Paraguay is Being Targeted by Cybercriminals - 7.4 Million Citizen Records for Sale
Cyber Threat Intelligence

The identified data breach involves 7.4 million records containing personally identifiable information (PII) of Paraguayan citizens for sale on the dark web. As the threat actors aim to sell the data quickly, it is only a matter of time before this data is exploited to victimize users across Paraguay. Cybercriminals have offered information about all citizens of Paraguay for sale, demanding $7.4 million in ransom payments, $1 per citizen. A ransomware group is extorting the entire country in what is probably one of the most significant cybersecurity incidents in the nation's history, with a symbolic deadline - Friday, June 13, 2025.
The first reports about the country's cybersecurity issues appeared nearly two years ago, when one of the affected government systems was compromised, although no data has been publicly released. At that time, China was accused of engaging in malicious cyber activity targeting South America, with Paraguay specifically mentioned.
Flax Typhoon, a cyber-group linked to the Chinese state, was found to have infiltrated Paraguayan government networks, according to a joint statement from the Paraguayan Ministry of Information and Communication Technologies and the U.S. Embassy in Asunción. Flax Typhoon carried out an advanced persistent threat (APT), meaning a targeted and sustained cyberattack. The Chinese group utilized malware to infiltrate systems, extract sensitive information, and maintain a covert presence over extended periods. No data has been leaked for that event, and no victim organizations have been officially named as compromised.
Since then, the situation has not improved, as new cyberattacks have continued to occur. It turns out that this was not the only incident, but rather multiple large-scale data breaches affecting the entire population, with the most recent one happening just a few weeks ago. Notably, no official statement has been released to date, and the government has not notified the victims. Leaks impacting citizens on a country-wide scale increase the risk of financial fraud and identity theft and can be exploited in future disinformation and election interference campaigns.
Paraguay has lost data about the entire population, including their PII, which was exfiltrated from several different government information systems. Notably, in the ransom demand, the actors accuse the country's leadership of corruption and a lack of attention to citizens' data protection. The actors positioned themselves as "mercenaries" - calling themselves "Cyber PMC" - and attacking government systems for profit. It is unclear whether a foreign state sponsors the actors and if cybercriminal motives purely drive their activity. Considering the previous attacks by China, this new development confirms the growing number of cyberattacks against Paraguay. These events, with a "hack-and-leak" narrative, could be interpreted as a landmark in known cybersecurity incidents today, by size and scale, as the entire country was extorted due to a massive data breach. The actors shared multiple samples and warned, "The time is ticking."
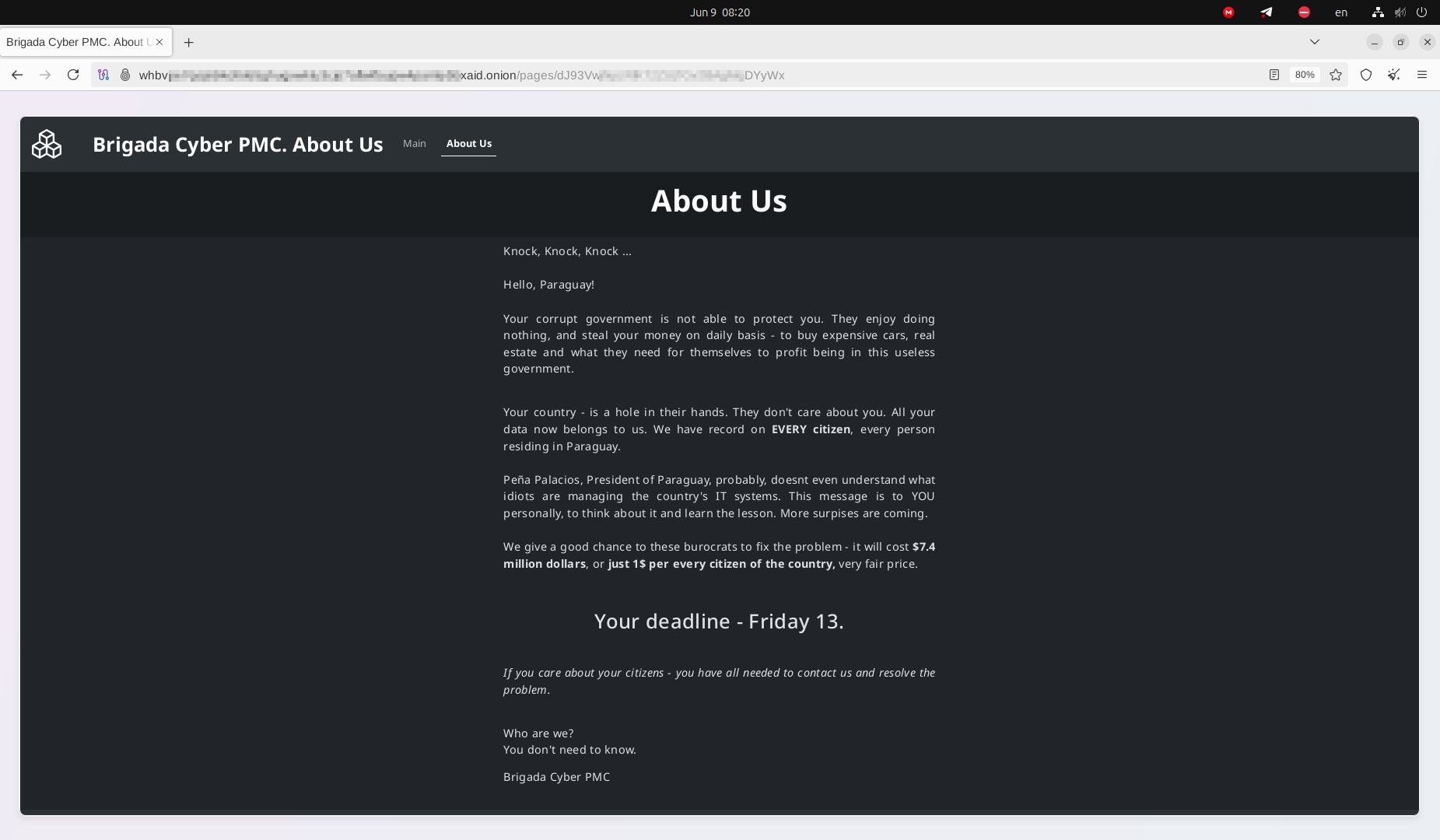
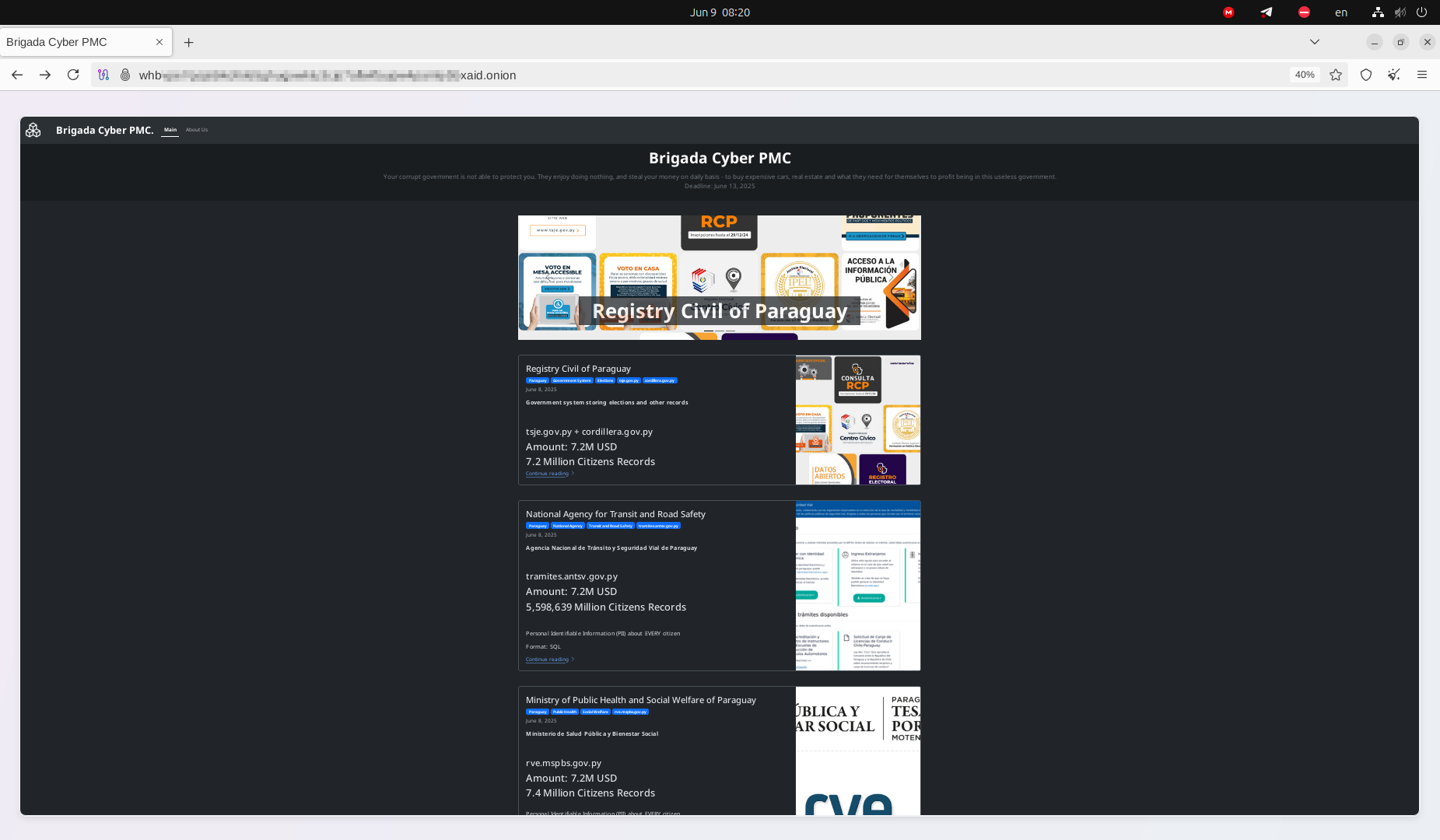
The Government of Paraguay declined to pay the ransom in the official statement and did not share any insights into how the information of 7.5 million citizens was stolen, offering only vague comments. A few days before the leak was published, the Twitter account of the President of Paraguay was hacked.
June 13, 2025 - The stolen data has been published on multiple underground forums. Interestingly, besides ZIP files containing databases, the actors also published a torrent file, enabling other Internet users to freely download citizens’ records using P2P networks. Notably, such tactics were previously used by LockBit 3.0. The group used P2P platforms to disseminate data leaks via torrent files to prevent takedowns. Why is this tactic significant? Firstly, even if the group's infrastructure is partially disrupted, RaaS operators can make stolen data accessible to a wide audience via decentralized torrent networks. Once downloaded, users in possession of these files automatically begin seeding them, meaning they become peer nodes in sharing this data within the torrent network. People who download these torrent-based ransomware links effectively become active participants in the data leak, similar to users sharing pirated movies or music. Stopping this activity poses a significant challenge, much like the difficulty the music, film, and TV industries face in combating content piracy through torrent trackers.
