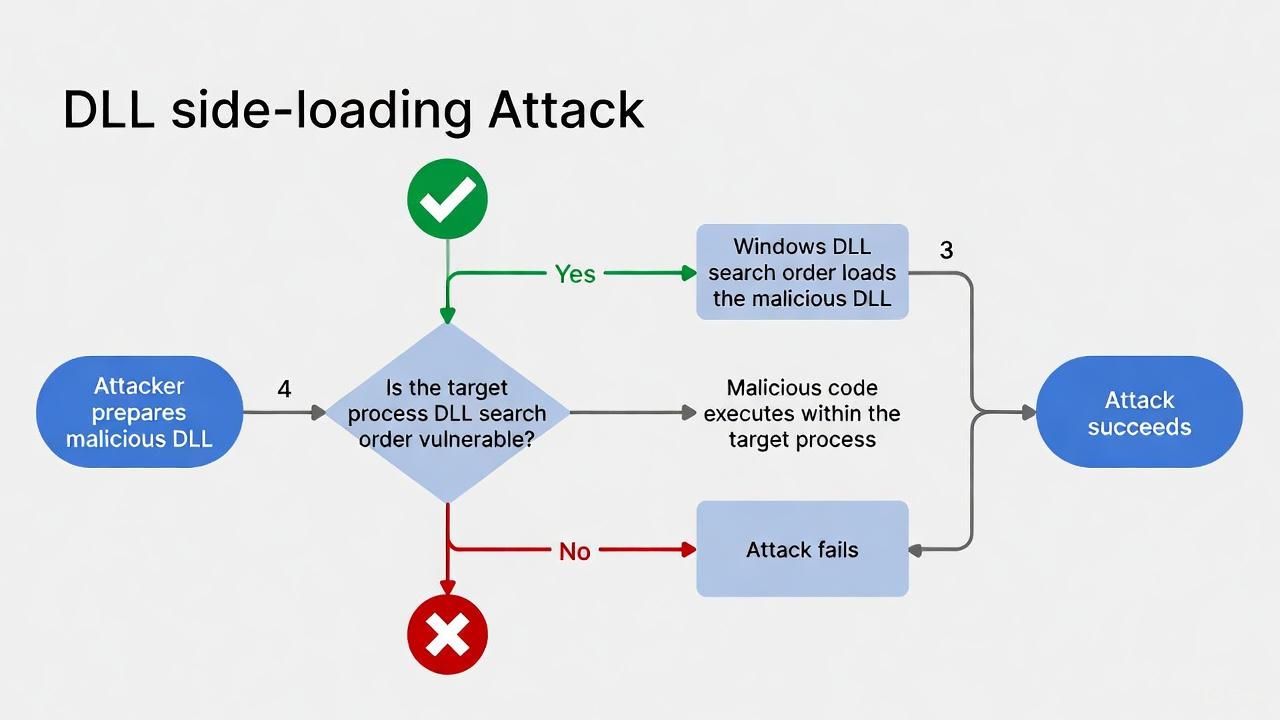
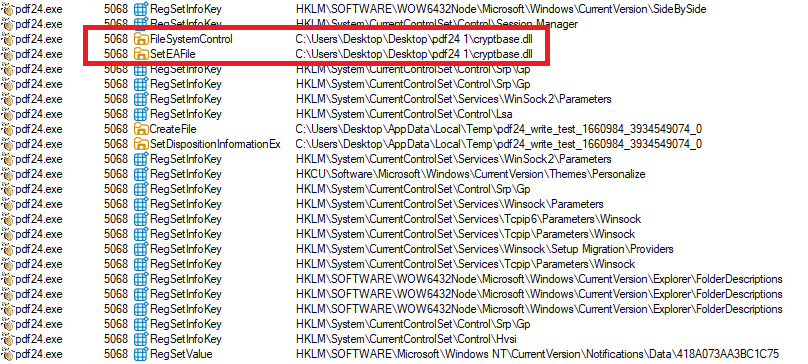
Once loaded, PDFSIDER initializes Winsock, sets up encrypted communications, gathers system information, and begins its backdoor loop.
2. In-Memory Execution
PDFSIDER operates primarily in memory, minimizing disk artifacts:
The malware provides full remote command execution upon launch, performing several actions. It creates anonymous pipes and constructs a command string using cmd.exe /C <attacker-supplied command>.
