Knownsec Data Breach: A Trove of Espionage Tradecraft with an Insider Narrative
Cyber Threat Intelligence
Introduction
The Knownsec leak is a pivotal incident of 2025 because it exposed the inner workings of a major state-linked Chinese cybersecurity firm, revealed espionage tools and global targets, internal documentation, and evidence of ongoing cyber operations targeting other countries.
The Chinese government and state media have officially denied and downplayed the Knownsec leak incident. When questioned, the Chinese Foreign Ministry spokesperson stated that they were unaware of any breach at Knownsec and reiterated that China "firmly opposes and combats all forms of cyberattacks." This approach is consistent with previous incidents involving alleged state-linked cyber operations, where Chinese authorities typically issue blanket denials or express unfamiliarity, while emphasizing their official stance against cyberattacks.
Resecurity acquired the complete data set and prepared an analysis to increase awareness within the cybersecurity community. The Knownsec data leak has exposed a trove of internal documents, offensive cyber tools, and evidence of global targeting by a Chinese cybersecurity firm with government ties. The breach is prompting international investigations and raising concerns about the scale and sophistication of Chinese cyber operations.
The leaked Knownsec tradecraft details tools used externally to monitor and breach targets like foreign governments, critical infrastructure, and private-sector enterprises, as well as internally to track Chinese companies and individuals for intelligence, control, and counterintelligence. Revealing these tools helps divert suspicion from entities acting for the Chinese government, complicate attribution, and fuels internal power struggles, all while maintaining plausible deniability.
Timeline
Notably, around November 7, 2025, the stolen data was presumably sold on the Dark Web by an actor under the alias t1g3r. This moniker had no prior history and was likely created deliberately to publicize the leak. Subsequently, the same data was offered for sale again on another underground community later in December.
At some point, this leak resembles the recent i-Soon leak from another Chinese cybersecurity venture involved in offensive cyber operations and espionage activity. However, its root cause is likely not due to random hacking but rather a much more delicate issue, such as insider activity.
Insider Involvement
Based on the insights collected by our HUNTER team, the source of the leak could be an insider (rogue employee).
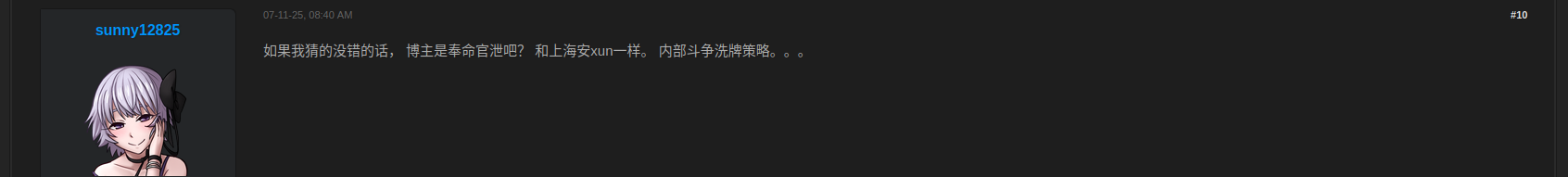
In one of the statements, another actor familiar with the matter commented: "If I had to guess, the poster is leaking, similar to the Shanghai i-Soon incident. It's a tactic to stir up an internal power struggle."
What Has Been Breached?
Knownsec (known as Beijing Knownsec Information Technology Co., Ltd.) is a major Chinese cybersecurity company with close ties to the Chinese government and military.
KnownSec -- 知道创宇信息技术股份有限公司 (Beijing Knownsec Information Technology Co., Ltd)
Unified Social Credit Identifier Code (统一社会信用代码): 91110108666277620Y
Registration Code (注册号): 110108010419556
Organization Certification Code (组织机构代码): 666277620
Legal Representative (法定代表人): Zhao Wei 赵伟
The company is known for its "Internet Aegis" and "Enterprise Digital Fortress" systems and is associated with the global vulnerability-scanning and network mapping tool, ZoomEye.
What Has Been Leaked?
Over 12,000 internal documents from Knownsec were leaked, offering a rare glimpse into China's state-backed cyber arsenal and operations. The materials, briefly posted on GitHub, revealed:
Hacking Tools:
A sophisticated array of cyber tools, including Remote Access Trojans (RATs) designed to compromise various operating systems (Linux, Windows, macOS, iOS, Android), allowing persistent remote access.
Global Targets:
Extensive surveillance target lists covering more than 20 countries and regions, including India, South Korea, Taiwan, Japan, Vietnam, and the UK.
Stolen Data:
Evidence of large volumes of stolen data, such as 95 GB of Indian immigration records, 3 TB of South Korean call logs from LG U Plus, and 459 GB of Taiwanese transport data.
The rest of the data was offered for sale on several underground communities and Dark Web marketplaces.
Identified Tradecraft
Resecurity identified several tools used in offensive cyber operations, developed by Knownsec - ranging from data theft and malicious code to more tailored solutions for Internet surveillance. Based on the current assessment, this tradecraft could be designed to meet the specific needs of the affected company's state-side customers. It is also possible that some of these tools could be used by the company itself to conduct intelligence gathering worldwide.
Email Content Eavesdropping Platform
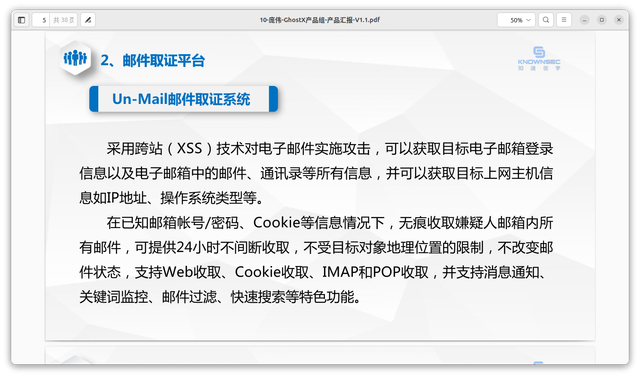
One of the leaked documents mentions Un-Mail, an email content eavesdropping system. The name of the solution is likely internal and was used as a project codename related to data exfiltration from compromised email accounts. It employs XSS technology to obtain email login credentials, emails, contacts, and related information. It can also gather host information such as IP address and OS type.
What does it do? By knowing the email account, password, and cookie information, it can monitor the target's email 24/7, regardless of geographical location. The tool does not alter the email status and supports collection via Web, Cookie, IMAP, and POP protocols. It also provides message notifications, keyword/phrase monitoring, email filtering, and quick search features.
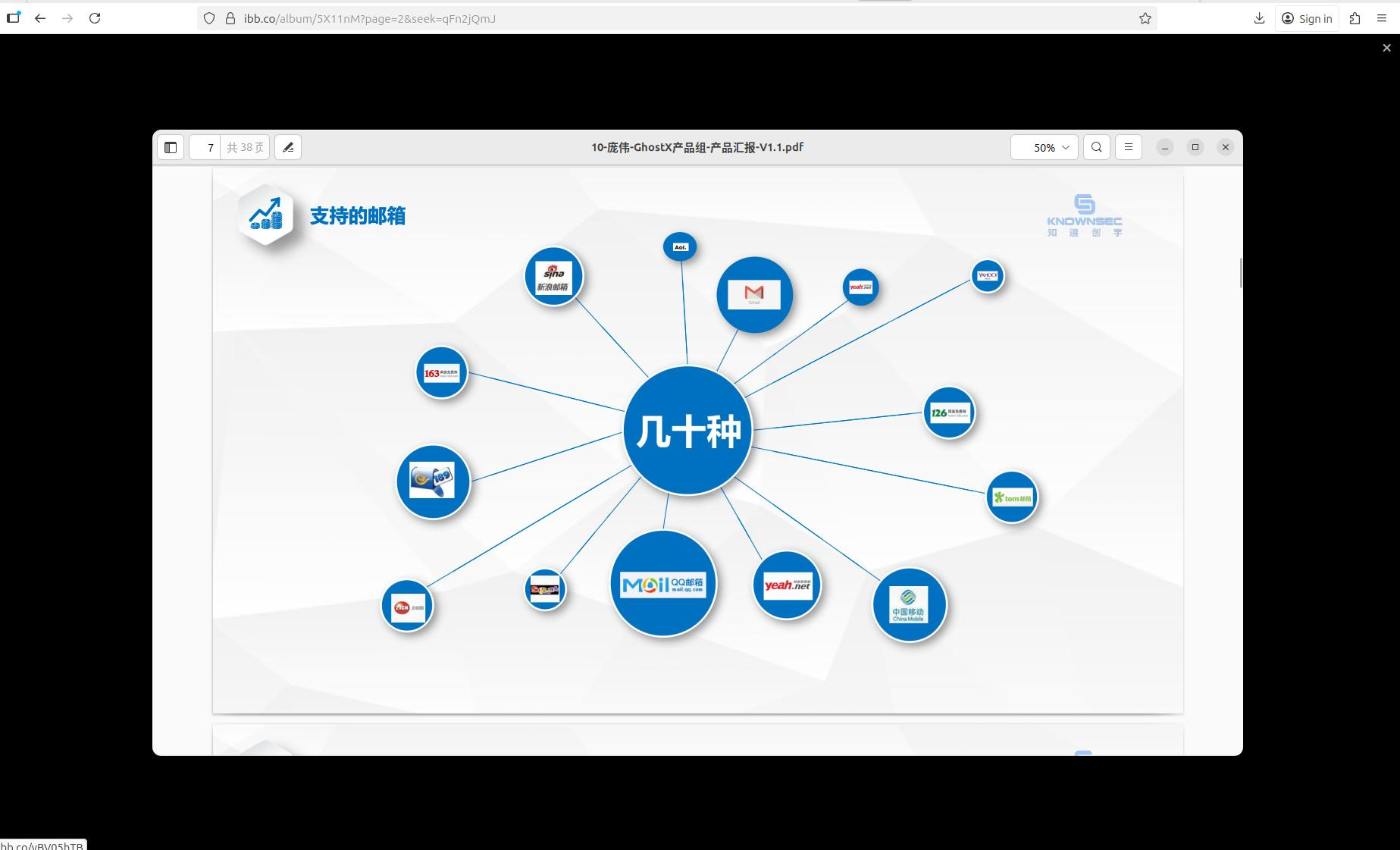
Un-Mail supports both Chinese email providers (such as QQ, 163, Sina, and China Mobile) and foreign providers, including but not limited to Gmail, Yahoo, and AOL.