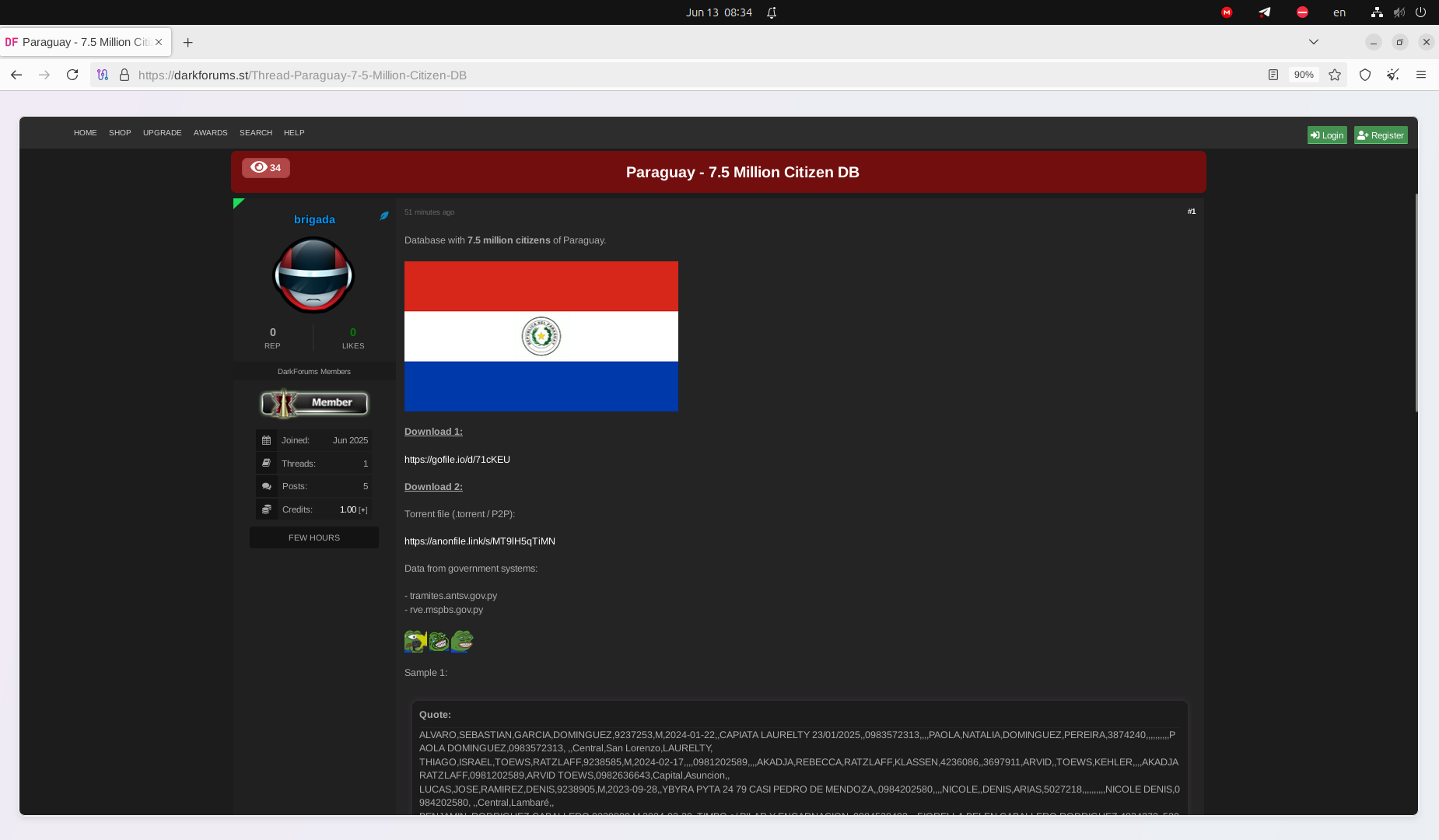
The data contains timestamps from 2025, and it had never been leaked publicly before. Considering that the data was stolen from several different sources, it is possible that the actors attempted to demonstrate the scale of the leak. Based on our current assessment, some of the impacted systems may have been compromised last year, but the stolen data from them has only now been leaked.
Introduction
May 28, 2025 — Resecurity identified a threat actor on the Dark Web offering a stolen database from a compromised government system, presumably containing over 7.4 million records with personal data of Paraguayan citizens. Notably, Paraguay's population is approximately 6.8-7.0 million, meaning the data breach may affect nearly every citizen of the country. The 7.4 million records for a population of 7.0 million account for some duplication, records for deceased individuals, and citizens who have migrated to Paraguay. The data breach of such scale is alarming and may indicate significant changes in the threat landscape targeting South America.
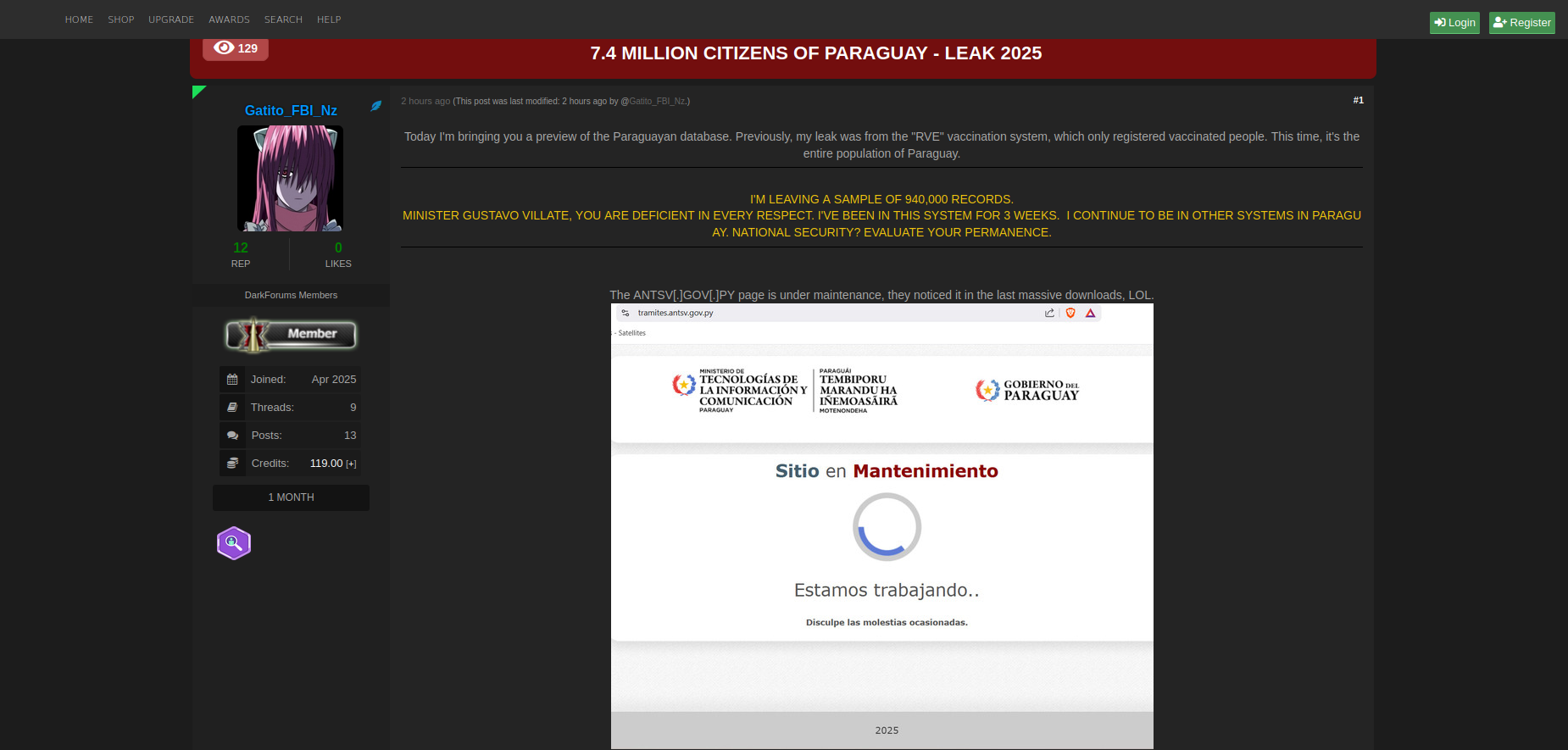
In his message, the threat actor Gatito_FBI_Nz addressed a personal threat to the Minister of Information and Communication Technologies of Paraguay, Gustavo Villate, claiming that they had gained unauthorized access to other government systems. The data breaches affecting the population may create significant implications for national security, establishing a precedent for cybercrime actors threatening the country's leadership.
Resecurity has informed CERT-PY, the national Computer Emergency Response Team for Paraguay responsible for responding to cybersecurity incidents within the country's networks and critical infrastructure, and relevant law enforcement authorities. Based on collected intelligence, the actor is responsible for cyberattacks against major government systems not only in Paraguay but also in multiple countries across South America.
Background
The actor, operating under the alias Gatito_FBI_Nz, has shared multiple samples containing evidence of compromised records with PII, and noted that he was able to hack into one of the government systems storing citizens' data. As proof, the actor shared a sample of 940,000 records for free, along with a screenshot of one of the official government web portals showing technical issues. It is likely that the actor aimed to provide additional context about the source of the data and indicated that he is willing to sell the entire dataset to others on the Dark Web.
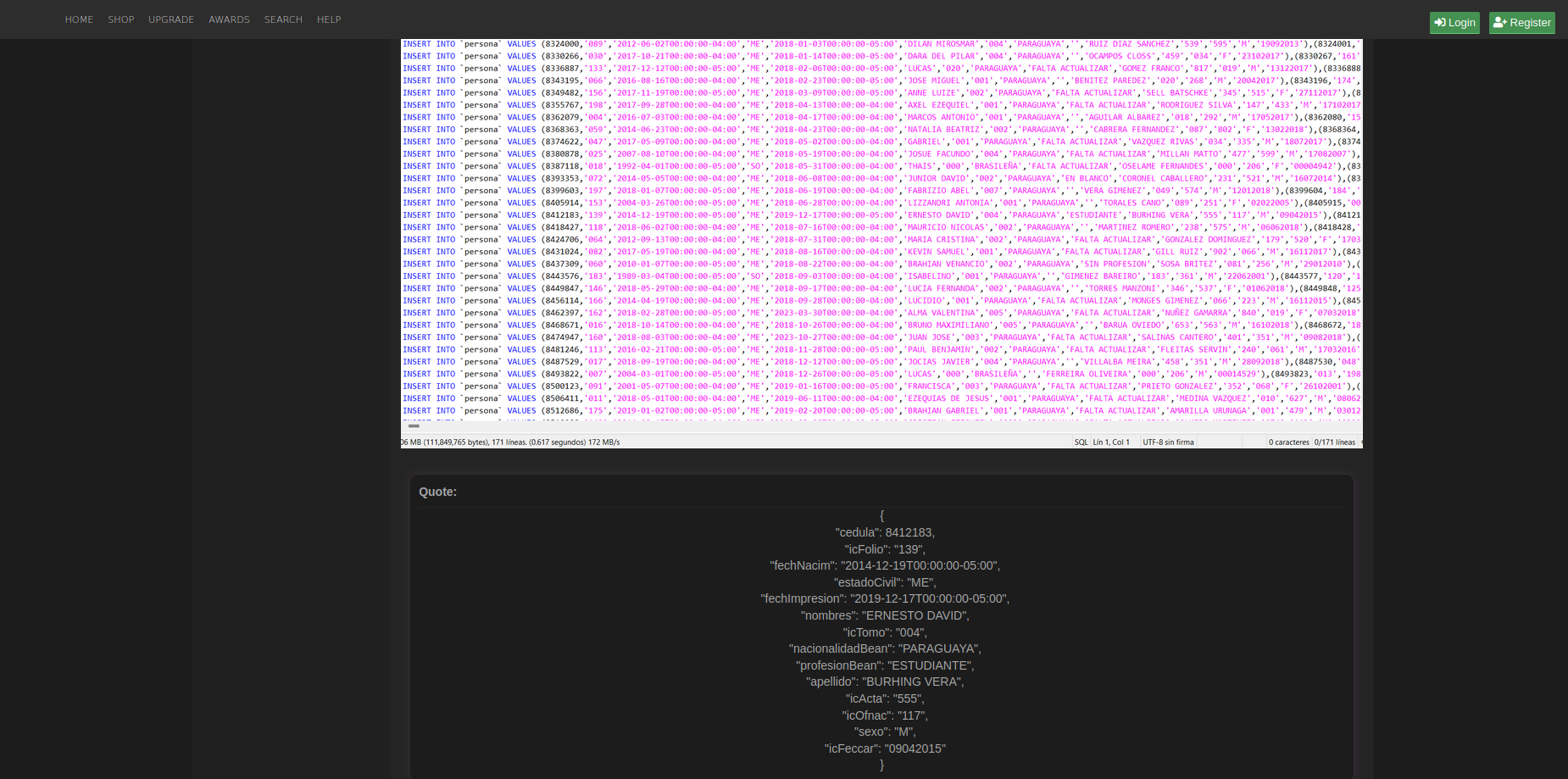
As of May 29, 2025, the website of the potentially impacted system (URL: https://tramites.antsv.gov.py), mentioned by the threat actor, has remained under maintenance without any additional information made available.