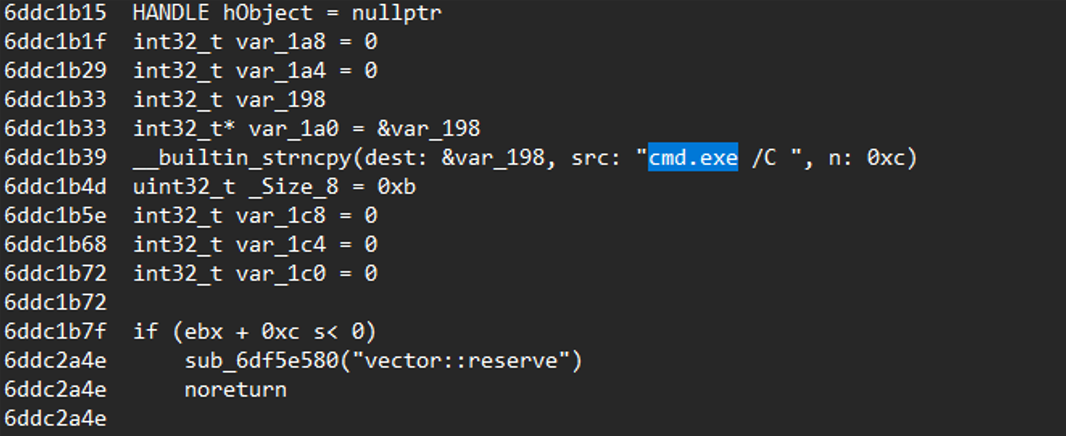
This command is launched with the CREATE_NO_WINDOW flag, ensuring no visible console appears.
The malware then extracts all information from your system, creates a unique ID from your system, and transmits the output back to the attacker.
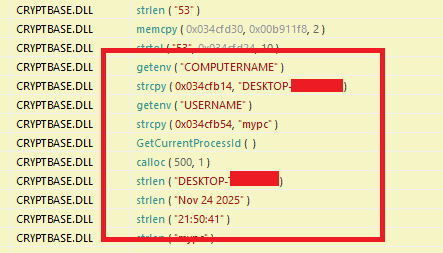
2.2 Encrypted C2 Data Handling
The malware utilizes the Botan 3.0.0 cryptographic library for encryption, incorporating several key components such as AES-256/GCM, GHASH, and checks for GCM tag failures.
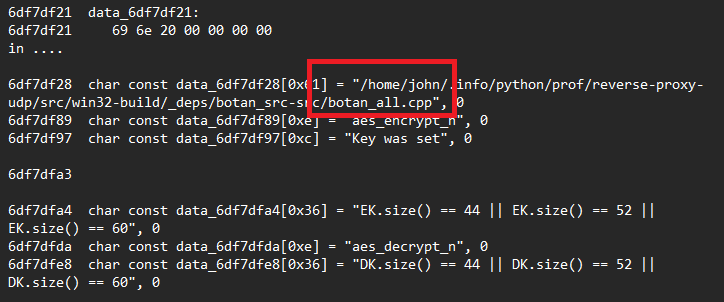
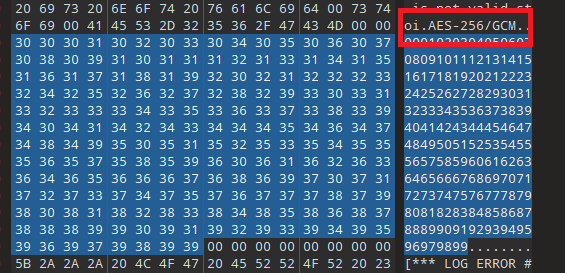
This strongly suggests that all inbound and outbound data handled by the malware is decrypted in memory, ensuring it is never written to disk. The data is also authenticated using AEAD (Authenticated Encryption with Associated Data) in GCM mode, providing a high level of security. This type of cryptographic implementation is typical of remote shell malware used in targeted attacks, where maintaining the integrity and confidentiality of communications is critical.
3. Anti-VM Technology
PDFSIDER features a multi-stage environment validation routine designed to detect sandboxes, virtual machines (VMs), and analysis labs. The malware uses the GlobalMemoryStatusEx function to assess the system's total RAM, with low-RAM systems (commonly associated with sandboxes or virtual environments) triggering an early exit.
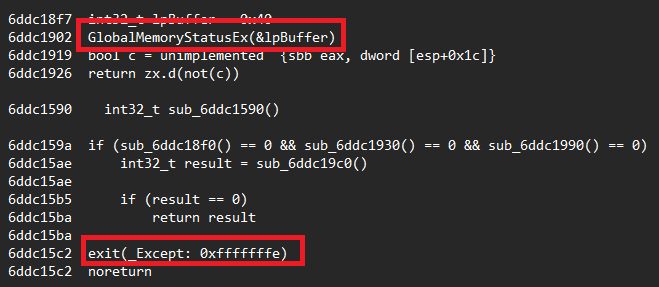
Additionally, it includes checks for the presence of a debugger, further ensuring that the malware avoids execution in a controlled or monitored environment.