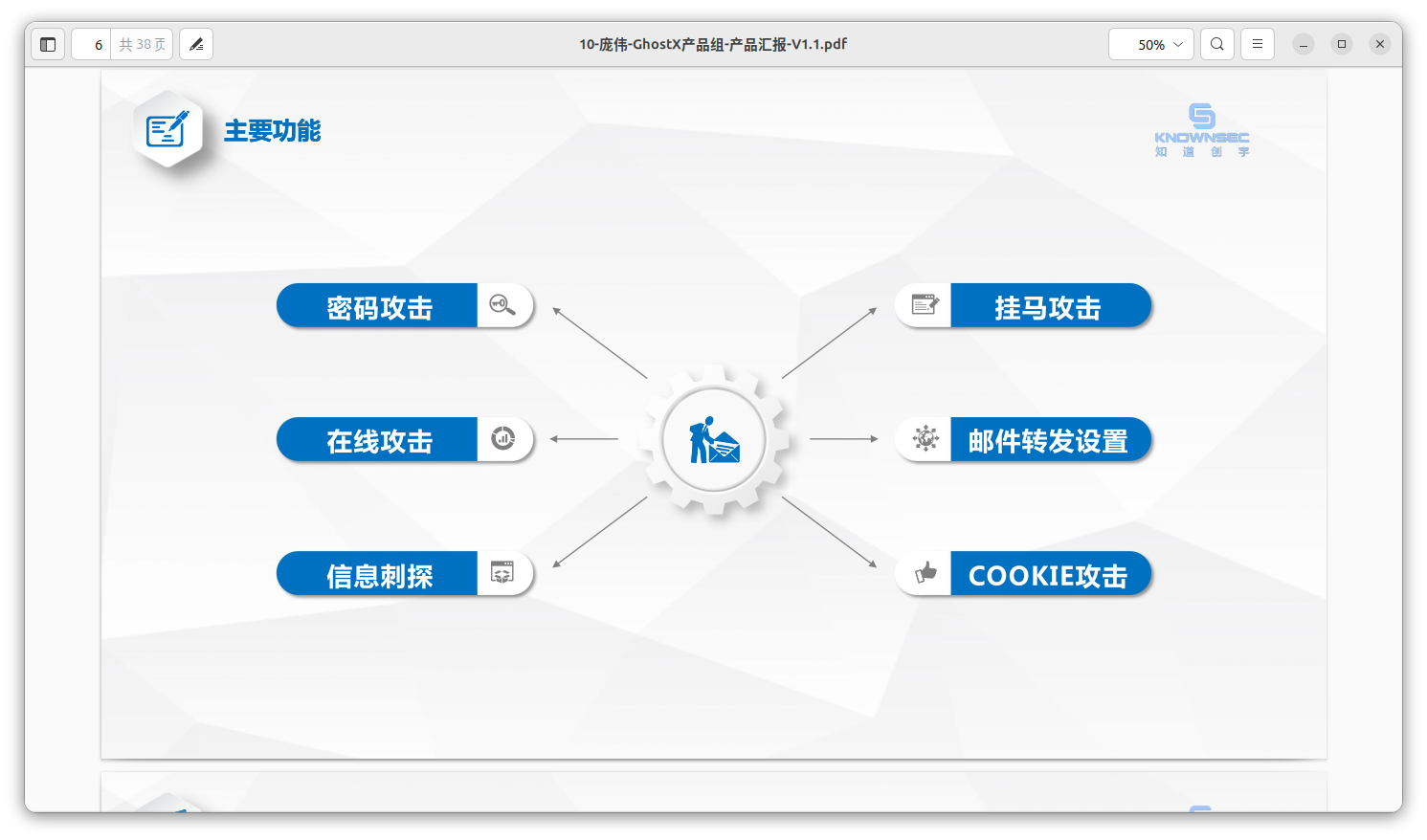
Un-Mail is leveraging the following methods to acquire e-mail content:
- Password Attack
- Online Login (via Web)
- Email Forwarding
- Cookie Manipulation
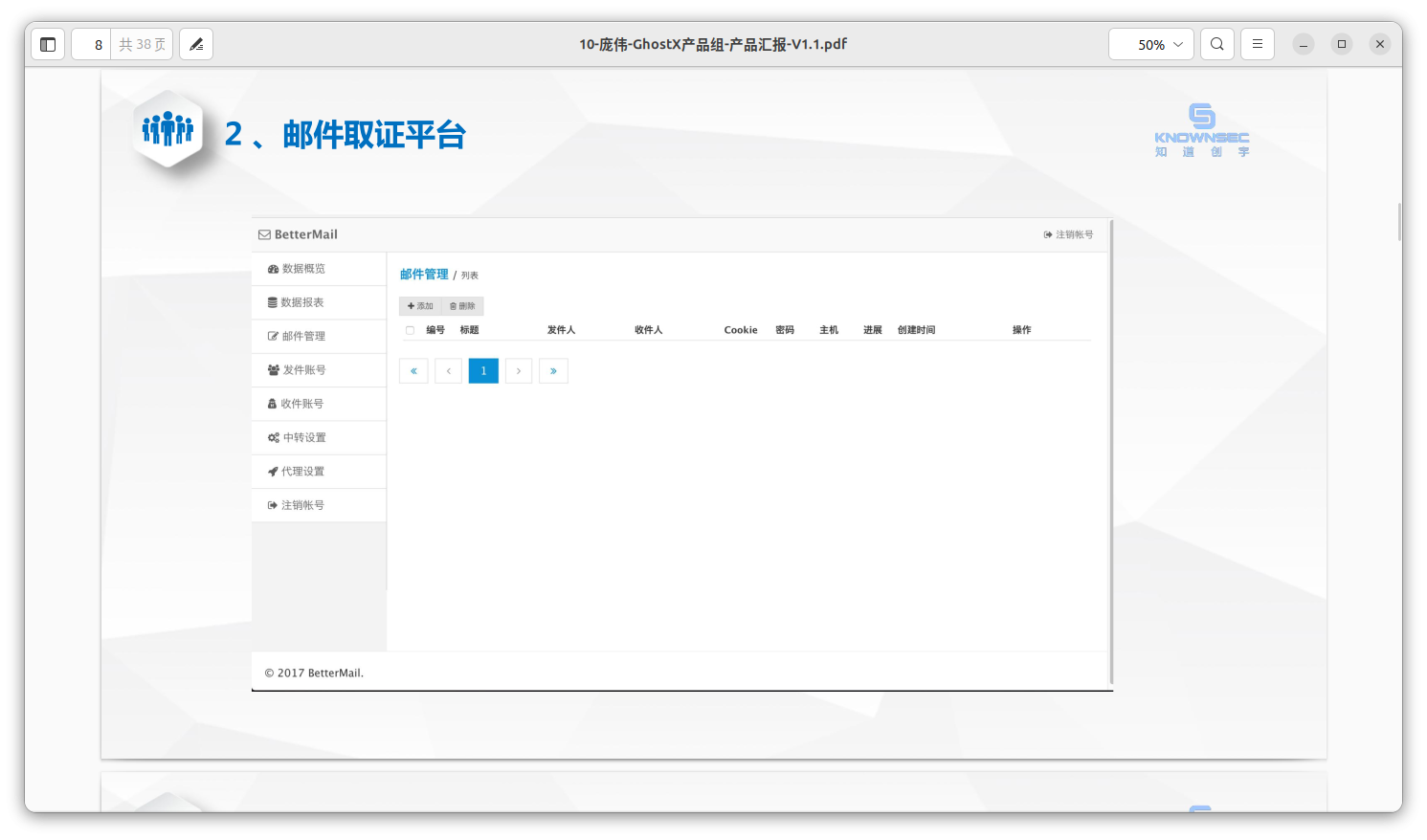
The exfiltrated e-mail content is stored in a centralized platform, having the following features to support multiple targets (victims) and navigation between them:
- Data Overview
- Data Lists
- Email Management
- Sender Accounts
- Receiver Accounts
- Transit Settings
- Proxy Settings
- Delete Account
The “Email Management” tab has the following fields:
- Number
- Title
- Sender
- Receiver
- Cookie
- Password
- Host
- Progress Status
- Creation Time, Actions
This email tool also has a capability to map out relationships (between the sender and e-mail receivers):

Identification of relationships is an important feature of intelligence analysis. It detects and extracts sender, receiver, time of email, subjects, keywords from the content. The analyzed data can be visualized to better understand the connections between emails.
Remote Control System (RCS) - Windows T-Horse
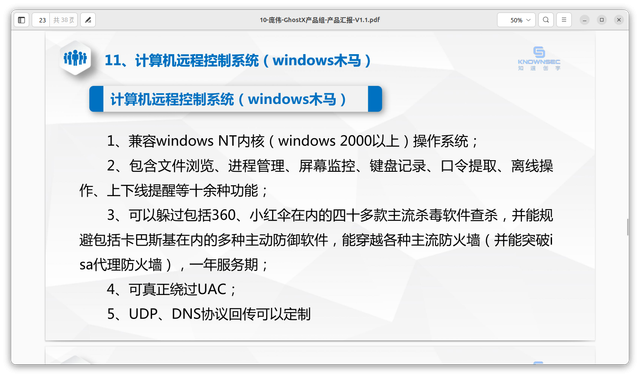
The solution acts as a Remote Control System (RCS), known internally under the codename Windows T-Horse. It is compatible with Windows NT Incore (Windows 2000+) operating systems and features capabilities similar to Remote Administration Tools (RAT). These include file browsing, remote management, screen monitoring, keyboard capturing, credential extraction, offline operation, and notifications for going online or offline.
According to specifications, it can evade more than 40 major antivirus applications, such as Qihoo 360 (China), Avira (Germany), and Kaspersky (Russia), as well as host-based firewalls. This service is offered via a yearly subscription. The company stated that the product can bypass UAC and utilize covert communication channels through DNS.
Compromised Data of Foreign Countries
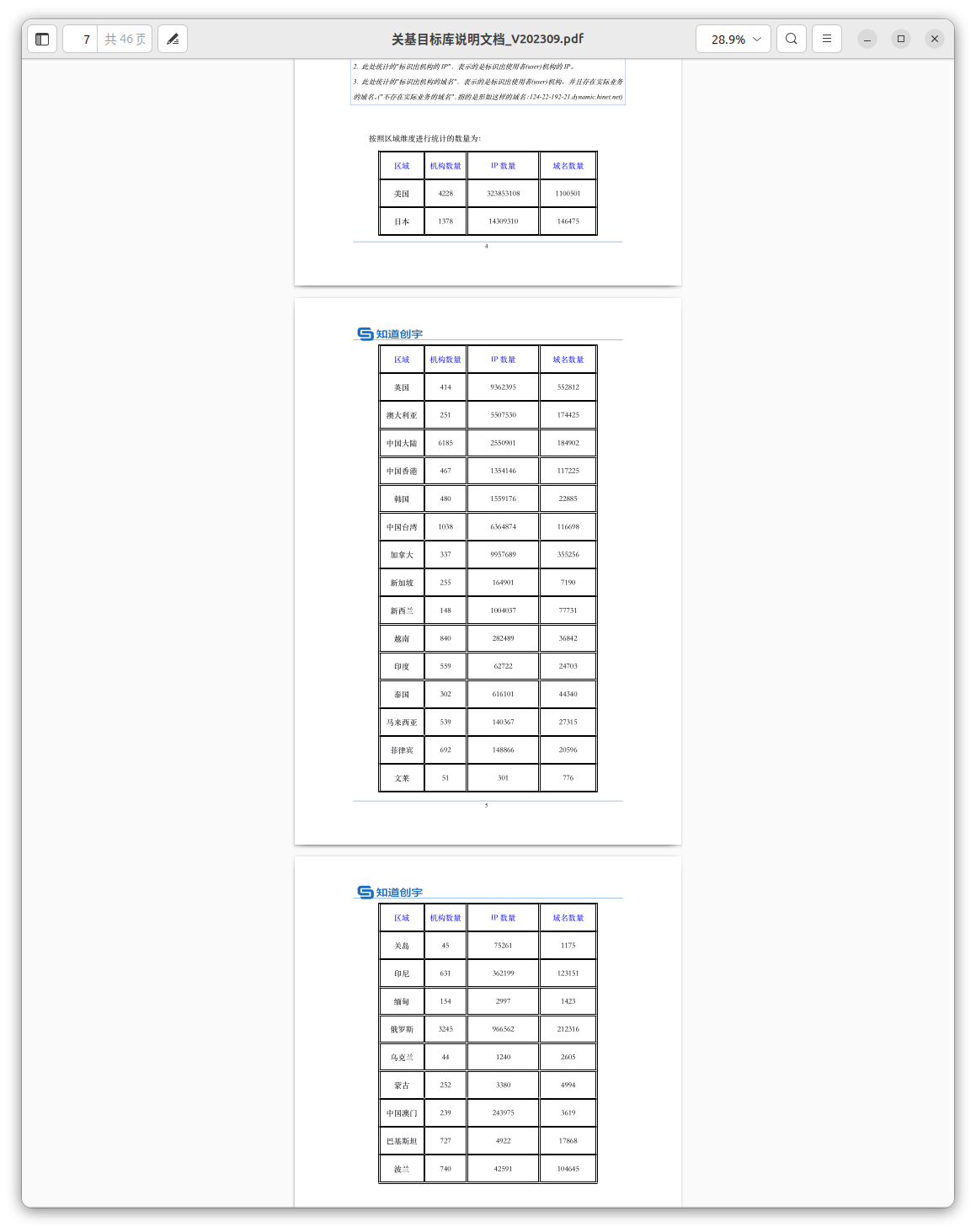
The company is acquiring large volumes of compromised data, with further analytics related to geography, identified organizations, domain information, and network details.
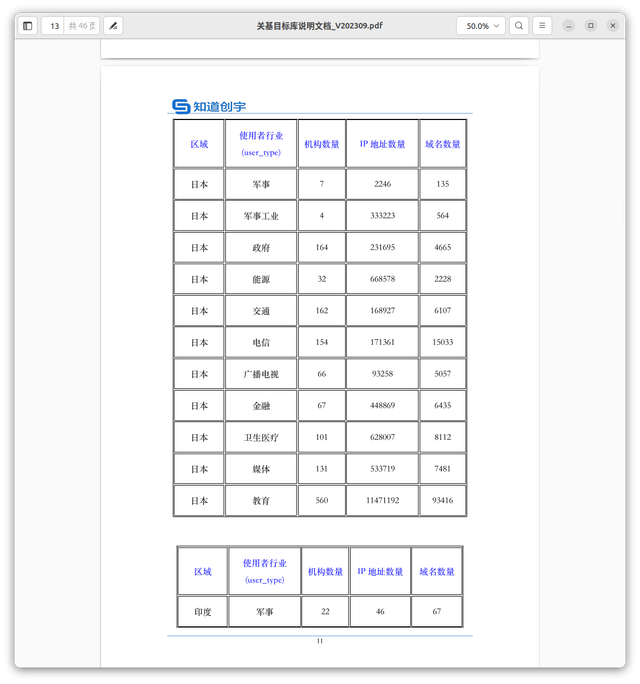
A strong targeting of Japan was identified, along with criteria related to military, government, energy, and transport organizations. Additionally, evidence was found of compromised data collection from domestic (Chinese) enterprises.