By May 30, 2025, the government portal had recovered and was back in operation, leaving many users unaware of what had happened.
What Exactly Has Been Breached?
There are at least two separate data breaches. What was particularly perplexing is that initially, the threat actor mentioned the 'RVE' vaccination system as the target of the cyberattack, which stores information about registered vaccinated citizens in the country.
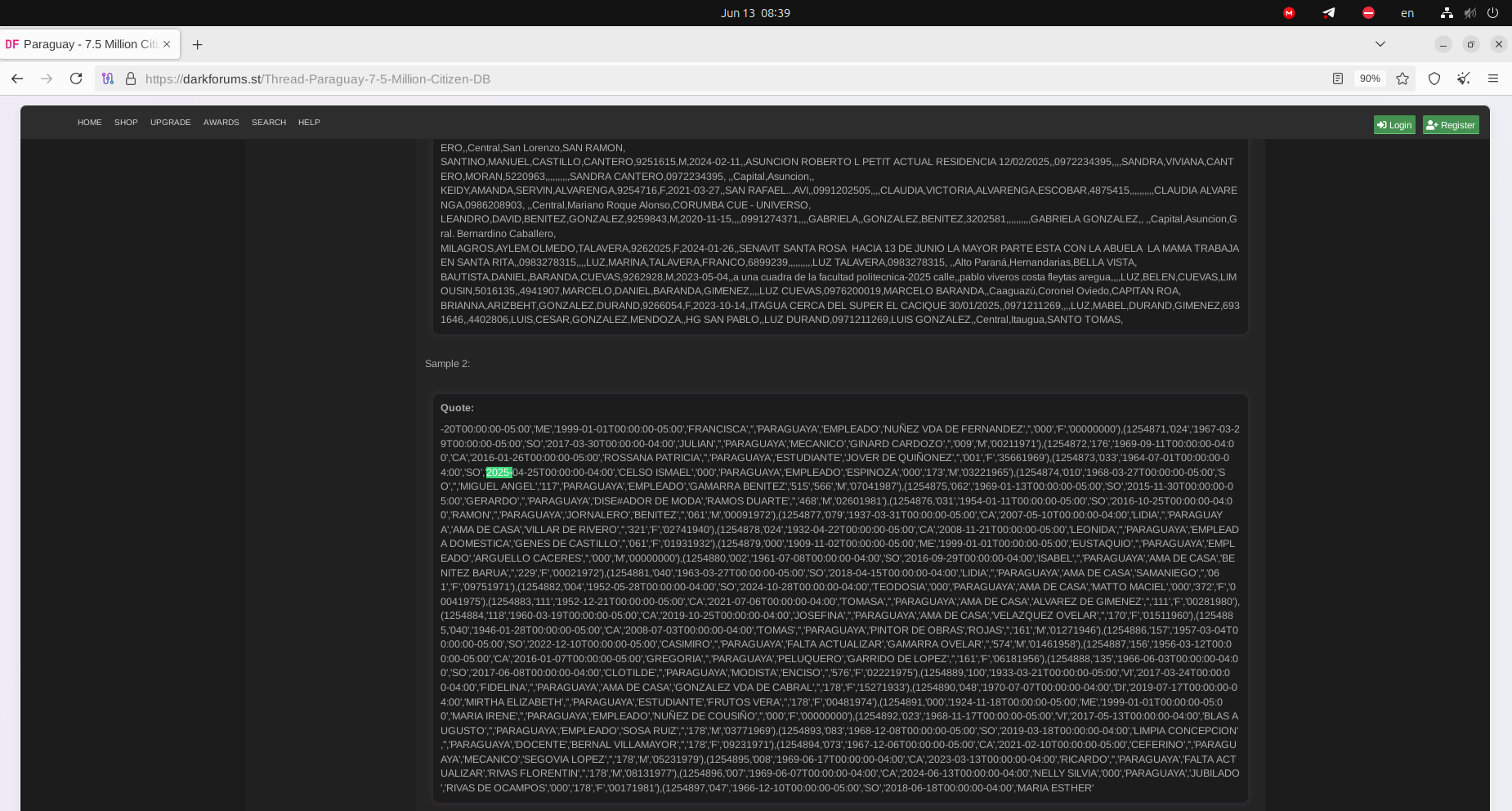
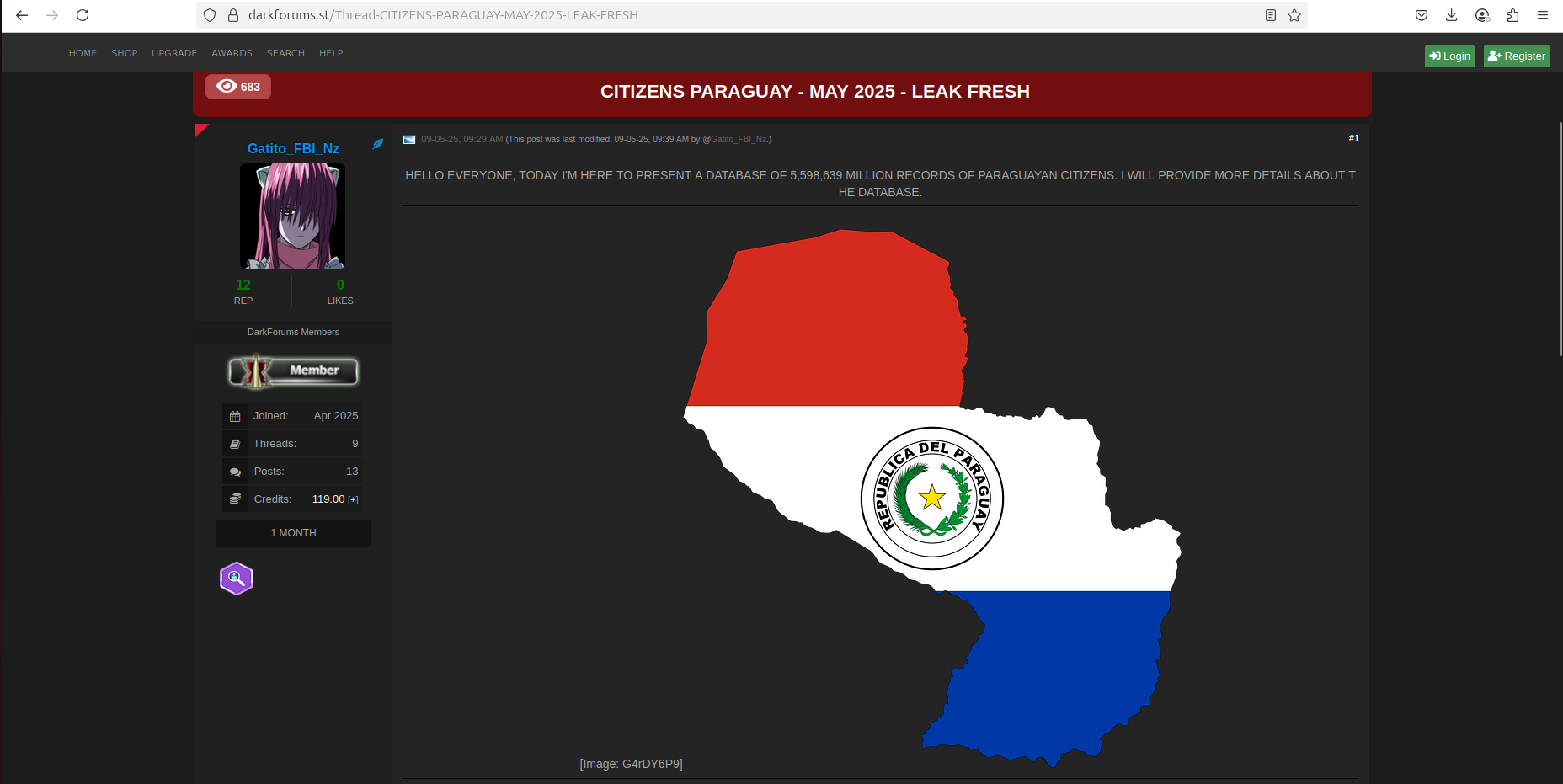
However, the most recent samples shared on the Dark Web originate from the Agencia Nacional de Tránsito y Seguridad Vial de Paraguay (National Agency for Transit and Road Safety of Paraguay). The samples observed by Resecurity contain PII information, including ID card numbers, internal folios, dates of birth, marital statuses, printing dates, names, volumes, nationalities, professions, surnames, certificates, and sexes.
"cedula": 8412183,
"icFolio": "139",
"dateOfBirth": "2014-12-19T00:00:00-05:00",
"maritalStatus": "ME",
"printDate": "2019-12-17T00:00:00-05:00",
"names": "ERNESTO DAVID",
"icTomo": "004",
"nationalityBean": "PARAGUAYAN",
"professionBean": "STUDENT",
"lastName": "BURHING VERA",
"icRegistry": "555",
"icOfNational": "117",
"sex": "M",
"icFeccar": "09042015"
Resecurity has reached out to multiple victims identified in the leaked dataset and received confirmation that the data is authentic. Previously, the victims did not receive any alerts indicating that their records could have been stolen as a result of a breach of the country's system. It is not clear whether the affected organizations were aware of the data breach or if the notification to the victims could be delayed. As of June 13, 2025, there were no official statements published shedding light on the incident or the circumstances of the data breach. Notably, at the beginning of May, the same actor was offering 5,598,639 records for sale originating from another unnamed government system in Paraguay.
The samples of records had utterly different structures, which likely indicated the data had been exfiltrated from a different system than the one previously disclosed.