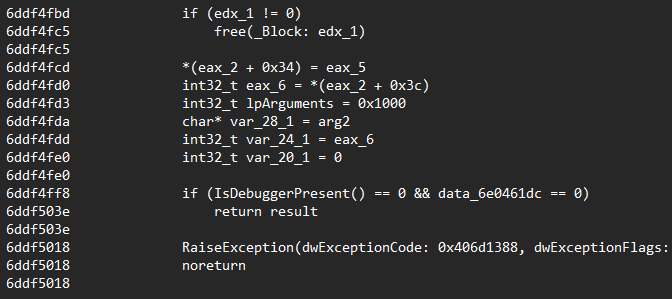
During our investigation, we discovered that the hackers leased a VPS server from the following company and set up a C&C server that sent the encrypted data to DNS port 53 at the specified location, which was used to exfiltrate compromised data.
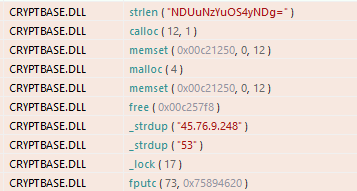
PDFSIDER is a robust and stealthy backdoor designed for long-term covert access, flexible remote command execution, and encrypted communications - aligning more with espionage tradecraft than financially motivated malware.
4. Decoy
Threat actors may leverage various decoys to lure victims into opening malicious documents. In one of the recent episodes of the same campaign, the actor also used a fake document designed to appear as if authored by the PLA Intelligence Bureau of the Joint Staff Department (中央军委联合参谋部情报局).
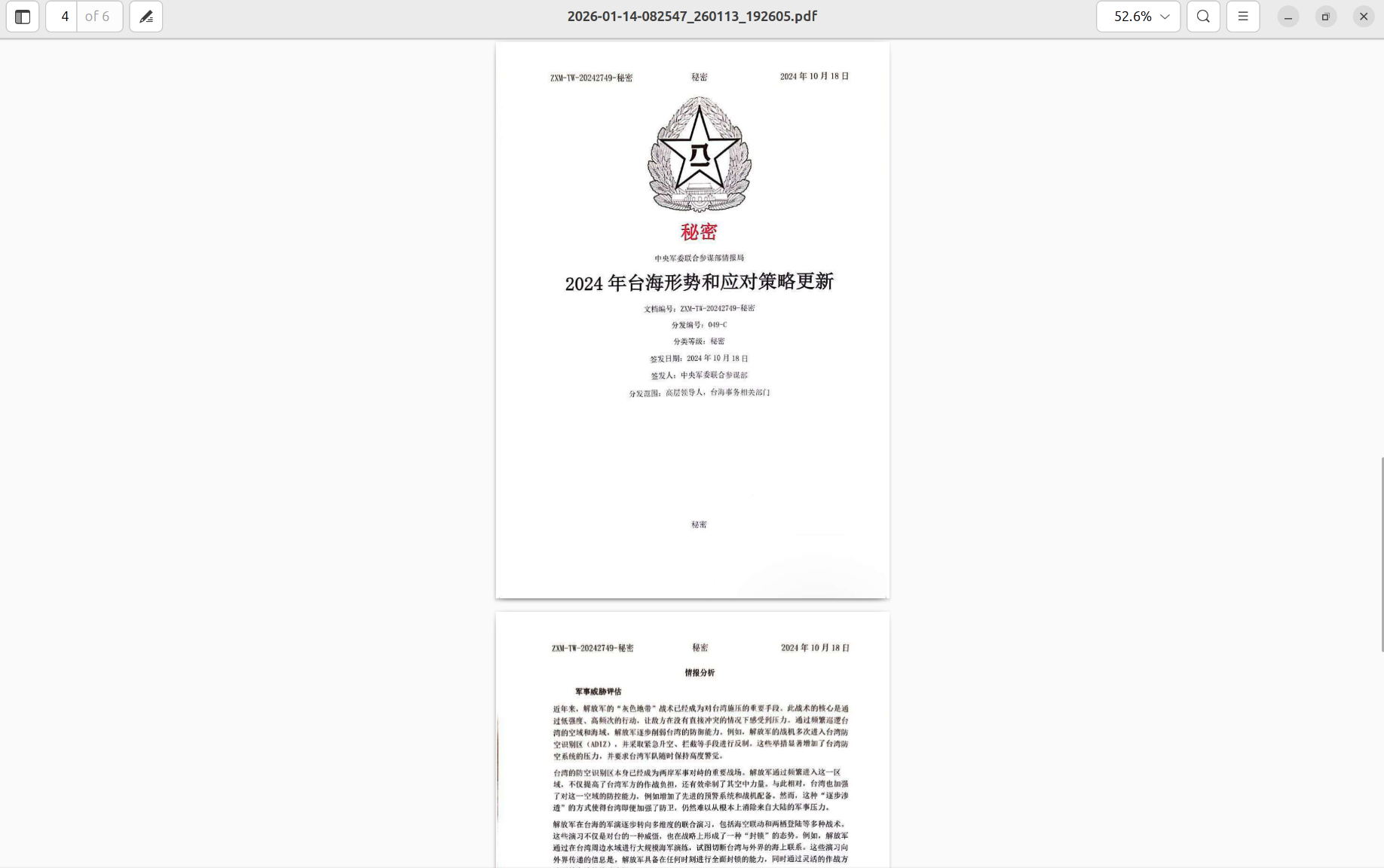
Notably, the majority of artifacts identified from the PDFSIDER campaign evade popular AV/EDR solutions. Currently, Resecurity interprets PDFSIDER as a tradecraft used in targeted attacks rather than mass-scale delivery.