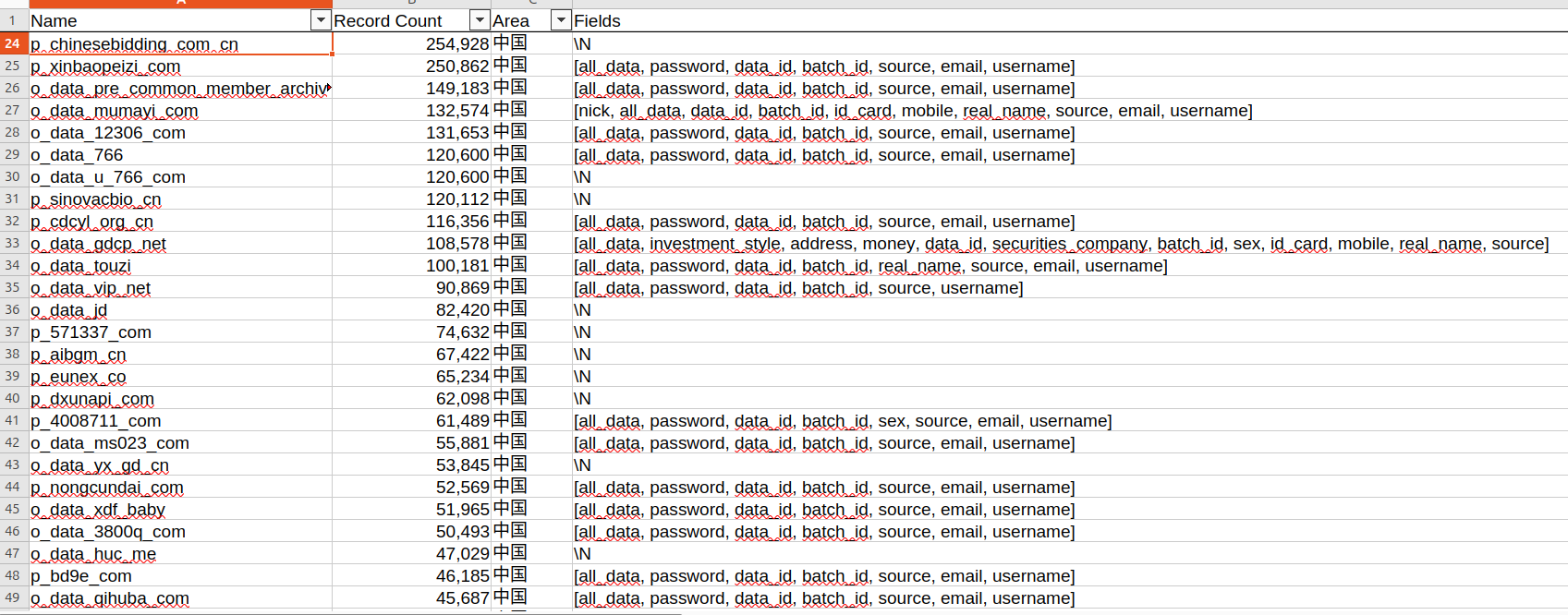
The image above shows data related to various Chinese enterprises, such as Chinese Bidding, Xinbaopeizi (新宝配资), and SINOVAC, including Chinese government agencies such as 12306 (which stands for Chinese Railway), cdcyl.org (Communist Youth League of China), and many others. The list highlights the presence of password data—likely intended for cross-checking to gain access to accounts linked to particular individuals.
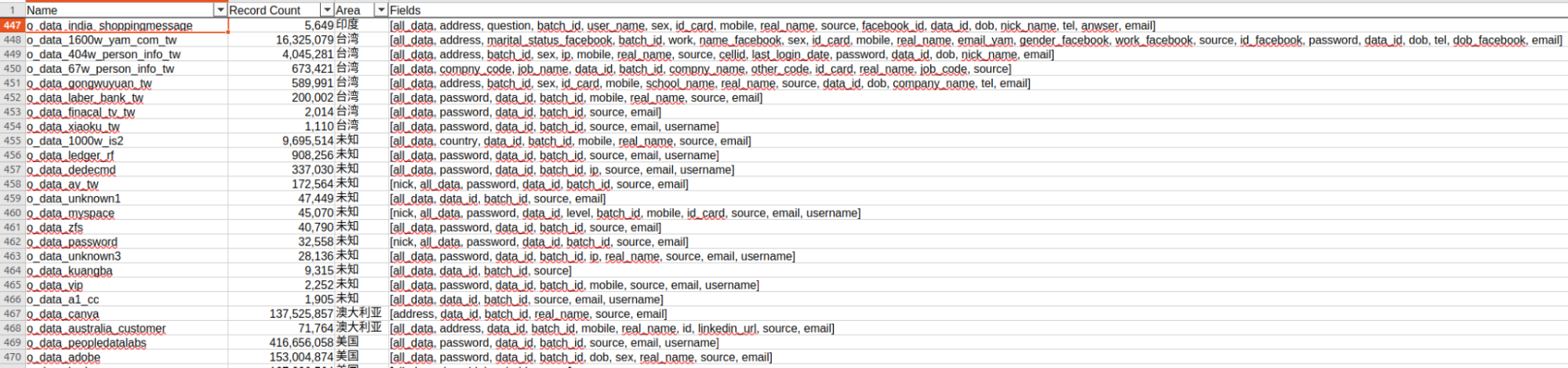
The acquired lists reference notable foreign enterprises, including Yam.com (a Taiwanese email provider), Kaungba (a Chinese crypto-mining service), and Ledger (a French crypto-wallet company). Notably, some of these organizations have previously suffered data breaches, and it is likely that the company was aggregating such data to identify specific targets of interest. Some items in the lists are marked as "Unknown"—probably indicating that these data sets originate from third parties or were purchased on the Dark Web.
Network Reconnaissance - ZoomEye
An extensive dataset related to Taiwan's critical infrastructure organizations and agencies was also identified, containing publicly accessible network devices associated with them. Such data could likely be used in Knownsec's product, ZoomEye, or for targeted exploitation activities targeting Taiwan.
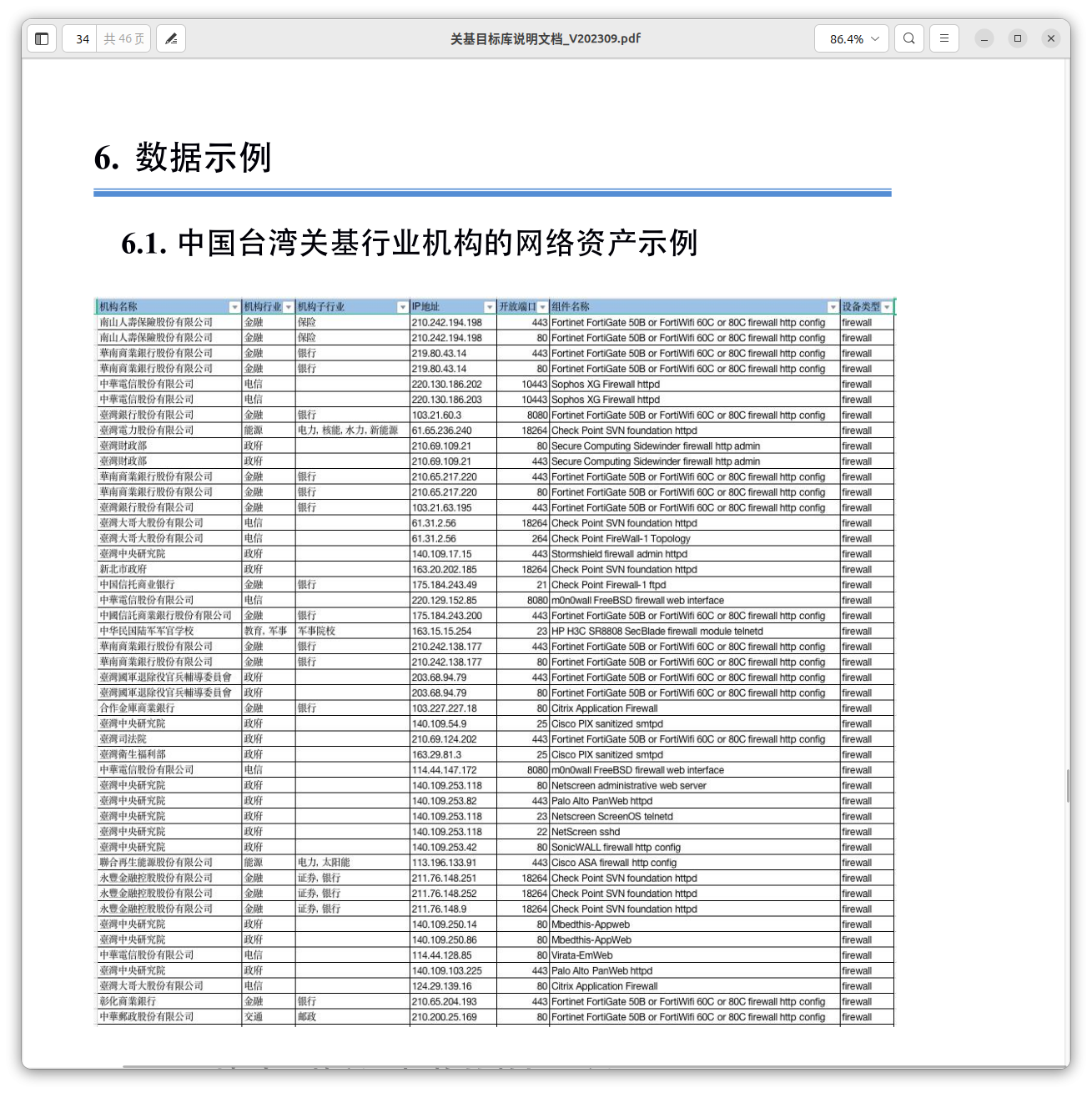
Another document references "1-day" exploits, which could be used to facilitate successful exploitation based on the results of network reconnaissance.
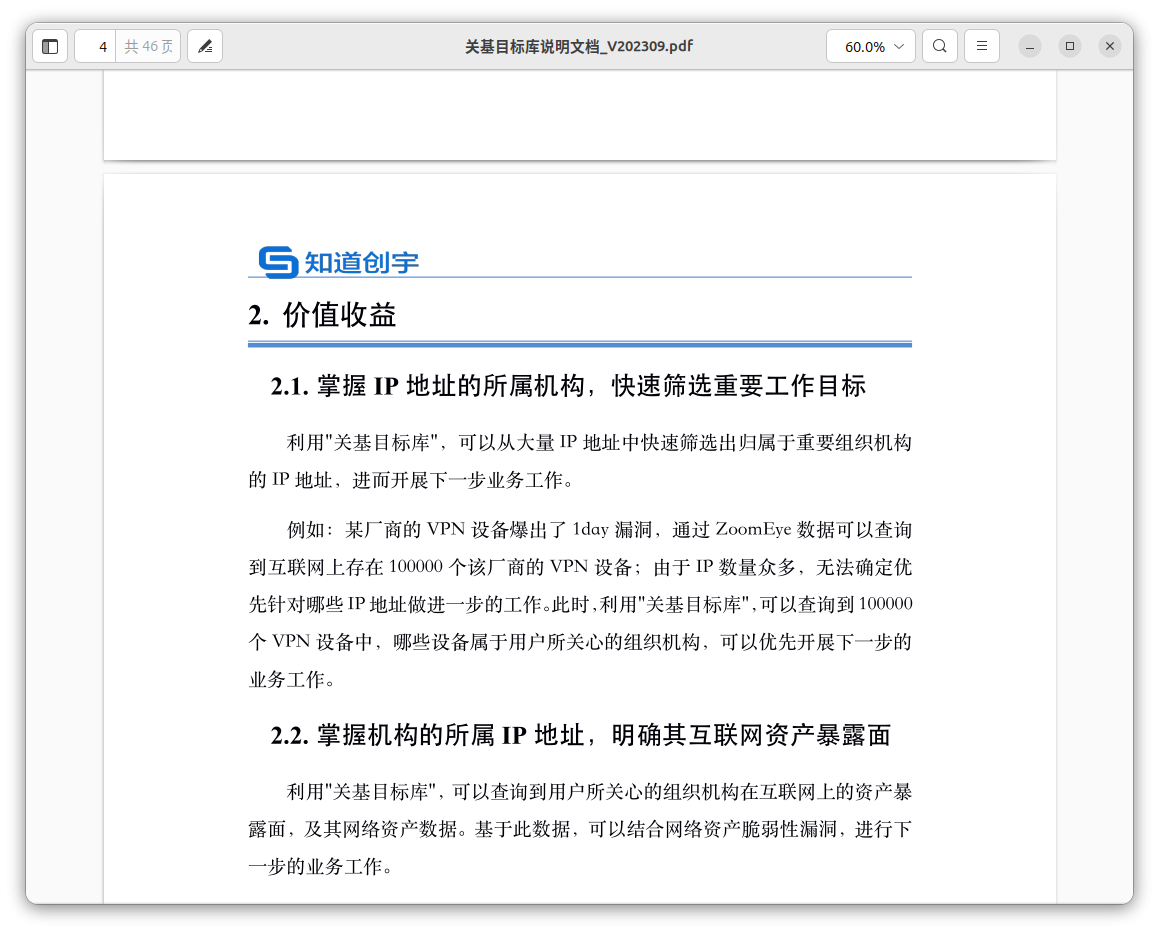
The document states:
“XXX company’s VPN has been exposed to an 1day loophole, and there are about 100,000 VPN devices, on the internet, of XXX company – searched via ZoomEye data. Because there are so many IPs, we’re unsure of which IPs we should target to continue our objectives. ”
The company was building a Critical Infrastructure Target Database (关基目标库) to navigate across the targets and prioritize them.