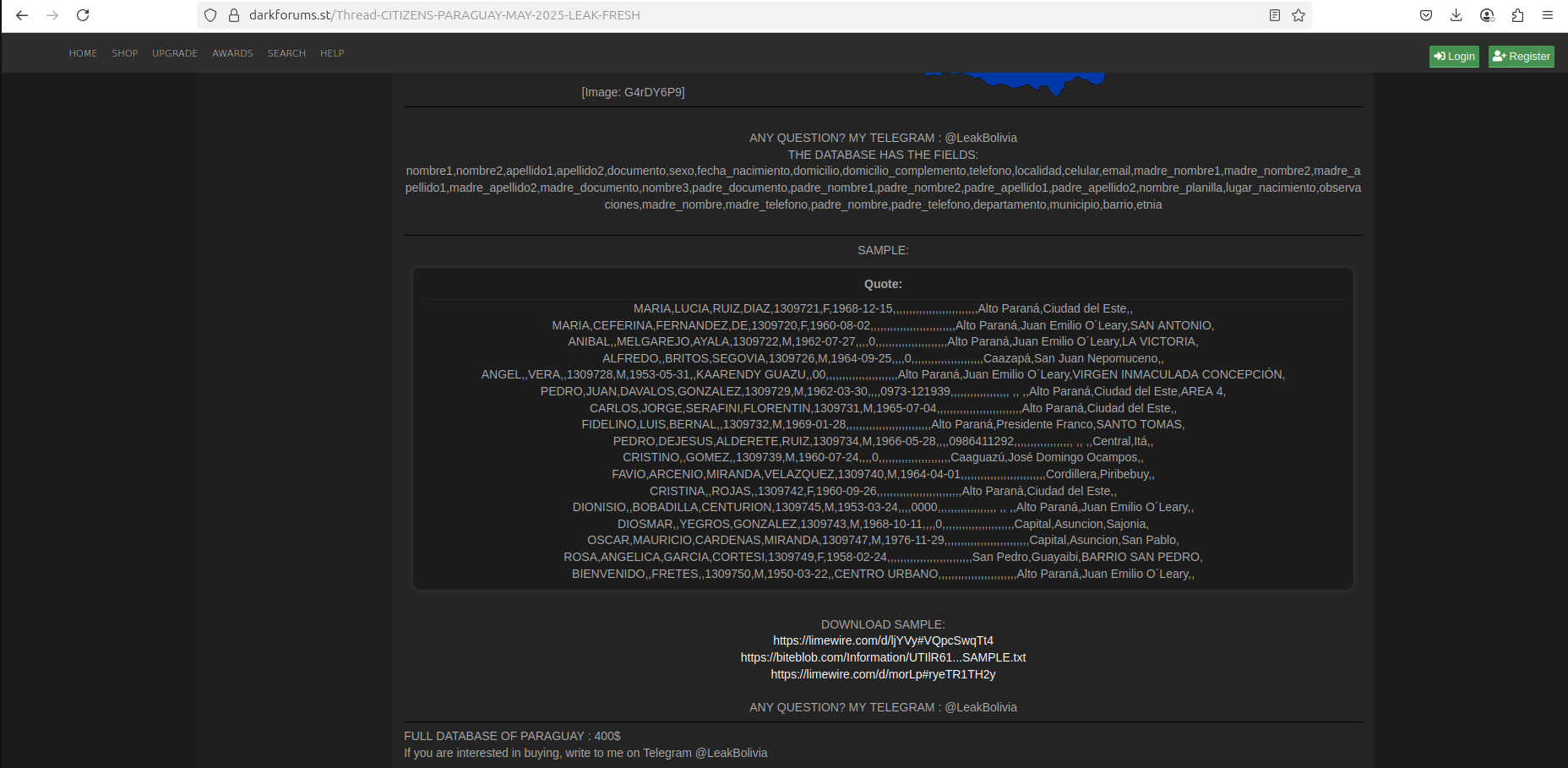
The main fields include:
nombre1
nombre2
apellido1
apellido2
documento
sexo
fecha_nacimiento
servicio_salud
domicilio
domicilio_complemento
telefono
localidad
celular email
madre_nombre1
madre_nombre2
madre_apellido1
madre_apellido2
madre_documento
nombre3 padre_documento padre_nombre1
padre_nombre2
padre_apellido1
padre_apellido2
nombre_planilla
lugar_nacimiento
observaciones
madre_nombre
madre_telefono
padre_nombre
padre_telefono
departamento
municipio
barrio
etnia
The most notable field, "servicio_salud" ("health service"), may indicate a specific relationship of this dataset to healthcare services. Via human intelligence (HUMINT), Resecurity was able to acquire additional artifacts from the actor, confirming that the data may have originated from one of the systems managed by the Ministry of Public Health and Social Welfare of Paraguay (Ministerio de Salud Publica y Bienestar Social).
The actor shared a screenshot of a successful login to the customer portal, showcasing the disclosed personal information. The URL shared by the actor (https://rve.mspbs.gov.py) was associated with a government information system that stores data about citizens who have been vaccinated against COVID-19.

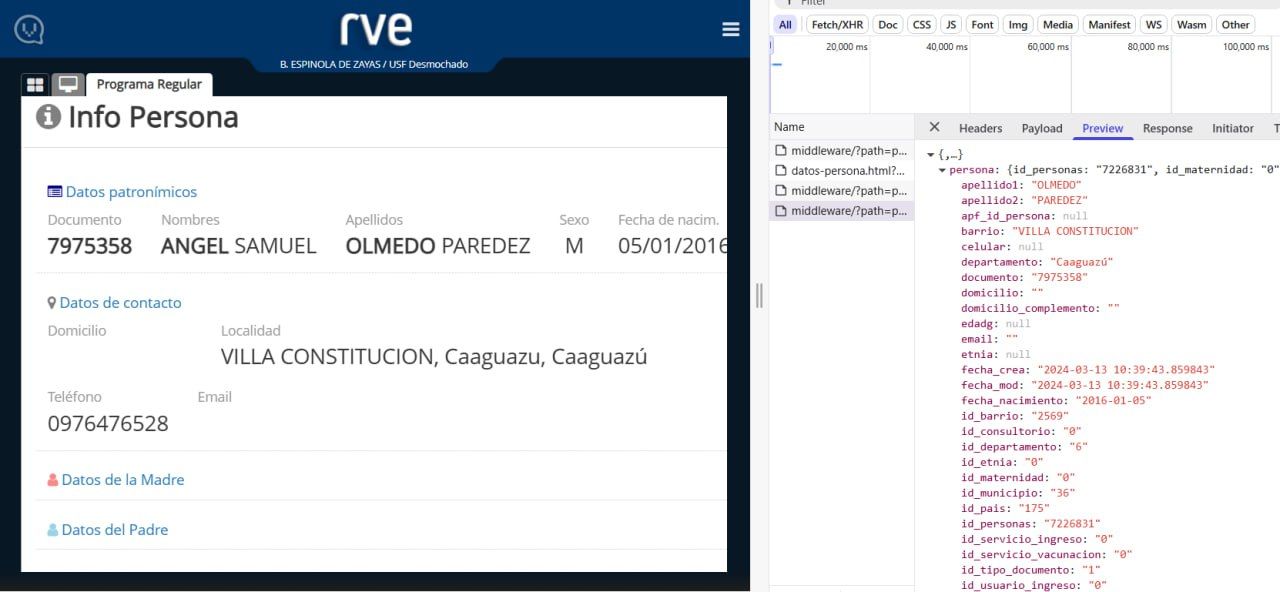
Resecurity cross-checked the document IDs against the acquired data set, which contained over 5 million records. The match allowed us to confirm the exact point of compromise (rve.mspbs.gov.py).
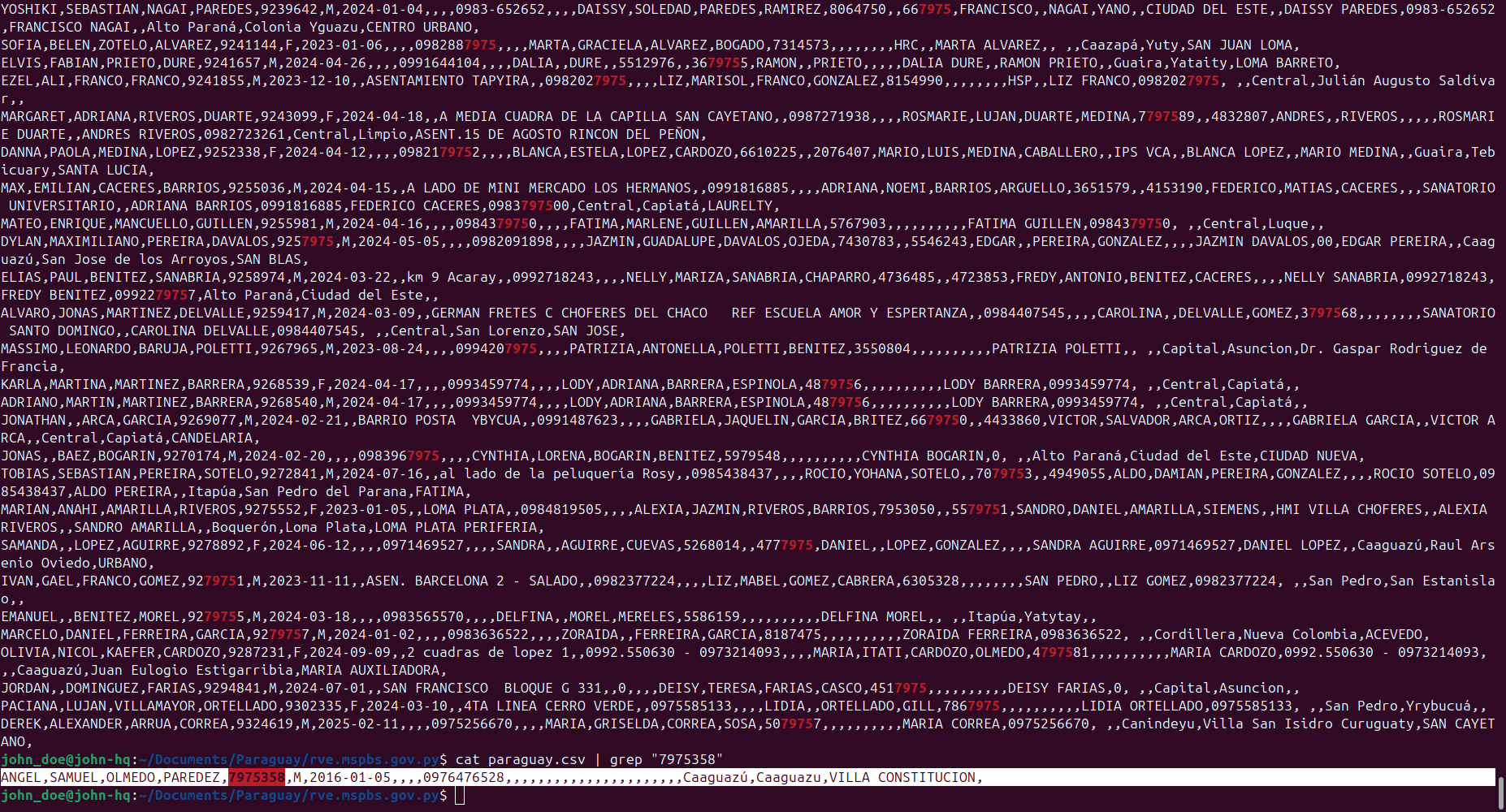
These two data breaches likely occurred at different times.
Resecurity also acquired the second artifact from the threat actor, who was logged into a customer portal related to another citizen.
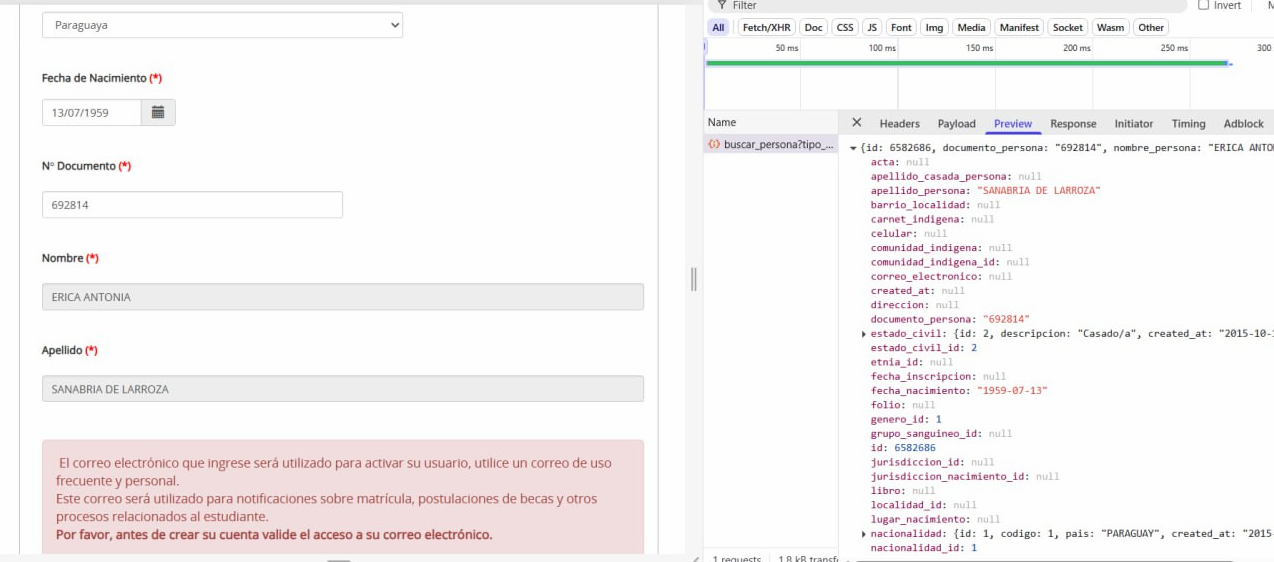
Our investigators successfully cross-checked the ID with the acquired dataset to confirm the match for additional validation.