Indicators of Compromise (IOCs)
| File Name | MD5 Hash | Status |
|---|---|---|
| About.dll | e0e674ec74d323e0588973aae901b5d2 | Clean |
| Cryptbase.dll | 298cbfc6a5f6fa041581233278af9394 | Malicious |
| Language.dll | 80e4a29270b828c1f97d9cde9475fcbd | Clean |
| NotifyIcon.dll | 96ff508f9be007062b1770691f489e62 | Clean |
| Pdf24.exe | a32dc85eee2e1a579199050cd1941e1d | Clean |
| Settings.dll | 9f9dd5a432b4dde2160c7a7170e0d069 | Clean |
C2 IPs:
- 45.76.9.248
MITRE ATT&CK Mapping
| Tactic | Technique | Mapping to PDFSIDER |
|---|---|---|
| Initial Access | T1574.002 - DLL Side-Loading | Malicious cryptbase.dll hijacks legitimate applications. |
| Execution | T1059.003 - Windows Command Shell | Executes hidden cmd.exe /C commands. |
| T1204 - User Execution | User must run the parent executable that loads the DLL. | |
| Defense Evasion | T1497 - Virtualization/Sandbox Evasion | CPU, RAM, timing, VHD boot checks. |
| T1622 - Debugger Evasion | Uses IsDebuggerPresent. |
|
| Discovery | T1082 - System Information Discovery | Collects username, computer name, PID. |
| Command & Control | T1095 - Non-Application Layer Protocol | Custom Winsock C2 with AES-GCM. |
| T1041 - Exfiltration Over C2 Channel | Sends captured command output over encrypted channel. | |
| Execution | T1106 - Native API | Uses low-level Win32 APIs for pipe and process control. |
Significance
Resecurity has learned about PDFSIDER during an investigation of a network intrusion attempt that was successfully prevented by a Fortune 100 corporation. The threat actor contacted their staff, impersonating technical support, and used social engineering tactics with QuickAssist in an attempt to gain remote access to their endpoint.
Considering DLL sideloading technique, this attack vector can be effectively exploited by advanced actors to bypass antivirus (AV) and endpoint detection and response (EDR) systems. According to our HUNTER team, PDFSIDER is already being actively used by several ransomware actors as a payload delivery method.
Resecurity may outline a continuing trend of targeted spear-phishing, favoring reliable execution techniques such as DLL sideloading over exploit-based initial access. For example, one of the recent malware campaigns identified by Acronis, targeting the U.S. government and attributed to LOTUSLITE, leveraged such a vector combined with geopolitical narratives between the United States and Venezuela as thematic lures. Infrastructure analysis and execution patterns show a moderate-confidence overlap with Mustang Panda tradecraft, including delivery style, loader–DLL separation, and infrastructure usage.
In another campaign identified by Trellix, DLL sideloading was used to distribute a wide assortment of malware, such as Agent Tesla, CryptBot, Formbook, Lumma Stealer, Vidar Stealer, Remcos RAT, Quasar RAT, DCRat, and XWorm. DLL sideloading vulnerability was exploited in a legitimate binary associated with the open-source c-ares library to bypass security controls and deliver a broad range of commodity trojans and stealers.
Update
No patch was available at the time of the malware distribution and active exploitation. One of the actively targeted versions is 11.13.2.0 and later. As of now (February 25, 2025), PDF24 software has released version 11.29.1, in which the same DLL sideloading with cryptbase.dll has been patched. However, multiple other modules are still vulnerable to the same technique.