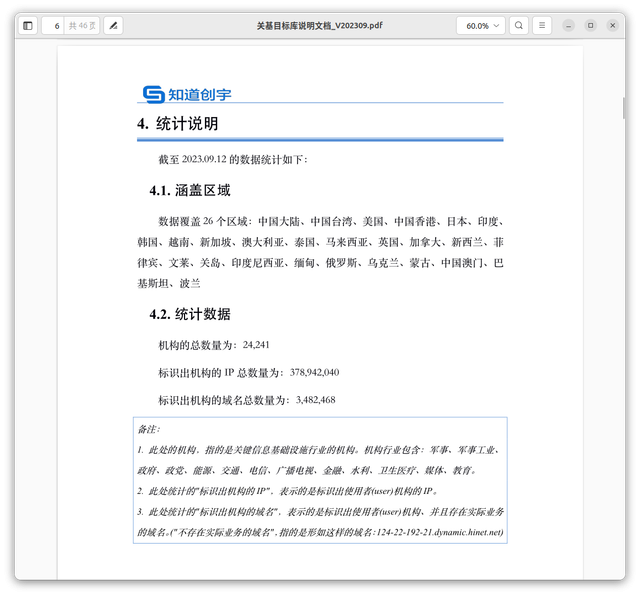
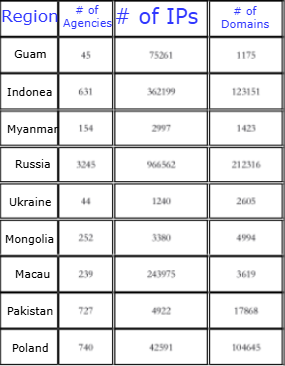
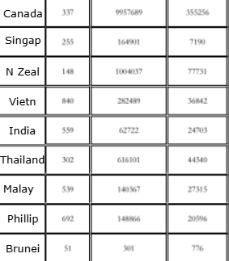
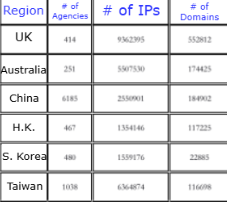
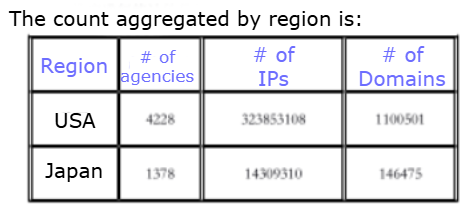
The following list of countries has been found as prioritized by Knownsec for further targeting: Taiwan, the US, Japan, India, Korea, Vietnam, Singapore, Australia, Thailand, Malaysia, the UK, Canada, New Zealand, Philippines, Brunei, Guam, Indonesia, Myanmar, Russia, Ukraine, Mongolia, Macau, Pakistan, and Poland. The observed statistics shows the following metrics around the number of targets under monitoring by Knownsec:
- Number of agencies/organizations (targets):
24,241 - Number of IPs associated with targets:
378,942,040 - Number of domains associated with targets:
3,482,468
By "targets," the following industries have been marked as high-priority: defense, arms manufacturing, government, political parties, energy, transportation, telecommunications, broadcasting, finance, healthcare, multimedia, and education.The biggest number of artifacts collected by Knownsec has been found associated with the United States, Canada, Japan and Russia.
ZoomEye Passive-Radar Product
One of the key products of Knownsec is ZoomEye, an alternative to Shodan and similar IPv4/IPv6 scanning platforms used to map network services and devices.
Official webpages and links of ZoomEye:
Based on the acquired context, the platform is used not only for reconnaissance purposes but also for targeting and exploitation.
Translated:
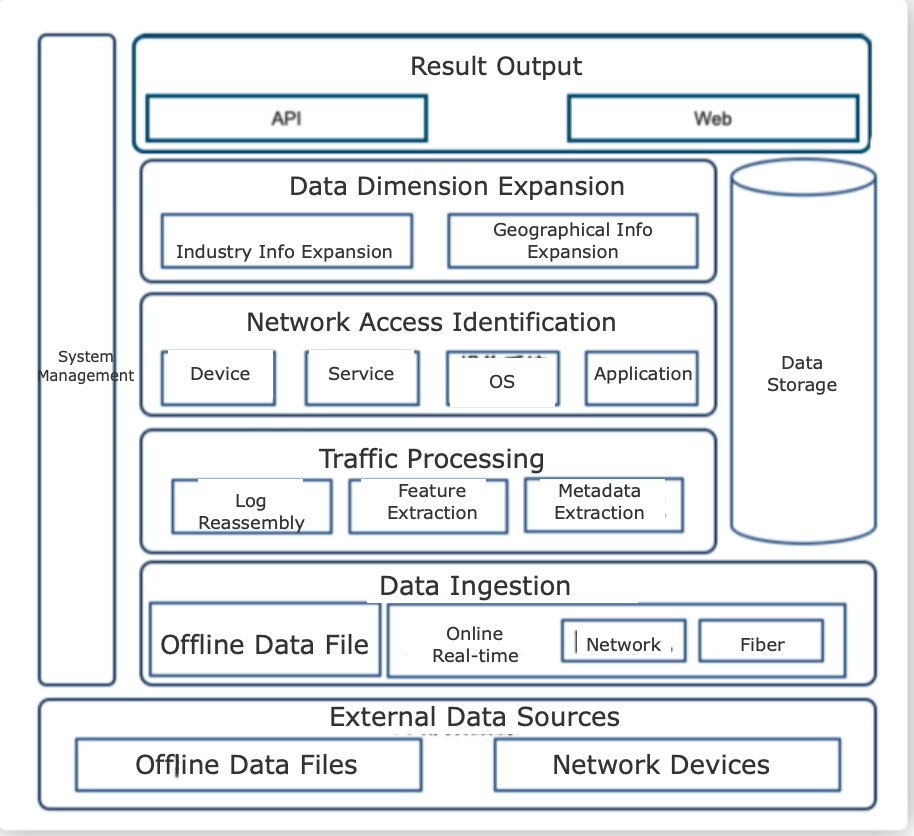
The operators may upload scans via FTP in the form of archives and PCAP files.
The operators may also add new data offline by providing structured files up to 500 GB.
Function | Explanation |
Mission Name | Name of the mission, do not repeat. |
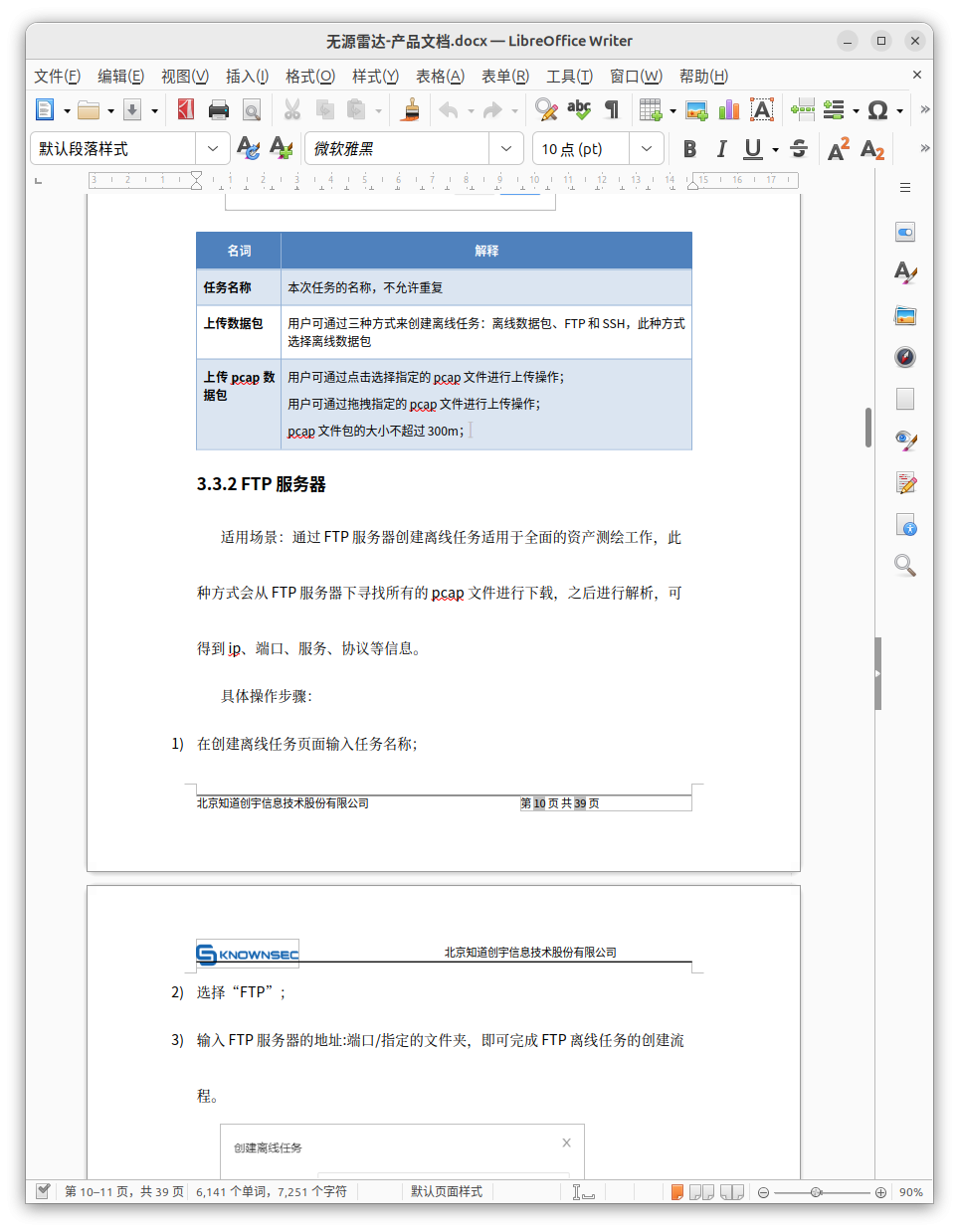
Uploading Datapack | Users could create offline missions via 3-ways: Offline Datapacks, FTP / SSH, these methods could select offline datapacks. |
Upload pcap Datapack | User can click on the specific pcap datapack to upload; User can drag the desired pcap datapack to upload; pcap datapack cannot be bigger than 300m; |
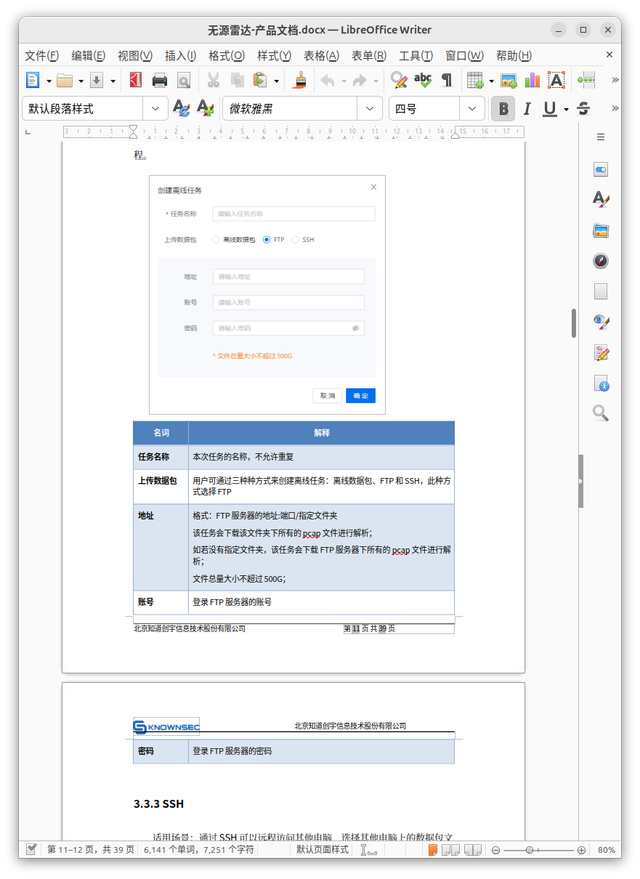
It is possible that operators may use other available methods to collect network reconnaissance data—for example, passively from intercepted network traffic. Such data sets for further ingestion into the platform are called "Offline Datapacks."