The actor was able to confirm successful access to different citizens' accounts, and likely, as TTPs, used a combination of infostealer credentials and API abuse to collect data.
The Root Cause
The actor did not disclose how exactly he arranged the compromise. Such a leak could occur without exploiting any specific vulnerability, but rather by leveraging exposed access credentials. Based on our analysis, with a high level of confidence, infostealer activity could be the root cause of the data breach—one or several IT staffers may have been infected with malicious code, leading to their credentials being exposed.
Such compromises may have occurred some time ago, and the actor was carefully developing access to exfiltrate data. Considering the massive volume of information involved, such an event could have been arranged several months ago or even earlier.
The notable difference between the two data breaches is that the data exfiltrated from the National Agency for Transit and Road Safety of Paraguay (Agencia Nacional de Tránsito y Seguridad Vial de Paraguay) is presented in the form of a MySQL dump. In contrast, the records from the Ministry of Public Health and Social Welfare of Paraguay (Ministerio de Salud Pública y Bienestar Social) are shared as CSV files. Of course, the actor could have converted the data into different file formats during exfiltration, but this may indicate that the attack vectors could be slightly different.
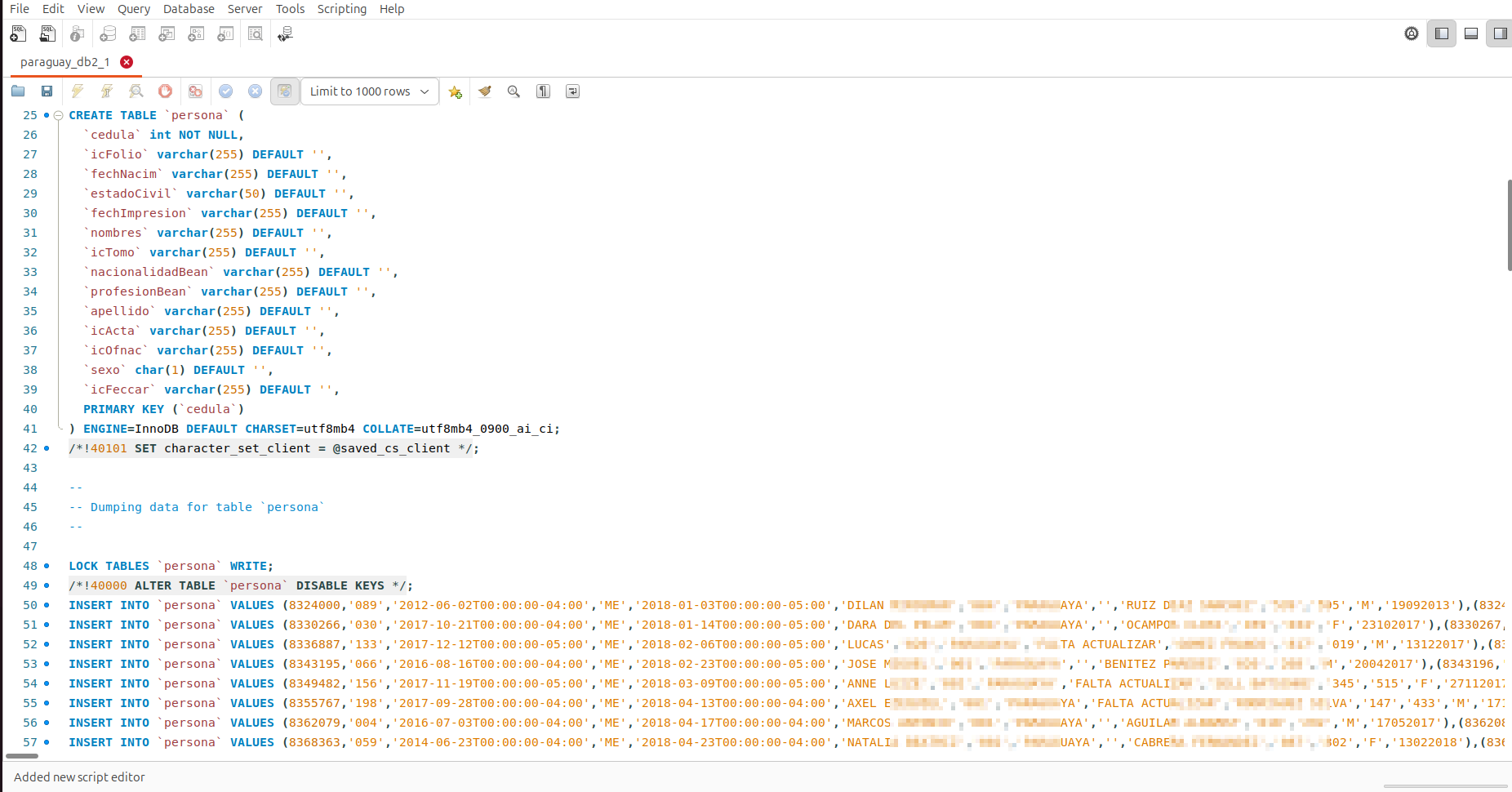
Such data breaches are not exclusive to Paraguay and have also occurred in other countries. Resecurity has covered details about these events in previous threat intelligence reports:
- Cybercriminals Attacked National Social Security Fund of Morocco - Millions of Digital Identities at Risk of Data Breach
https://www.resecurity.com/blog/article/cybercriminals-attacked-national-social-security-fund-of-mor...
- Massive Dump of Hacked Salvadoran Headshots and PII Highlights Growing Threat-Actor Interest in Biometric Data
https://www.resecurity.com/blog/article/massive-dump-of-hacked-salvadorean-headshots-and-pii-highlig...
- Cybercriminals leaked massive volumes of stolen PII data from Thailand on the Dark Web
https://www.resecurity.com/blog/article/cybercriminals-leaked-massive-volumes-of-stolen-pii-data-fro...
- The hack and leak of genetic data belonging to the direct-to-consumer DNA testing company 23andMe
https://www.resecurity.com/blog/article/hunting-genetics-data-cyberespionage-in-the-context-of-geopo...
- Cybercriminals have stolen PII data from Thailand’s Department of Medical Sciences, which contains information about patients with COVID-19
https://www.resecurity.com/blog/article/covid-19-data-put-for-sale-in-dark-web
Based on available threat intelligence data, Resecurity acquired artifacts containing infostealer logs, confirming that IT staffers of both impacted government systems were compromised and may be the source of these breaches.
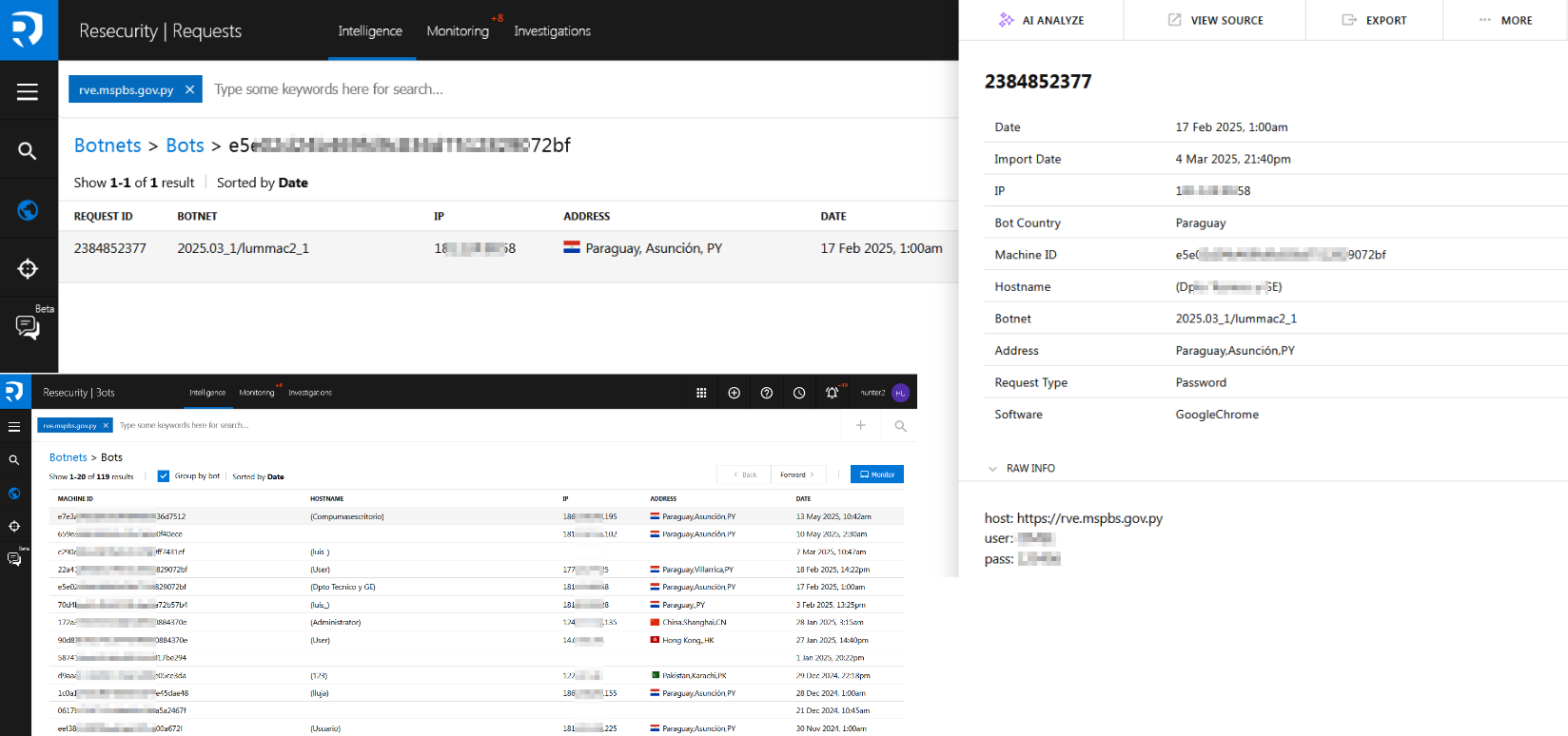
As such, the likely root cause of the data breach could be infostealer activity, specifically by the Lumma Stealer, rather than traditional hacking. Based on the collected artifacts, many third-party endpoints have been compromised with this infostealer. The threat actor could leverage the stolen access credentials and misuse available customer portals under the guise of an authenticated user.
National Security Implications
The data breach of such a scale hurts the entire country's population. This underscores the importance of proactive cybersecurity measures, including threat intelligence.
What was the motivation for the threat actor to attack Paraguay? The answer may not be straightforward, as it is unlikely that the actors behind the incident are just traditional cybercriminals. It is standard for advanced espionage groups and nation-state actors to use such tactics as a cover for their activities and to create plausible deniability of their involvement. The primary objective of the actors was to gather data on the entire country's population and target specific individuals. However, the actor may have also been opportunistic in their attack and in obtaining this sensitive data, which could impact nearly every citizen in the country.
Show Must Go On
May 31, 2025 - Another actor under the alias el_farado has created a posting on a prominent Dark Web forum and offered Paraguay data for sale. By description, it was like the postings made by Gatito_FBI_Nz, but in fact, it differed in the number of victims and possible source.