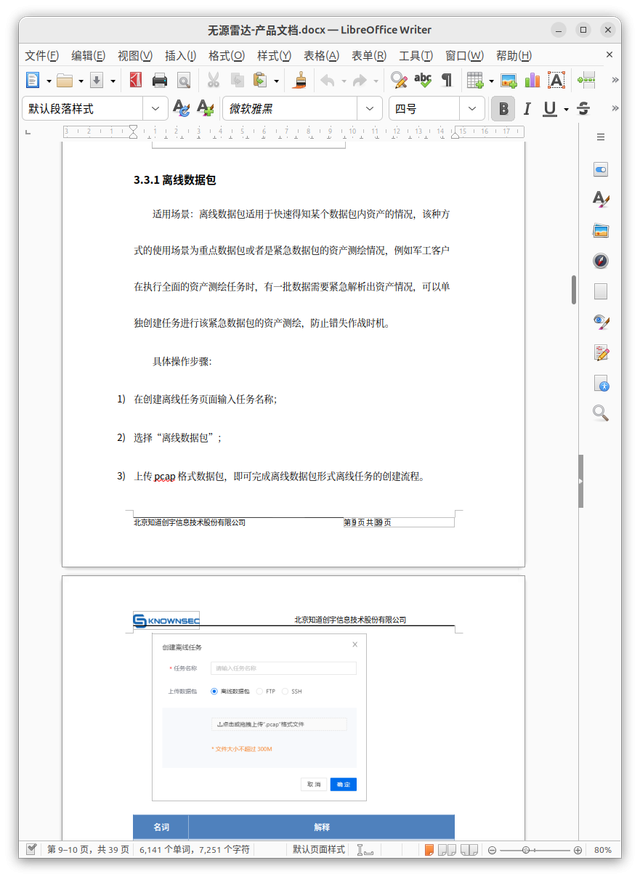
To add new "Datapack" the operators needs to:
- Enter the mission name in the Create-Offline-Mission page.
- Select “Offline-Datapack”.
- Upload pcap datapack, and then finishes the creation of an offline mission from an offline-datapack.
There’s also some documentations of ZoomEye related extensions and GPTs: https://github.com/zoomeye-ai. The ZoomEye GPT mentioned is a ZoomEye integrated system into DeepSeek that is only available in the Foreign Version (zhuanlan.zhihu.com/p/21881117943 ).
Staff Members
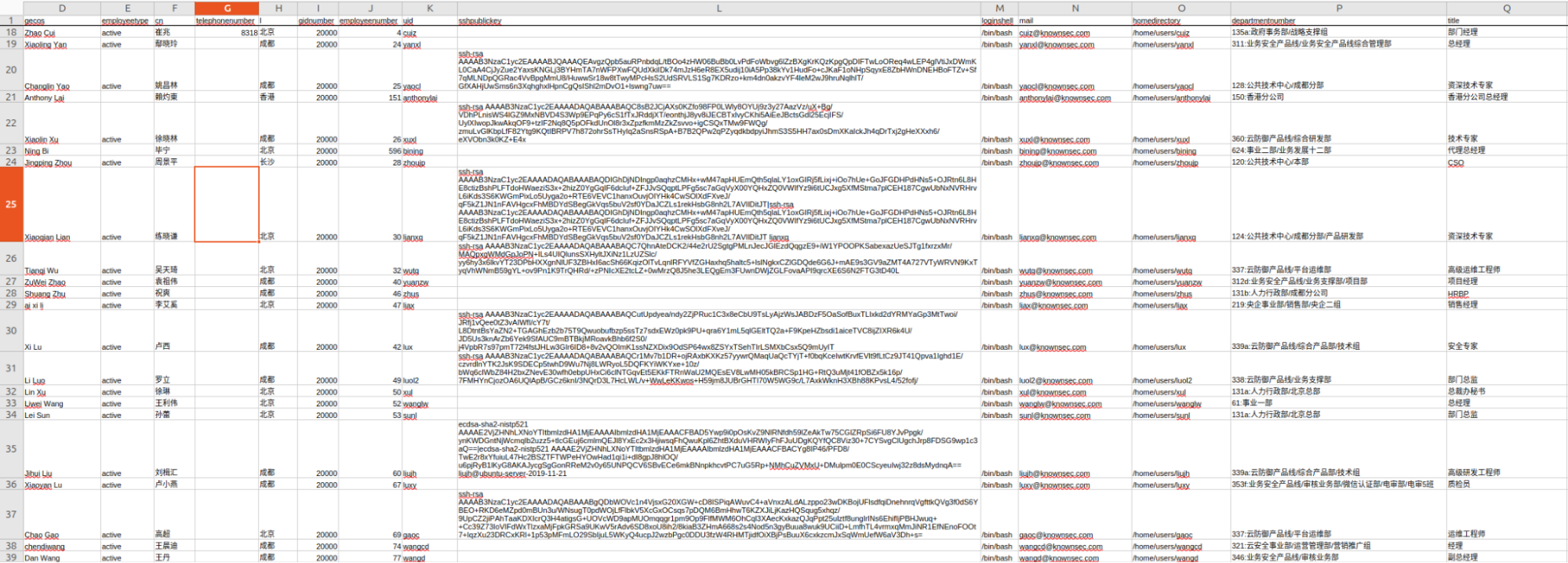
A list of Knownsec employees was identified, referencing various departments including the Department of Government Affairs, WeChat ID Verification, and the Cloud Defense Department. The staff is based in different geographical locations such as Beijing, Chengdu, Hong Kong, and Changsha.
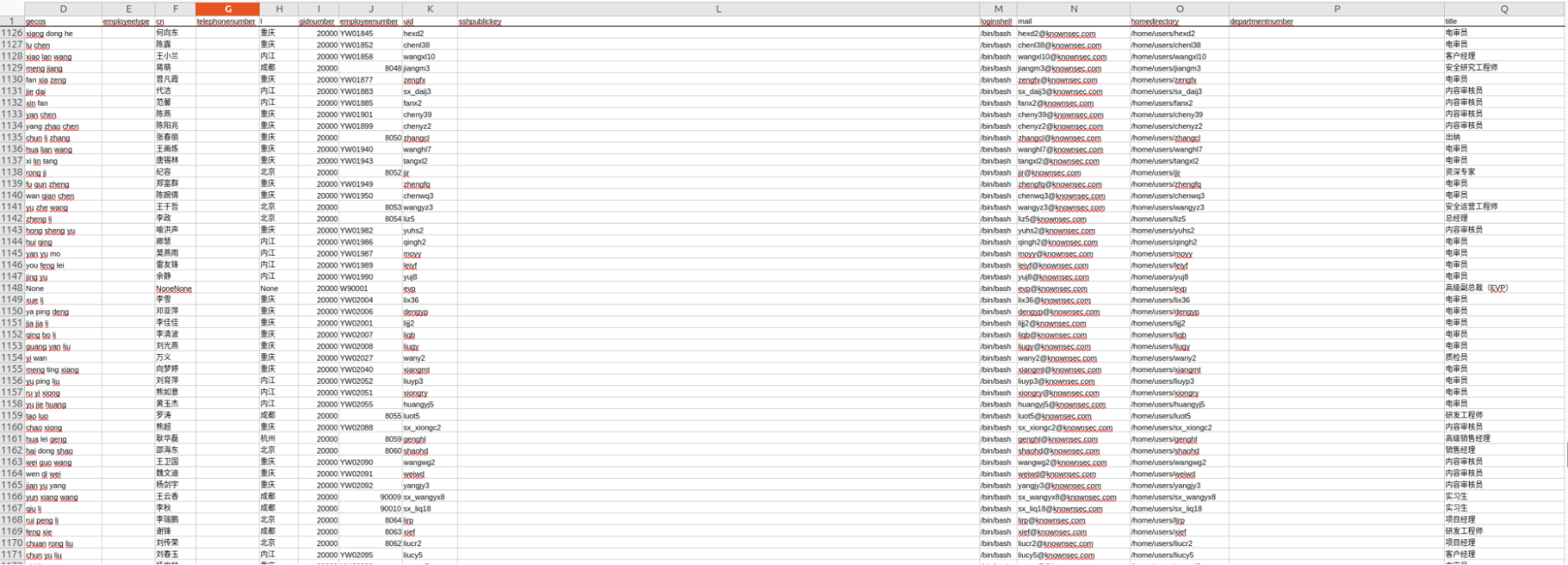
A second list of Knownsec staff members was also identified, although it does not specify departments. This list includes engineers, project managers, and interns. An interesting record named "NoneNone - None," marked as a Vice Executive Officer (EVP) with the email [email protected], was found—likely related to an employee who left the organization. The only EVP of Knownsec mentioned in public sources, according to OSINT collected, is Lu Hai (陆海), who is no longer with the company.