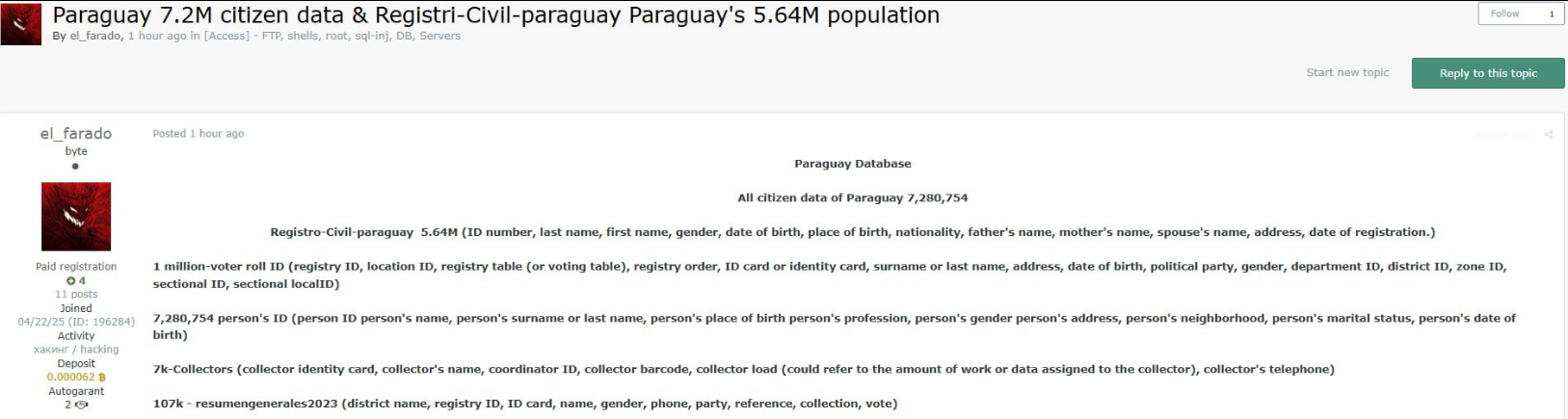
June 02, 2025 - Resecurity has contacted the actor to validate these claims. As a result of the Human Intelligence (HUMINT) engagement, the actor has uploaded the exfiltrated data to a popular file-sharing platform.
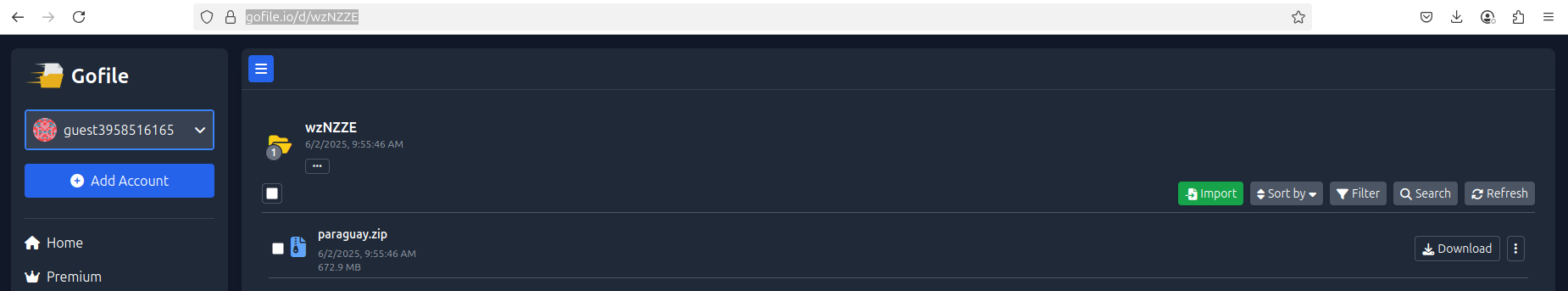
According to the actor, the data could originate from a new source, or from multiple government systems that store citizens' information ("Registro Civil") and electoral records.
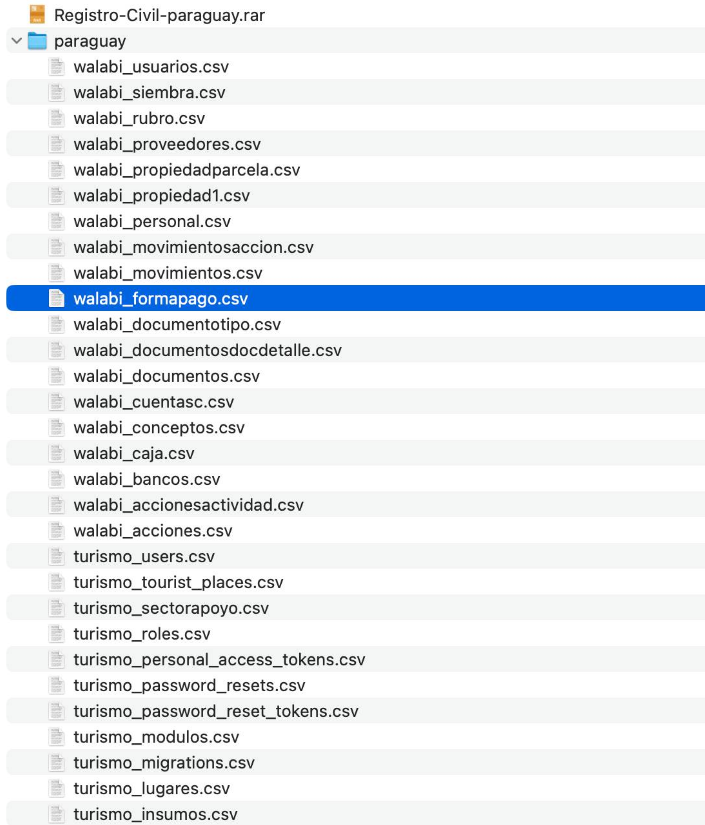
Based on the acquired artifacts, the data set contained relevant PII records. The files were dated March 24, 2025, but the actual data breach could have occurred at a different time.

The data set had a different structure from previous ones, which may confirm another source of compromise.
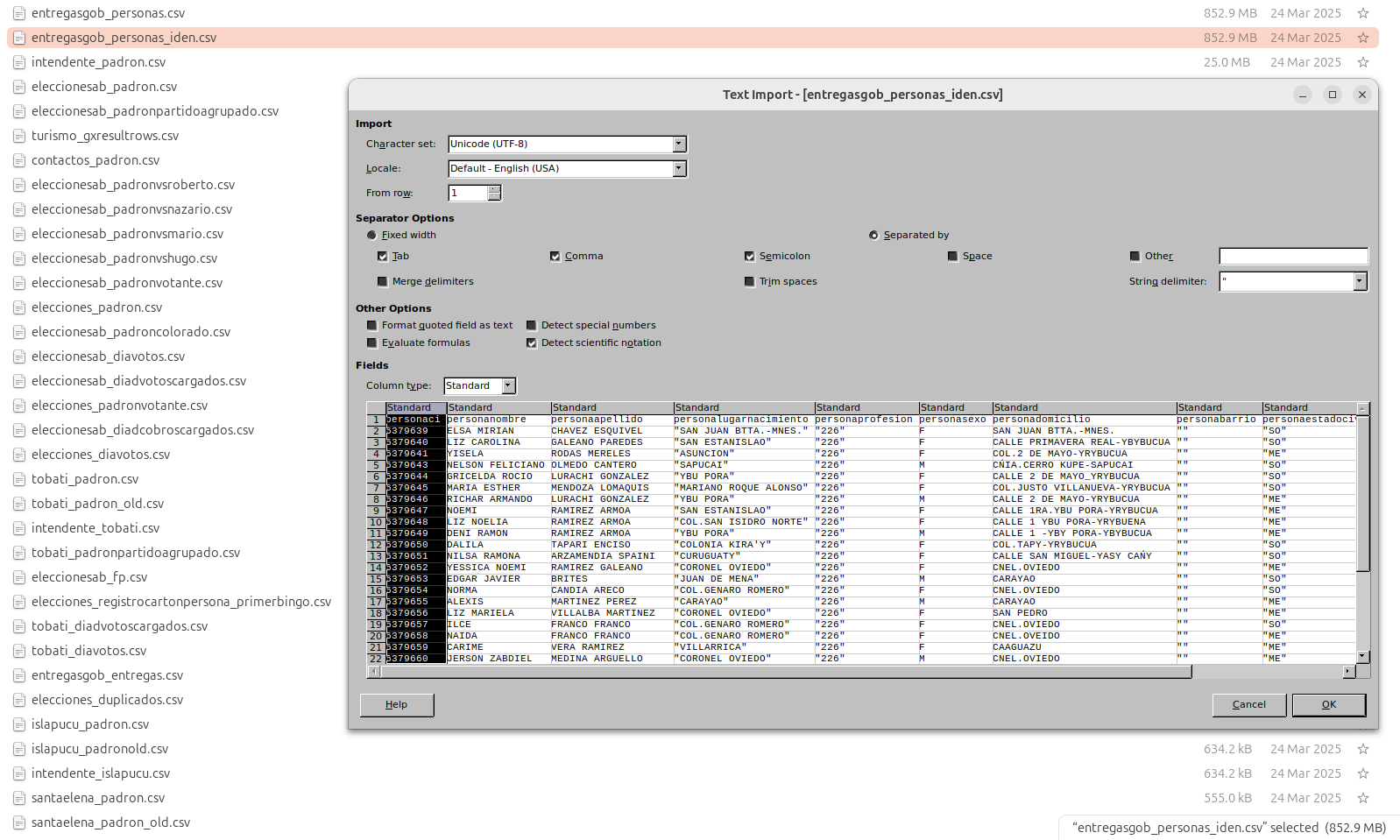
Notably, such large volumes of stolen data may facilitate the cross-correlation of details about specific individuals, which could be of interest to foreign intelligence agencies as well as fraudsters.
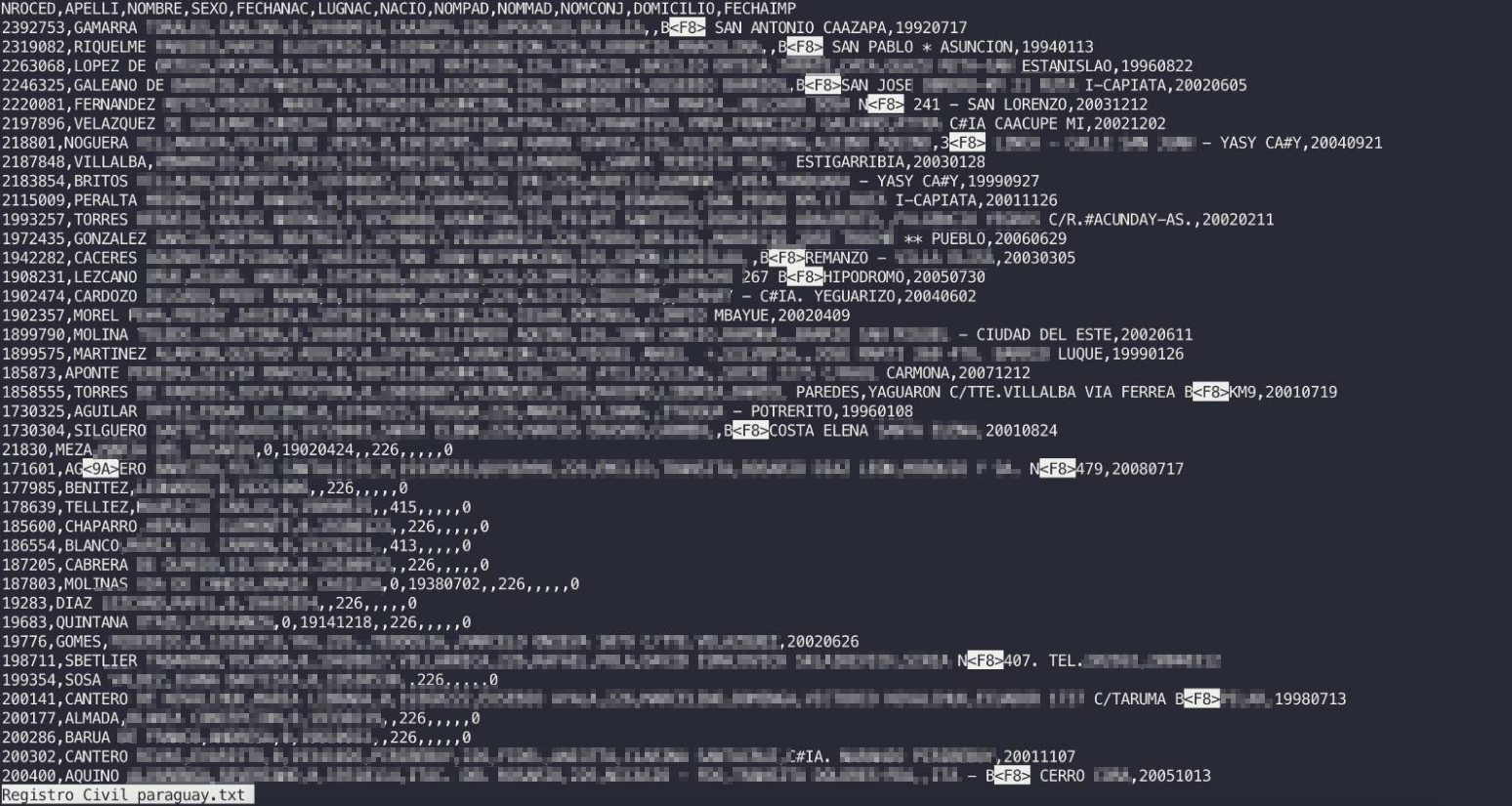
Cross-checking the acquired records reveals that one of the files, a stolen Civil Registry database, was leaked almost two years ago by another actor. Other files - have not been previously leaked, and contain records with timestamps from 2025. It is unclear whether the same actor is responsible for the reuse or if it is a result of a different breach. Resecurity has recovered a historical record with a fragment of a stolen data set. Likely, the actor included it as additional information to show the scale of resources breached and mixed it with new, previously unreleased data sets.