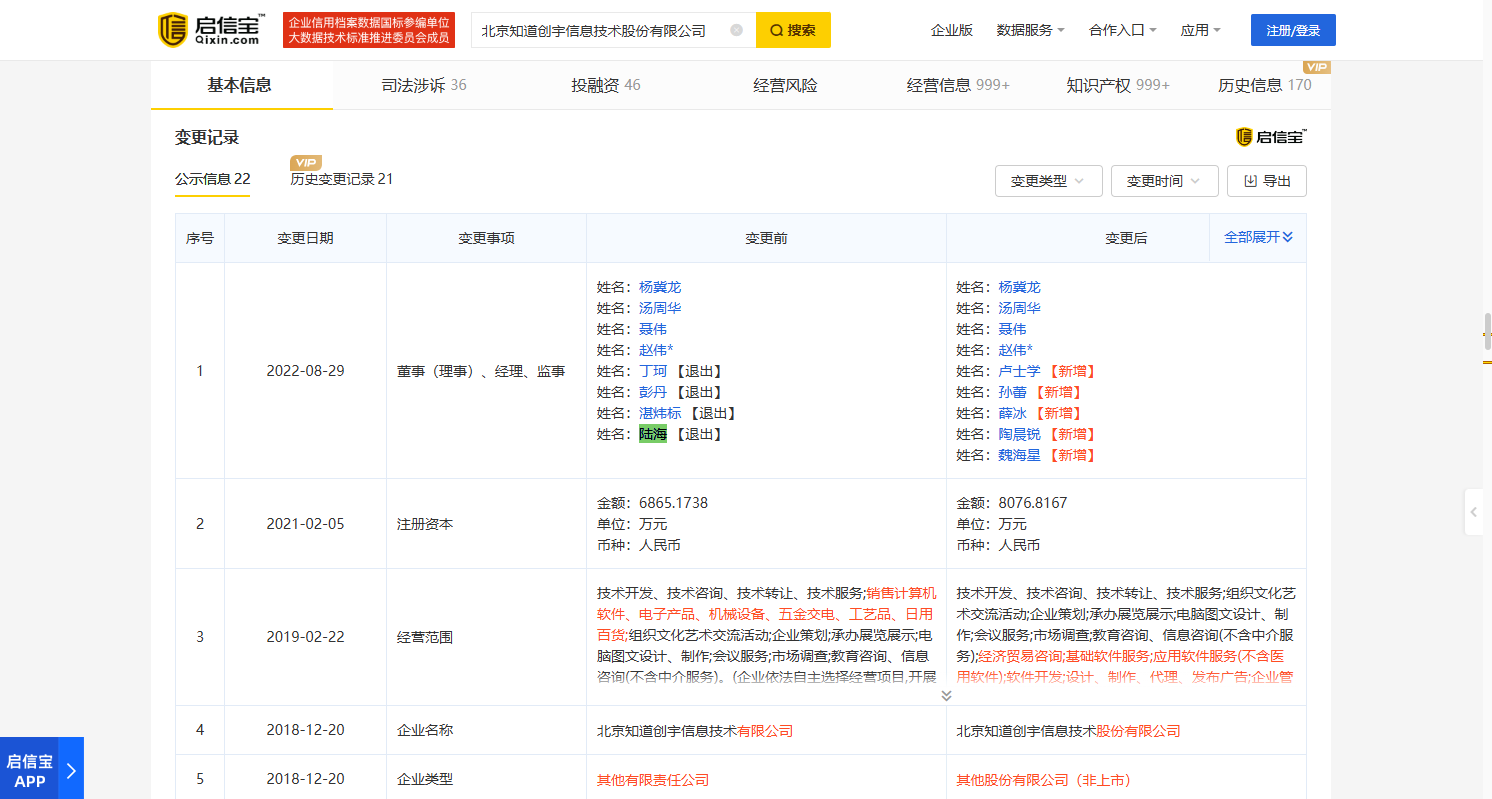
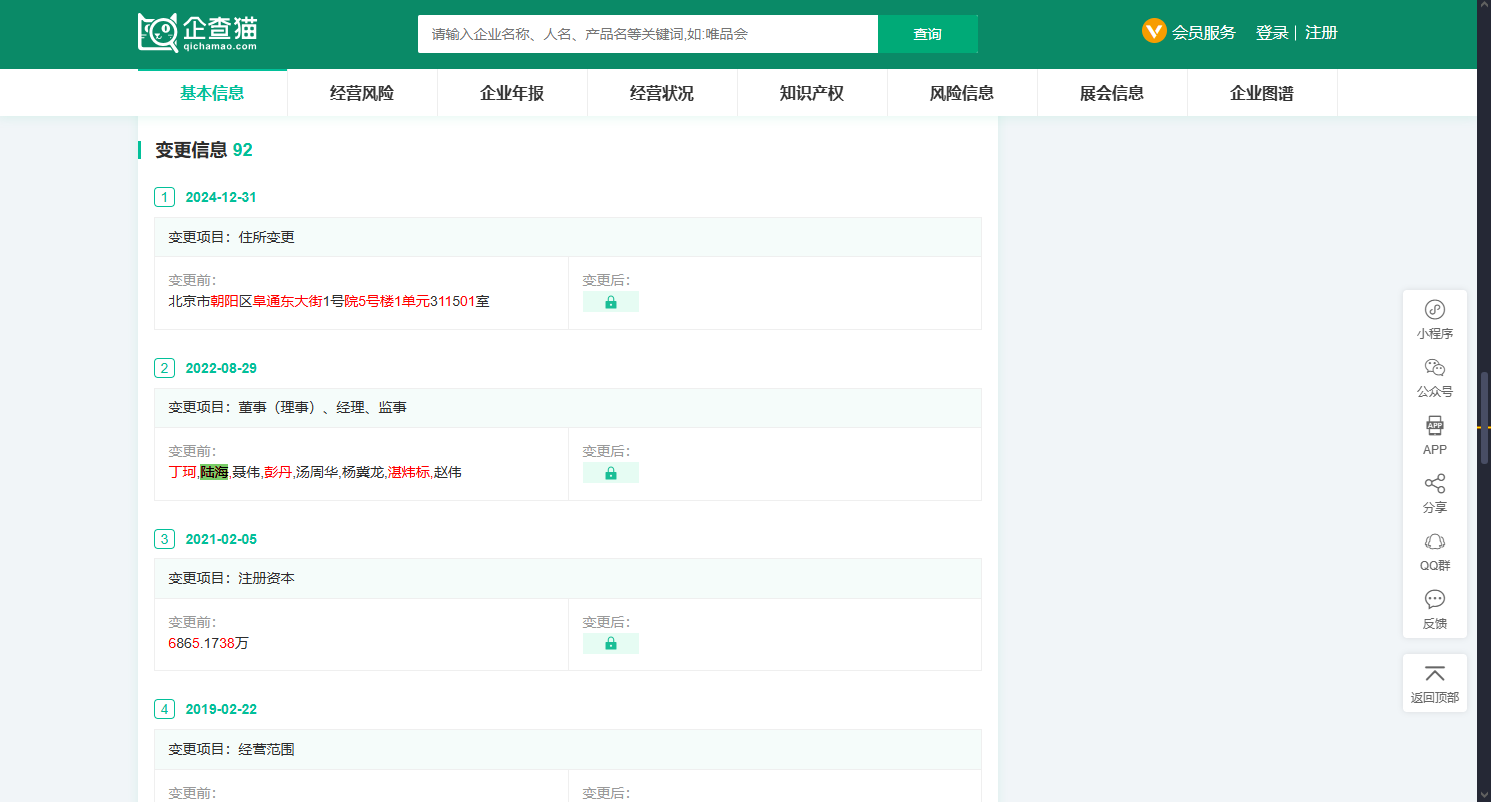
In a monthly journal published in 2018 Lu Hai was mentioned as an EVP. Another document released by KnownSec publicly shows a list of executive and administrative members of KnownSec.
One of the key staff members behind ZoomEye “钟馗之眼” is 李伟辰 (Li Wei Chen), mentioned as the Vice Chief Executive Officer of KnownSec.
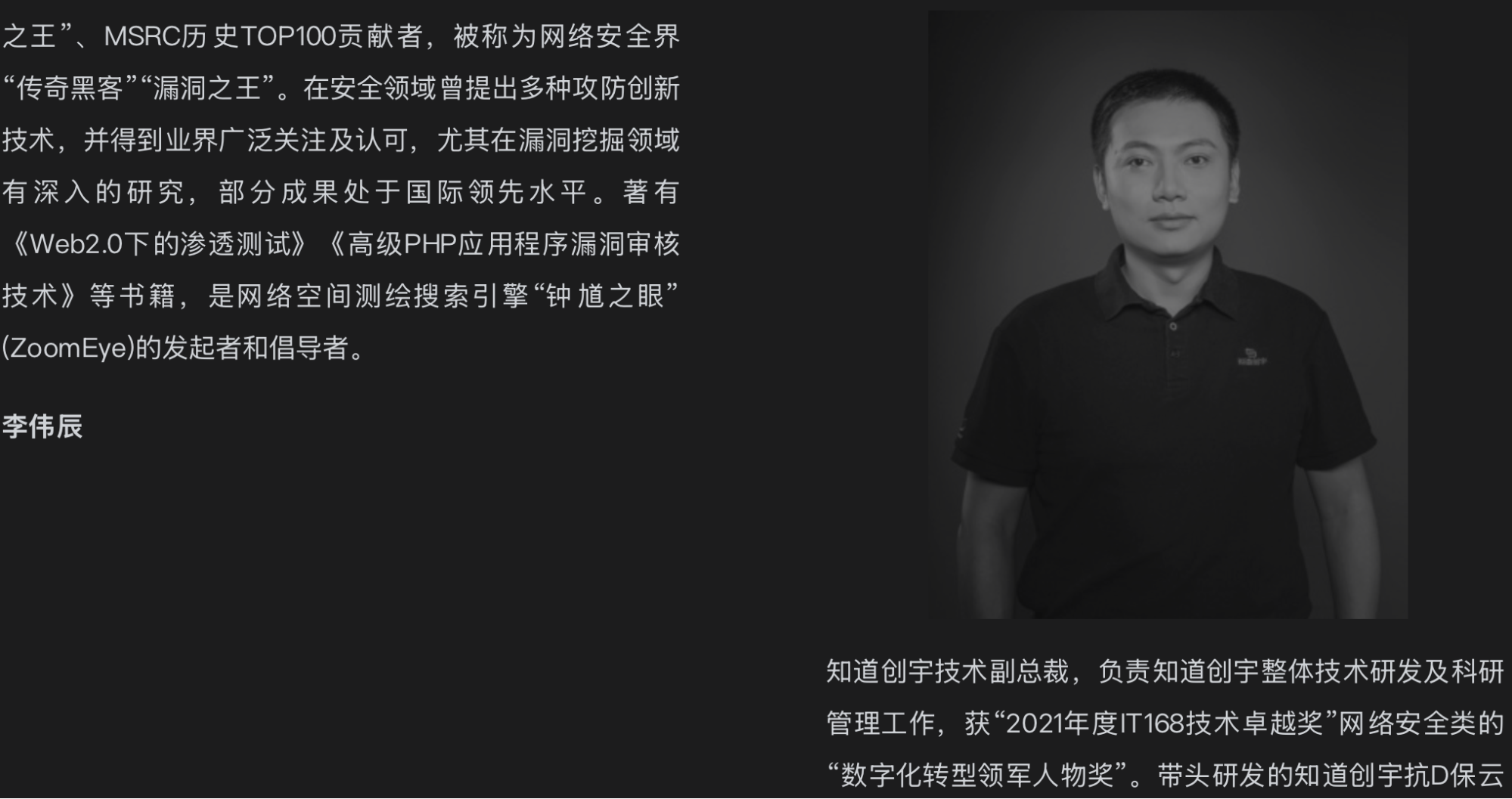
R&D lead of ZoomEye is 周阳(Zhou Yang), who according to OSINT is "responsible for scanning and crawling engines development".
The company's GitHub page referenced only 1 user @notsobad presumably involved in R&D operations.
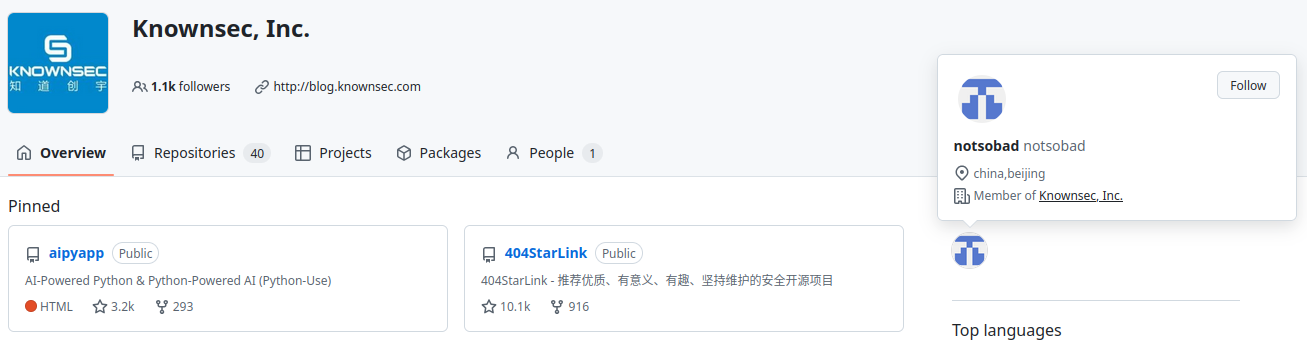
His personal blog mentioned Sichuan province – but his GitHub states he may be located in Beijing.
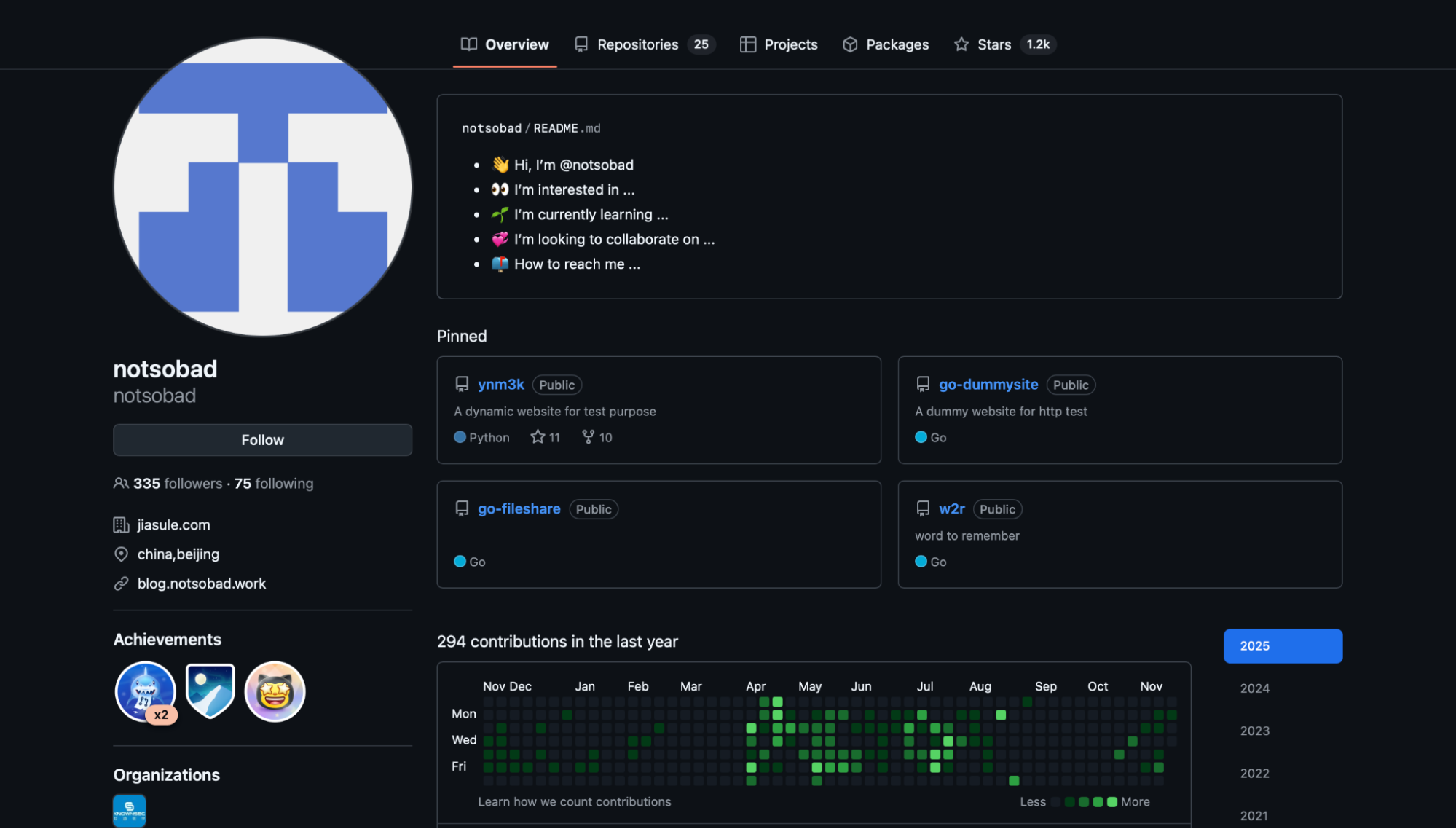
Other members have been identified via another Github account:
github.com/Knownsec404team (SeeBug)
KnownSec 404 Team is described as the leading global vulnerabilities and risks detection team in China. This team is one of the divisions of the company, focusing on Web and IoT threat hunting and vulnerability research. From its GitHub page, it suggests that the 404 Team is also known as KnownSec’s SeeBug team (seebug.org):
The team has a separate X account:
The official website has references to Knownsec and their products.
Notably, some of its members left the organization some time ago, but most of them have an extensive track record in vulnerability research and offensive cyber operations.

Public Security Ties
KnownSec is known to be involved with the Chinese government, military, as well as the Public Safety Department (Chinese People’s Police Department).
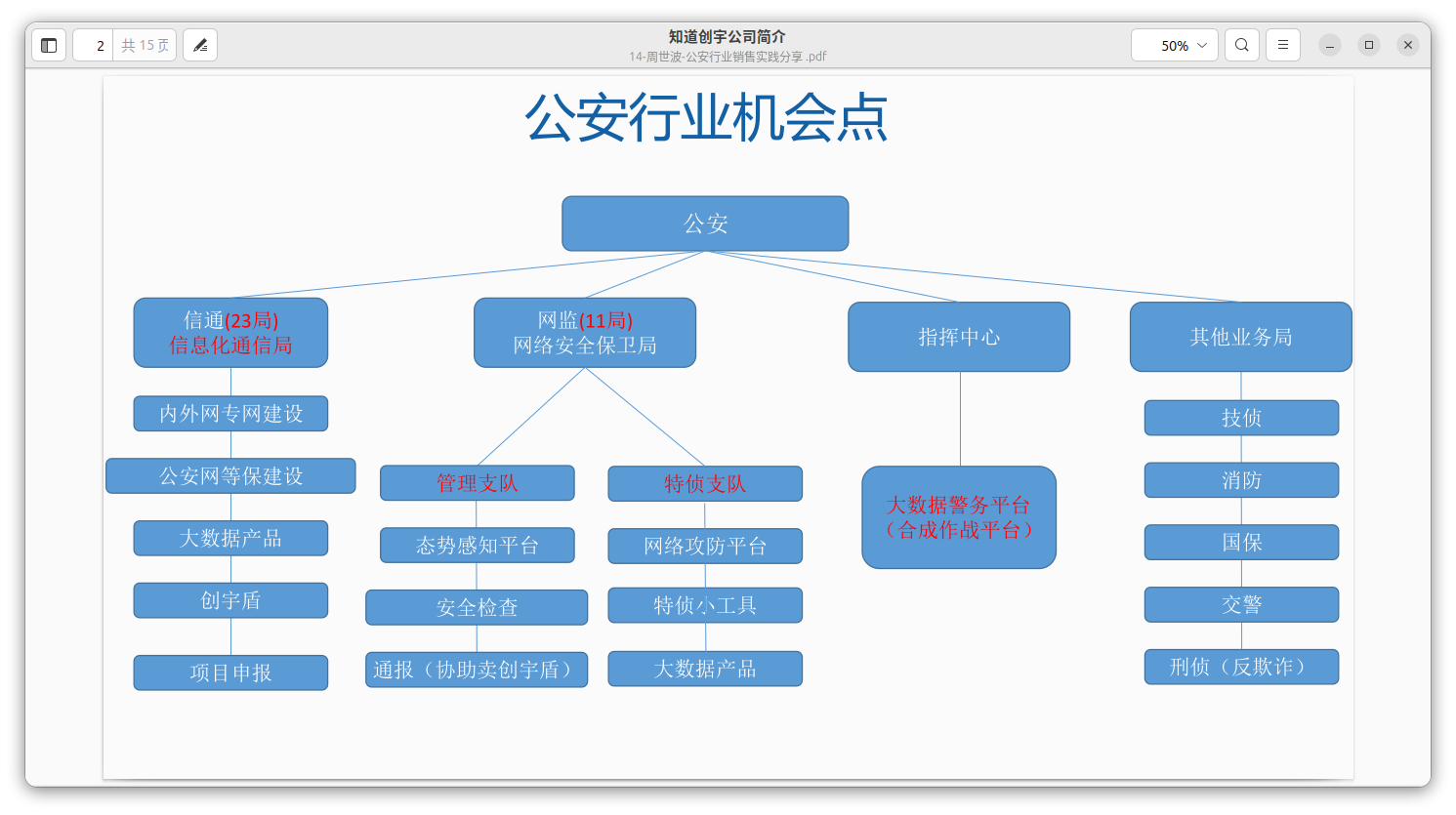
This diagram shows the connections with Chinese law enforcement, such as Telecommunication bureau (which includes R&D, LLM design, and deployment of 创宇盾, which stands for "Chuangyu Shield").
Translation:
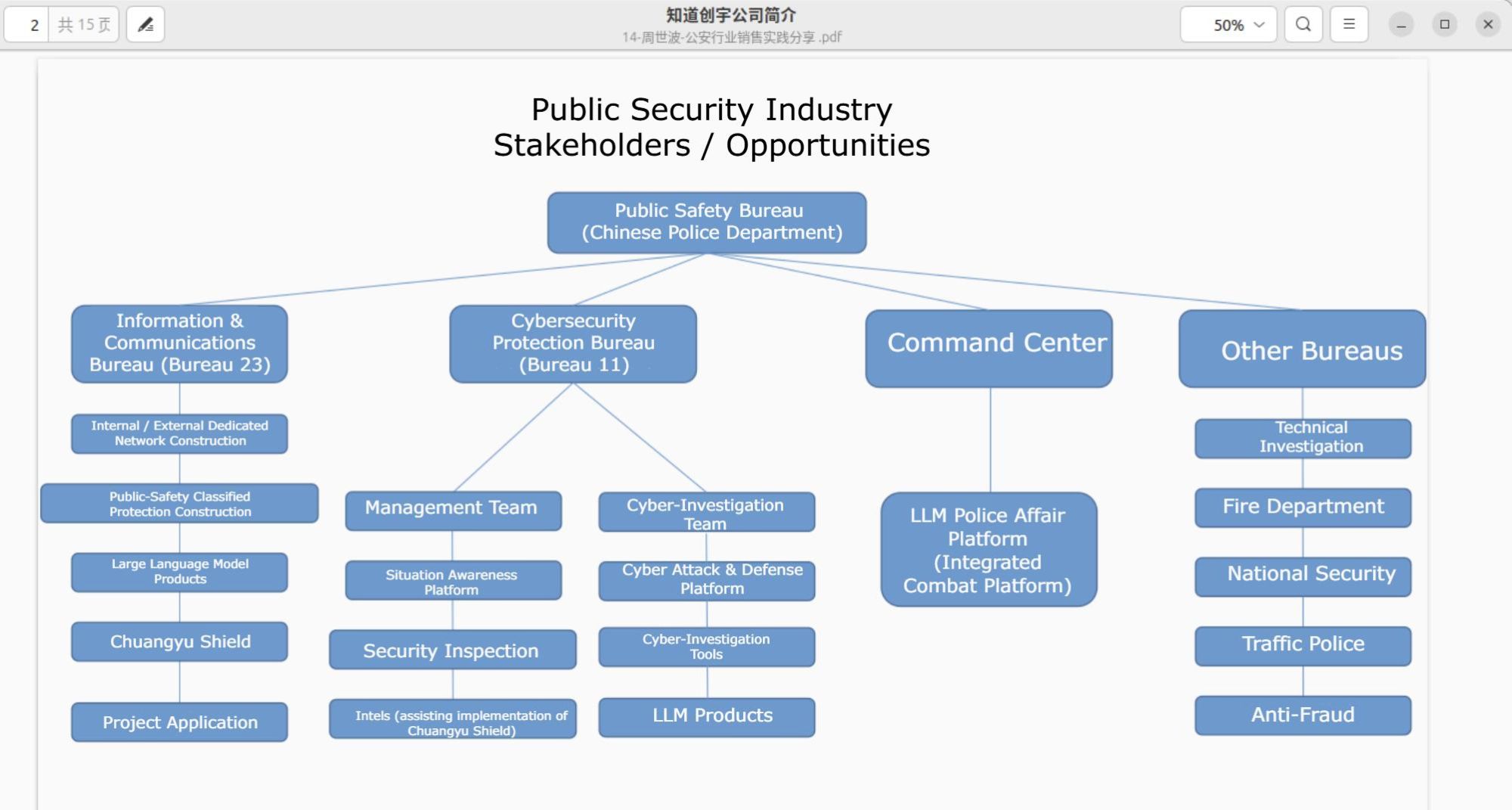
KnownSec is also developing projects with Chinese Internet Law Enforcement Bureau to facilitate Internet safety detection, cyber defense, and large language model (LLM) products design. Some other ones are involved with the fire department, traffic enforcement, investigations bureau, and anti-scam.
创宇盾 (Chuangyu Shield):
Provides defensive features against cyber-attacks by utilizing cloud computing, custom LLMs, and dynamic analysis. According to OSINT information, this project focuses on protection against web application vulnerability exploitation and zero-day attacks. It also leverages ZoomEye as an active scanning tool, likely to detect vulnerable hosts based on specific templates or patterns.
Chuangyu Shield has also been mentioned to be utilized as an anti-LLM crawling tool. In an article on Zhihu, Chuangyu Shield is mentioned as a tool to block LLM crawlers (e.g. ChatGPT) so that, specifically, foreign LLM users can’t use such tools to gain information on the Chinese government for more than 80 million crawl vists every day:

Chuangyu Shield also acts as a firewall with content inspection features to detect inappropriate or illegal under the Chinese internet laws. The service is deployed via cloud services, and it has been used by various customers, including: Chinese National Healthcare Security Bureau (国家医疗保障局), Chinese Police Web Systems(公安部网站系统), China Merchants Bank (招商银行), Tencent Security (腾讯安全), China Eastern Airline (东方航空). The white-paper document about Chaungyu Shield and its related sub-products can be found online.
Chinese Defense Industry and Government Connection
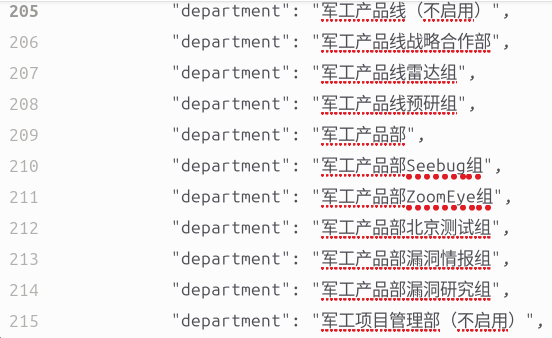
Documents confirming active customers of Knownsec, including Chinese military and government agencies, were identified, along with internal units of the company, such as:
- Military Production Line (Inactive)
- Military Production Line (Radar) Group
- Military Production Line (Research) Group
- Military Products (Seebug / ZoomEye) Departments
- Military Product Testing Group (Beijing)
- Military Product Weakness (Intelligence / Research) group
- Military Projects Management (Inactive)
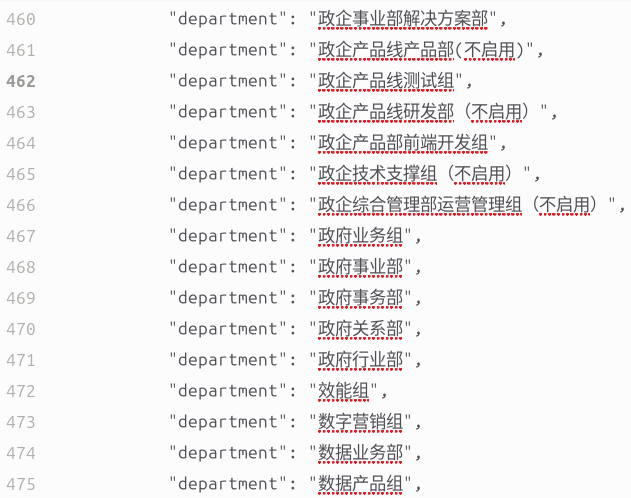
There were identified multiple references to government including:
- Gov-Corp Solutions Department
- Gov-Corp Production Department (Inactive)
- Gov-Corp Production Line Testing Group
- Gov-Corp Production Line Research Group (Inactive)
- Gov-Corp Product Front-end Development Group
- Gov-Corp Tech Support Group (Inactive)
- Gov-Corp General Management Group (Inactive)
- Government Matters Group
- Government Affairs Group
- Government Relations Group
- Government Sectors Group
- Group of Department Efficiency
- Digital Marketing Group
- Data Services
- Digital Products Group

One of the projects identified called “Research on Network Entity Data CJ and Integrated Key Technologies” related to Chinese Police No.3 Research Department, and an agreement (serial IG-201907-003) according to which KnownSec was responsible for solution design, reporting, and researching various cybersecurity matters.