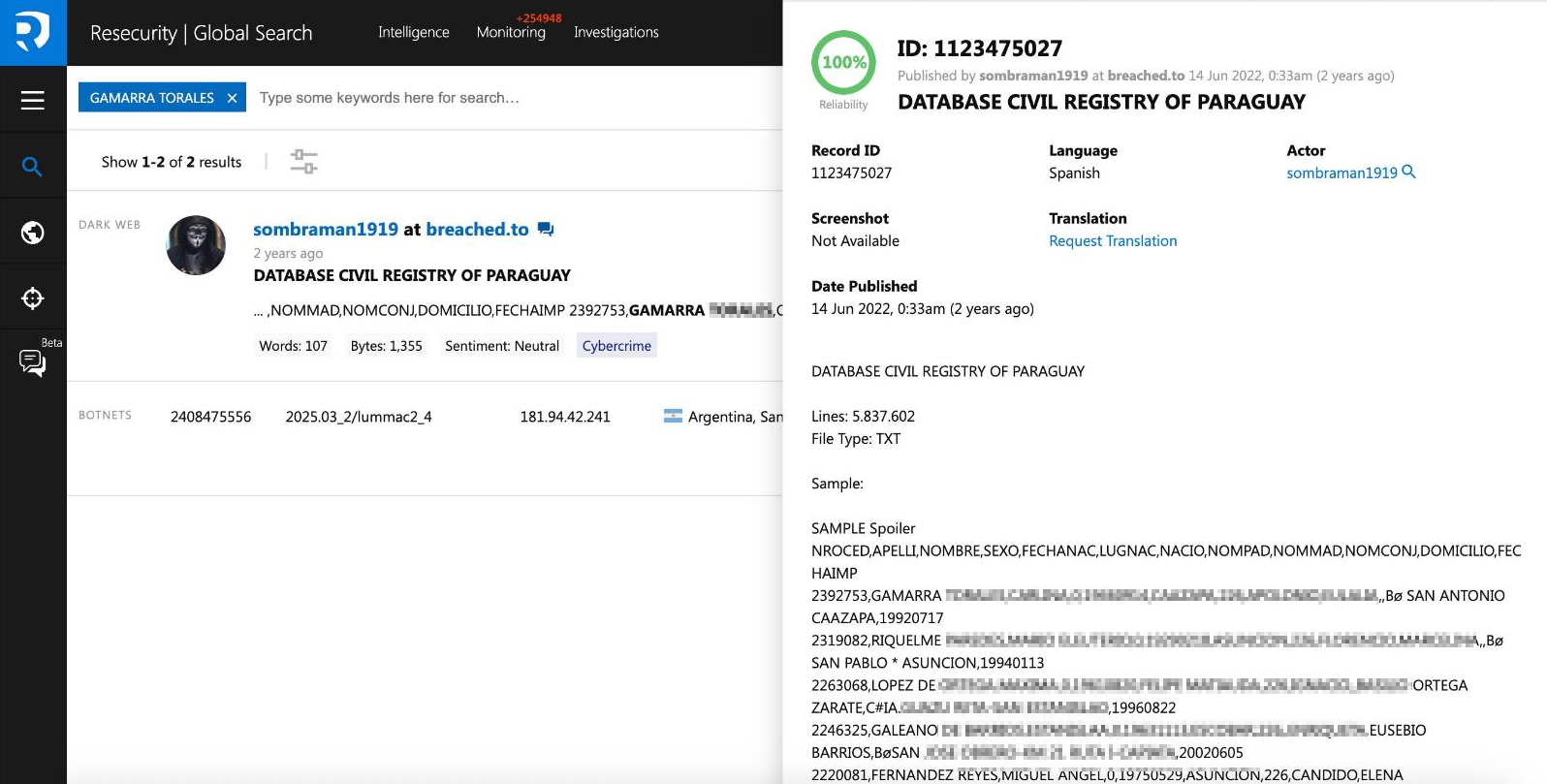
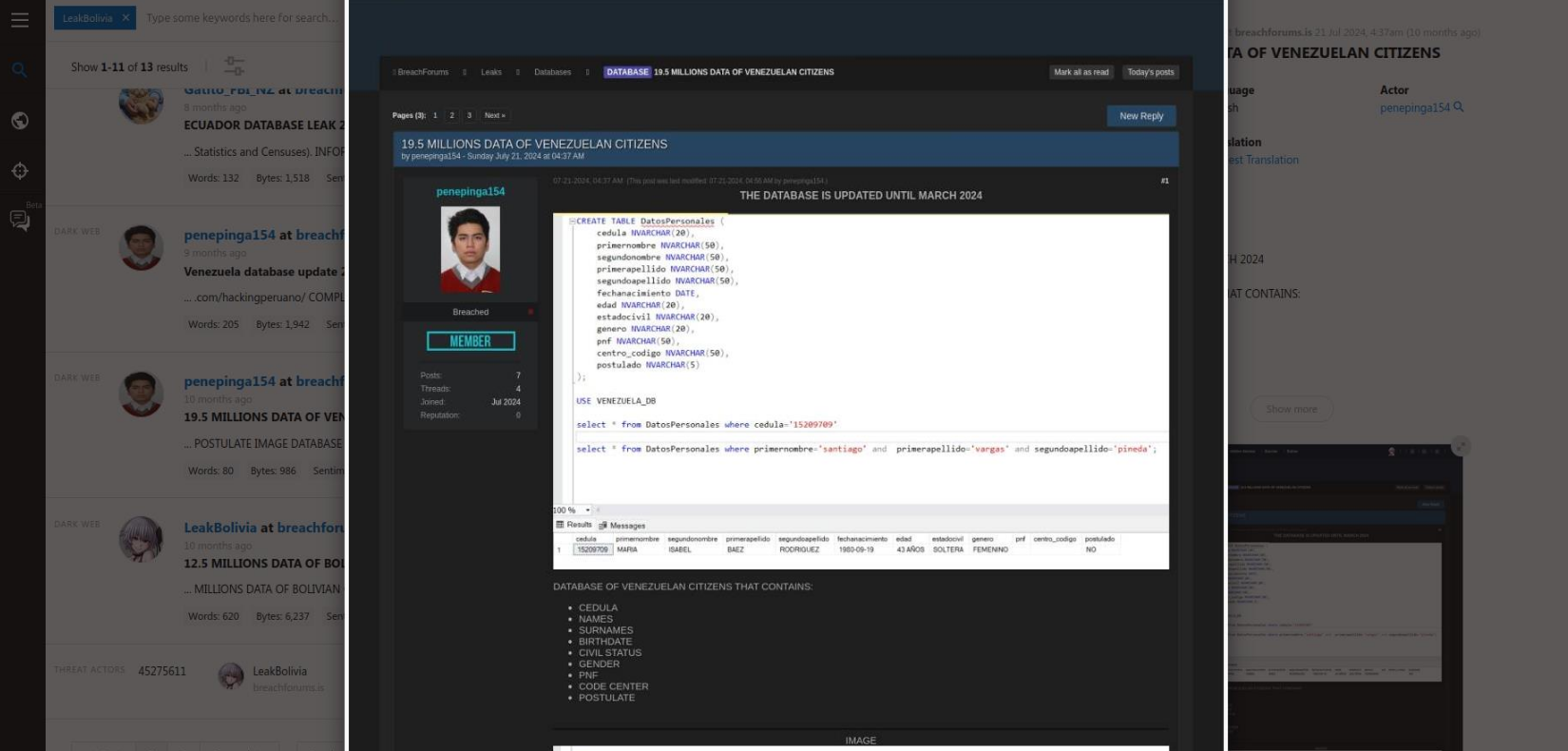
The profile of one of the key actors is known for several large-scale data breaches across South America. He was able to compromise multiple government systems of Bolivia, Venezuela, Ecuador, and steal millions of PII records. His motivation is not entirely clear, as the price he offers for this data is not substantial. Likely, such tactics could be employed by foreign intelligence or state-sponsored actors, masking targeted espionage operations under the guise of possible cybercrime activity to obscure attribution.
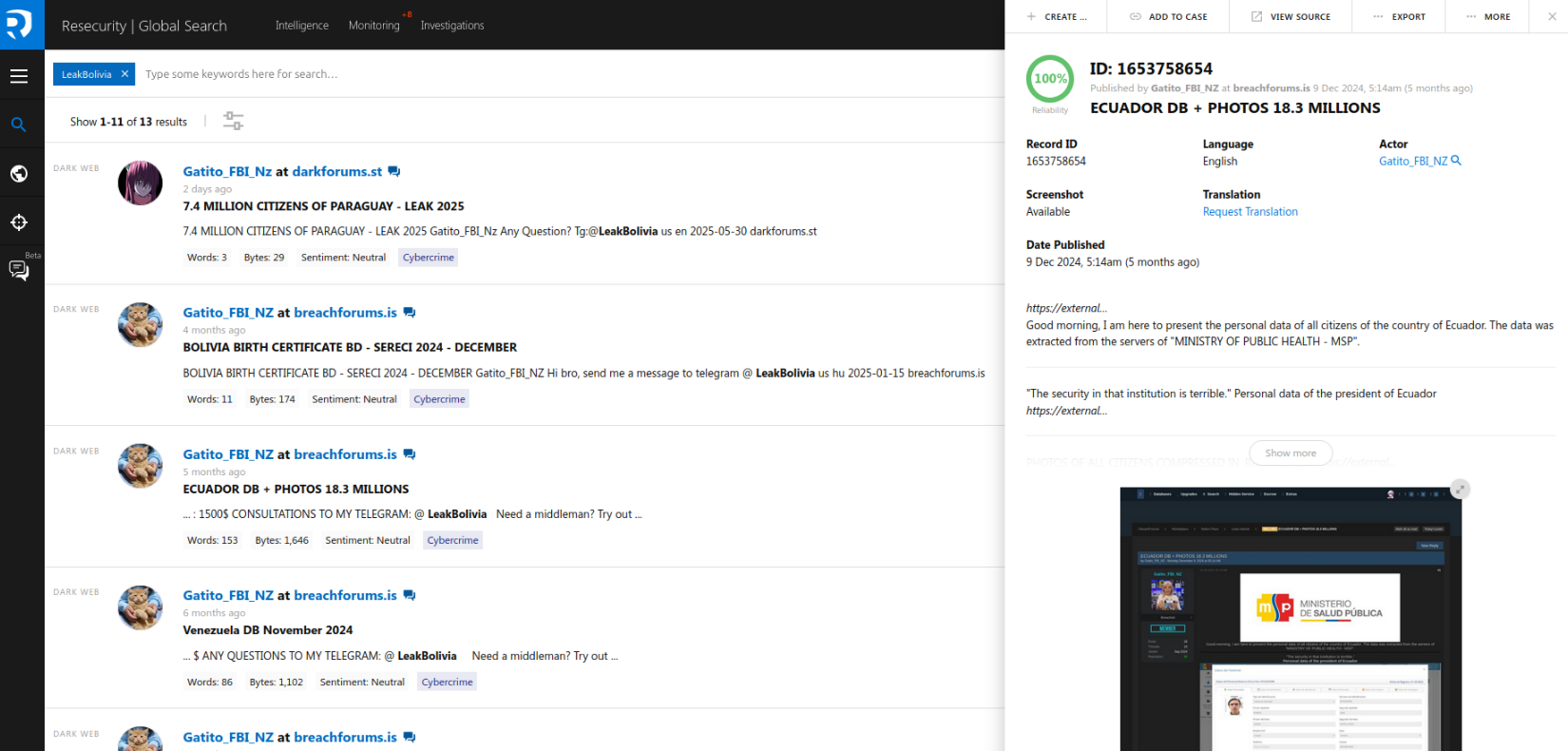
The actor has changed his alias several times; in the past, he was known as LeakBolivia and penepinga154.
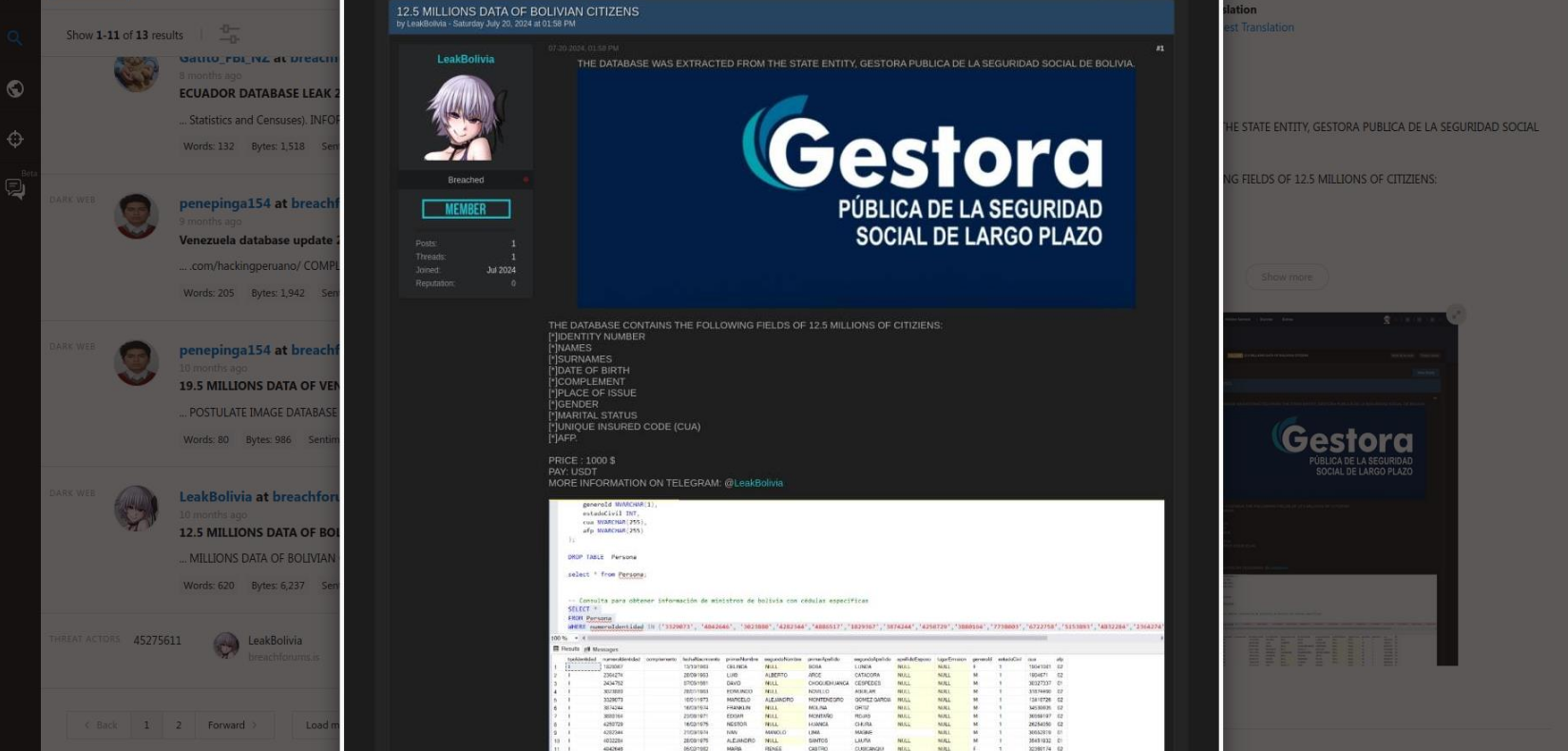
All the data breaches he has conducted have resulted in millions of victims due to data theft.
Notably, the profile of one of the actors was already known in connection with the prominent ransomware group known as "FunkSec," which has been involved in multiple hacking and leak operations. The group emerged in late 2024 and has already claimed over 85 victims. In December 2024, FunkSec launched its data leak website, which became a centralized platform for operations. In addition to hack announcements, the site features tools for conducting DDoS attacks and unique software within the ransomware-as-a-service (RaaS) model. Most of FunkSec's victims are in the United States, India, Italy, Brazil, Israel, Spain, and Mongolia. Analysis has shown that the group likely consists of newcomers seeking notoriety by recycling data from hacktivist-related leaks. Some members of the group have previously been active in hacktivism, highlighting the blurring of the lines between hacktivism, cybercrime, and espionage.
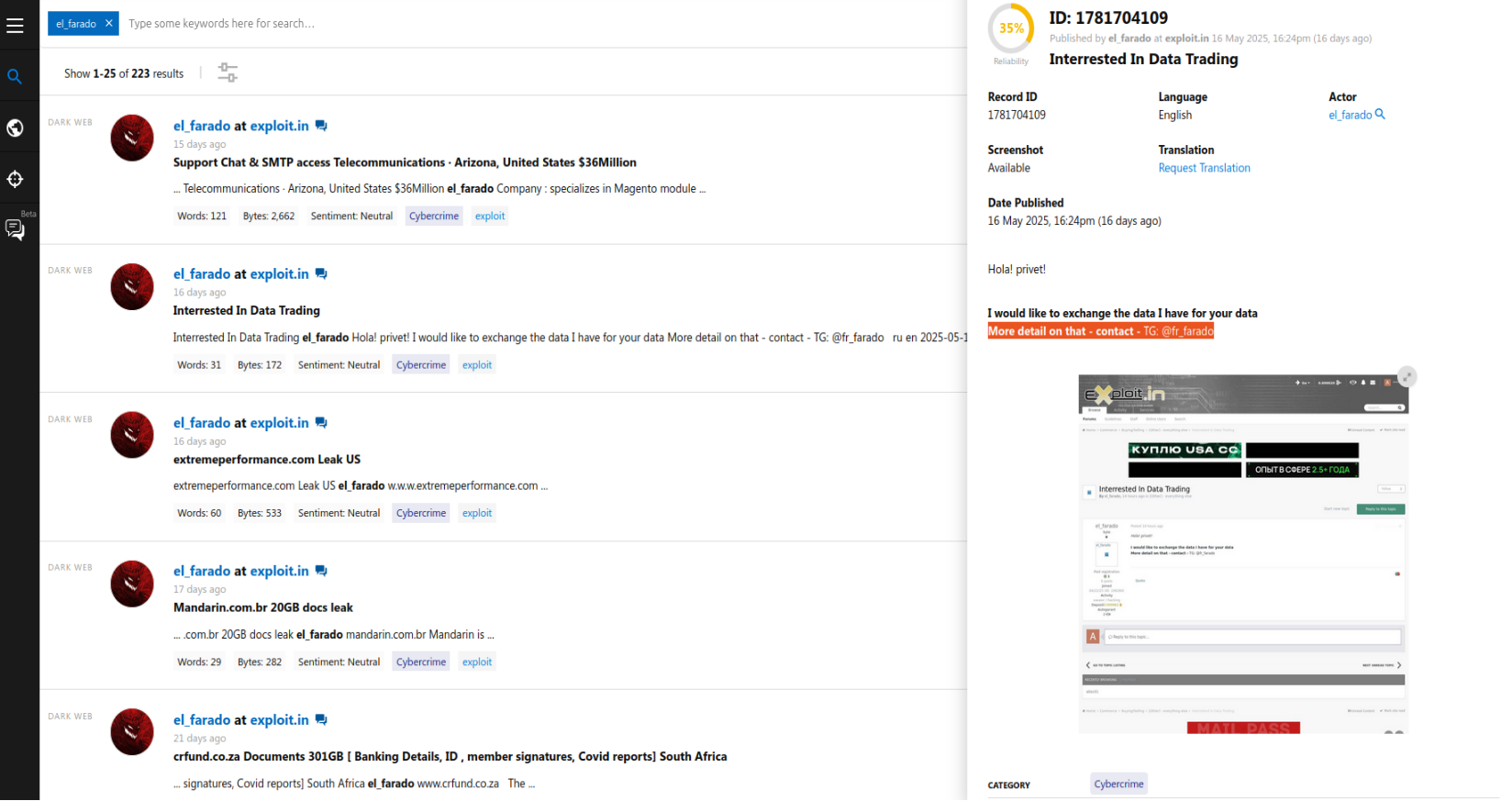
Based on the current assessment, these two actors may not be directly connected, and their motives may differ. In one case, the actor is closely tied to ransomware activities, while another acts as an independent access broker - essentially a mercenary. Very often, such actors are recruited by foreign states to acquire data of interest via targeted cyberattacks. In previous threat intelligence reports, Resecurity highlighted the "thin line" between cybercriminals and nation-states, who optimize costs and obscure the origin of their attacks by using "third parties" in face of opportunistic contractors found on the Dark Web.
Shadow Games - Behind the Scenes
These leaks are not new in Paraguay. Notably, the two newly revealed incidents follow several other recent data breaches affecting Paraguay. In 2025, just a few months ago, Paraguay experienced two massive data breaches originating from public institutions. The first involved the Superior Tribunal of Electoral Justice (TSJE) and exposed information on more than 7 million people. The second affected the Ministry of Finance, the Central Bank of Paraguay, and Itaipú, where a file containing over 17,000 records was made public, including sensitive data such as payments to public officials, salaries, full names, and ID numbers. In 2023, a data breach at the National Police exposed documents and personal data of detained individuals, including criminal records and photographs.
Besides confirmed data breaches and cybercrime activity, the country is actively combating disinformation. Just recently, Paraguay has launched investigations into an alleged cyberattack by Brazil targeting its government systems to obtain sensitive information about the Itaipu Binacional hydroelectric power plant, Foreign Minister Rubén Ramírez Lezcano confirmed. He said that national intelligence and the Technologies and Information Ministry (MITIC) were investigating the claims, although no evidence of a breach had been found yet. In addition, MITIC Minister Gustavo Villate noted that no vulnerabilities have been detected so far, emphasizing the importance of proactive cybersecurity measures. The probe was triggered by Brazilian media reports, notably UOL, which claimed that the Brazilian Intelligence Agency (ABIN) had hacked Paraguayan systems under the previous government of Jair Bolsonaro in June 2022 to access confidential data on Itaipu tariff negotiations.
The intensity of cyberattacks and data breaches targeting Paraguay and other countries in South America is alarming. Resecurity highlights the increasing efforts of foreign threat actors to compromise government information systems and portals that store PII of citizens.
Significance
The increase in data breaches impacting digital identity in Paraguay may highlight the dynamics of the cyber threat landscape in South America. Such incidents may also highlight the country's growing significance in this increasingly interconnected region.
As geopolitical challenges intensify, compounded by this and other breaches, cyberattacks targeting Paraguay are expected to increase, underscoring the need for cybersecurity leaders to accelerate their defenses. Paraguayan authorities should establish Public-Private Partnerships to enable the timely and actionable exchange of cyber threat intelligence, thereby enhancing the protection of government agencies and major enterprises from ongoing cyber threats.
Resecurity expects this trend to continue and has informed relevant law enforcement agencies about the incident, sharing additional insights to provide more context about the identified data breach.