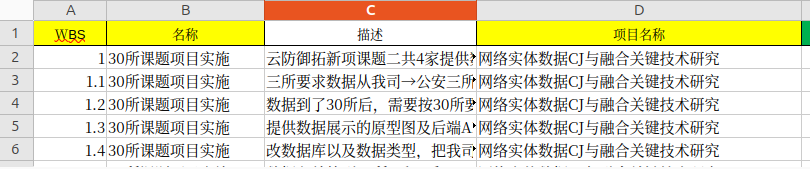
CJ stands for 采集(Cai Ji) - “collect / collection”. The purpose of the project is “Research on Key Technologies for Network Entity Data Collection and Fusion”.
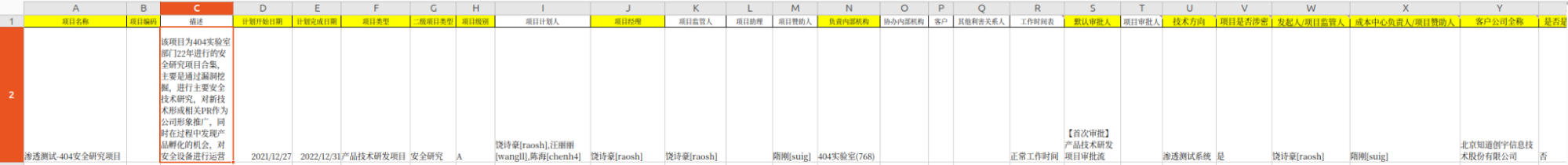
A document was also found in which Knownsec is mentioned as a client. The document references a penetration testing project called "404 Security Research," which started on December 27, 2021, and was completed on December 31, 2022. It is unclear whether stolen data could have been exfiltrated during any phase of the project. This initiative was described as a cybersecurity research effort focused on penetration testing and ethical hacking.
Additionally, a document referencing zero-day vulnerabilities was also discovered:

The project focused on zero-day vulnerabilities and potential misconfiguration flaws that could be identified in various products, "to facilitate awareness and research."


The project workflow included testing of servers and applications domestically, although without specific details or hostnames. It also referenced the Russia-Ukraine conflict, and Taiwan as targets for further "cyber cloud mapping." Likely, by this term, Knownsec refers to one of their internal projects called Cyberspace Mapping – Hardware Radar. What is publicly marketed under this name is known as the ZoomEye Passive-Radar product (网空云测绘).
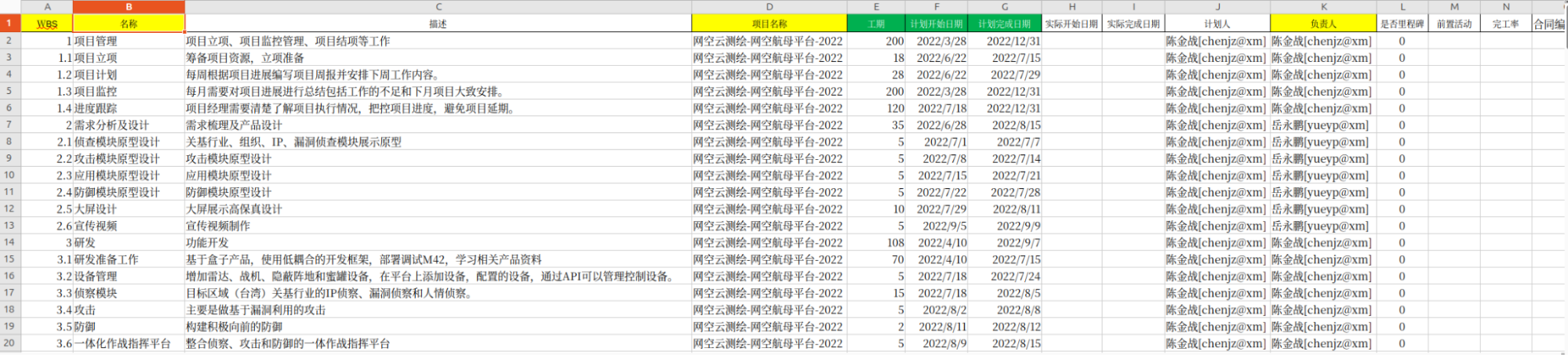
In some documents, ZoomEye Passive-Radar is also mentioned as part of the specifications for the Cyberspace Tradecraft Platform, which appears to be actively used in malicious activities targeting Taiwan for ongoing network reconnaissance. It is specifically designed to serve as a unified cyber warfare and combat command platform.
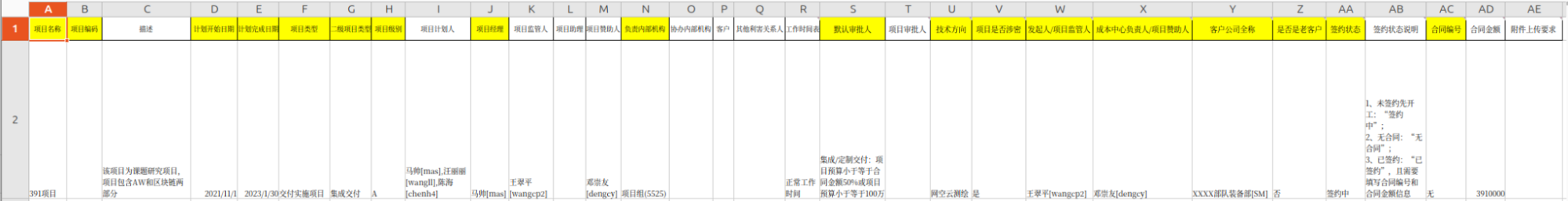
Notably, the project has a note labeled "391," which appears to be related to actual funding provided by the Chinese government, amounting to 39,100,000 Chinese Yuan (approximately 5,588,590.37 USD).
Cyberspace Mapping – Cyber Tradecraft Platform
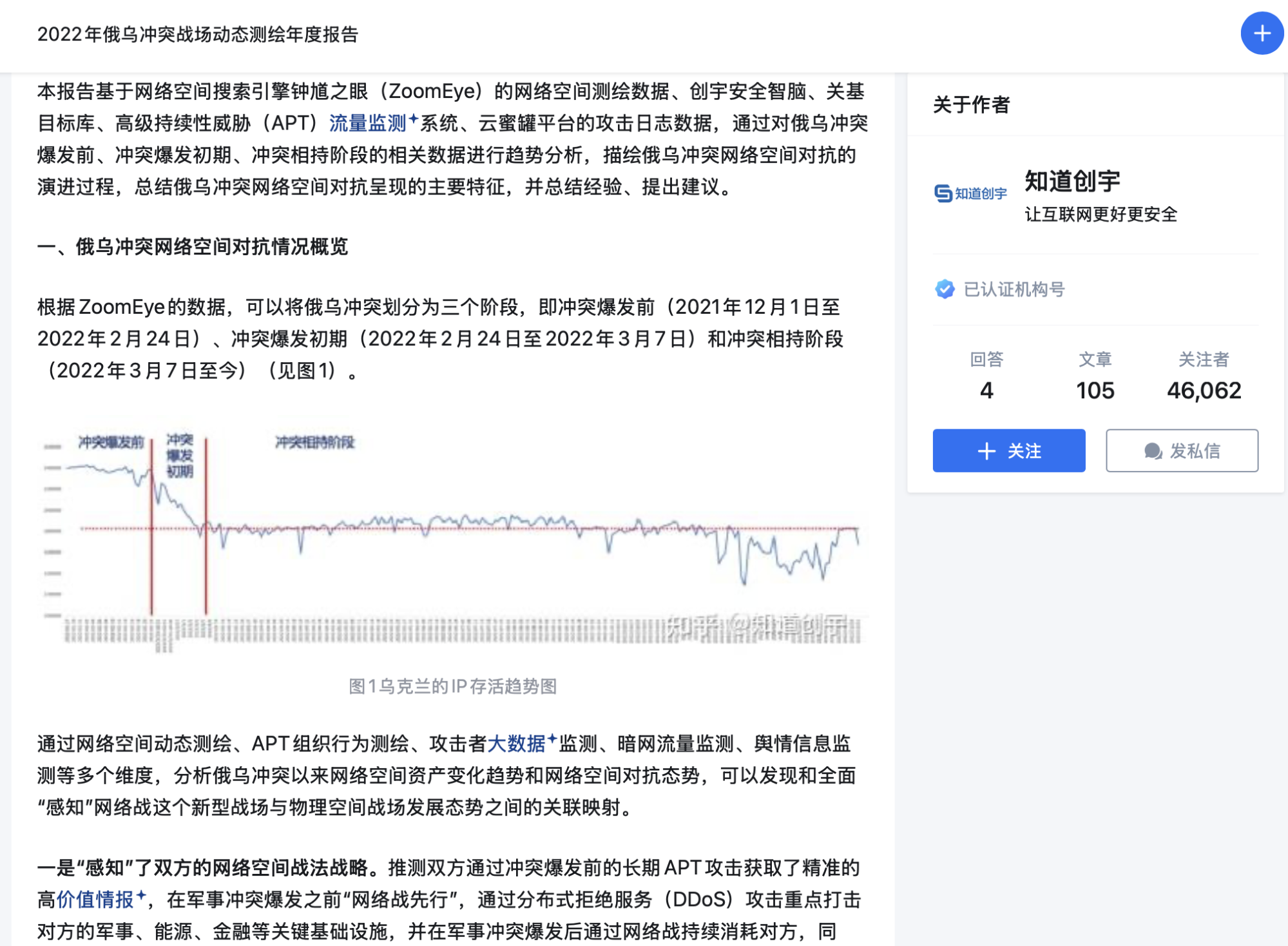
Cyberspace Mapping is delivered by ZoomEye to target foreign telecommunication infrastructure. A Zhihu post from the official account of Knownsec shared insights on how it could be used during the Russo-Ukrainian War, including identified mapping insights. The report describes the use of cyber warfare and details how ZoomEye conducted Cyberspace Mapping of activities related to the war:
The CEO of Knownsec, Zhao Wei, and his colleagues have published a book (ISBN: 9787111716051) describing the technology and its applications in government and other sectors.

The abstract describes three parts of the book: Concepts and Technology, ZoomEye Application, and Real-World Applications.
Clients of KnownSec
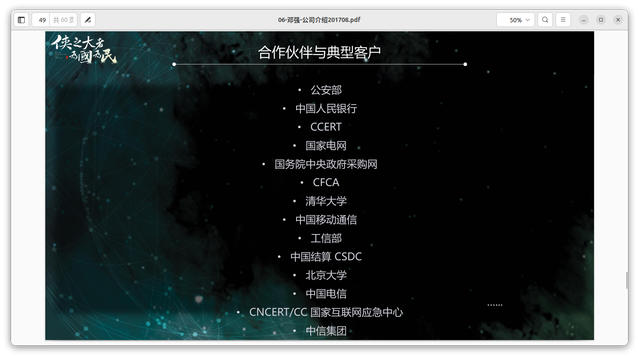
There were identified several leaked documents referencing possible clients of Knownsec:
- China People’s Police Department
- China People’s Bank
- CCERT
- State Grid Corporation of China
- Central Government Procurement Network of the State Council
- CFCA
- Tsinghua University
- China Mobile
- Ministry of Industry and Information Technology (MIIT)
- China Securities Depository and Clearing Corporation Limited
- Peking University
- China Telecom
- CNCERT/CC
- CITIC Group
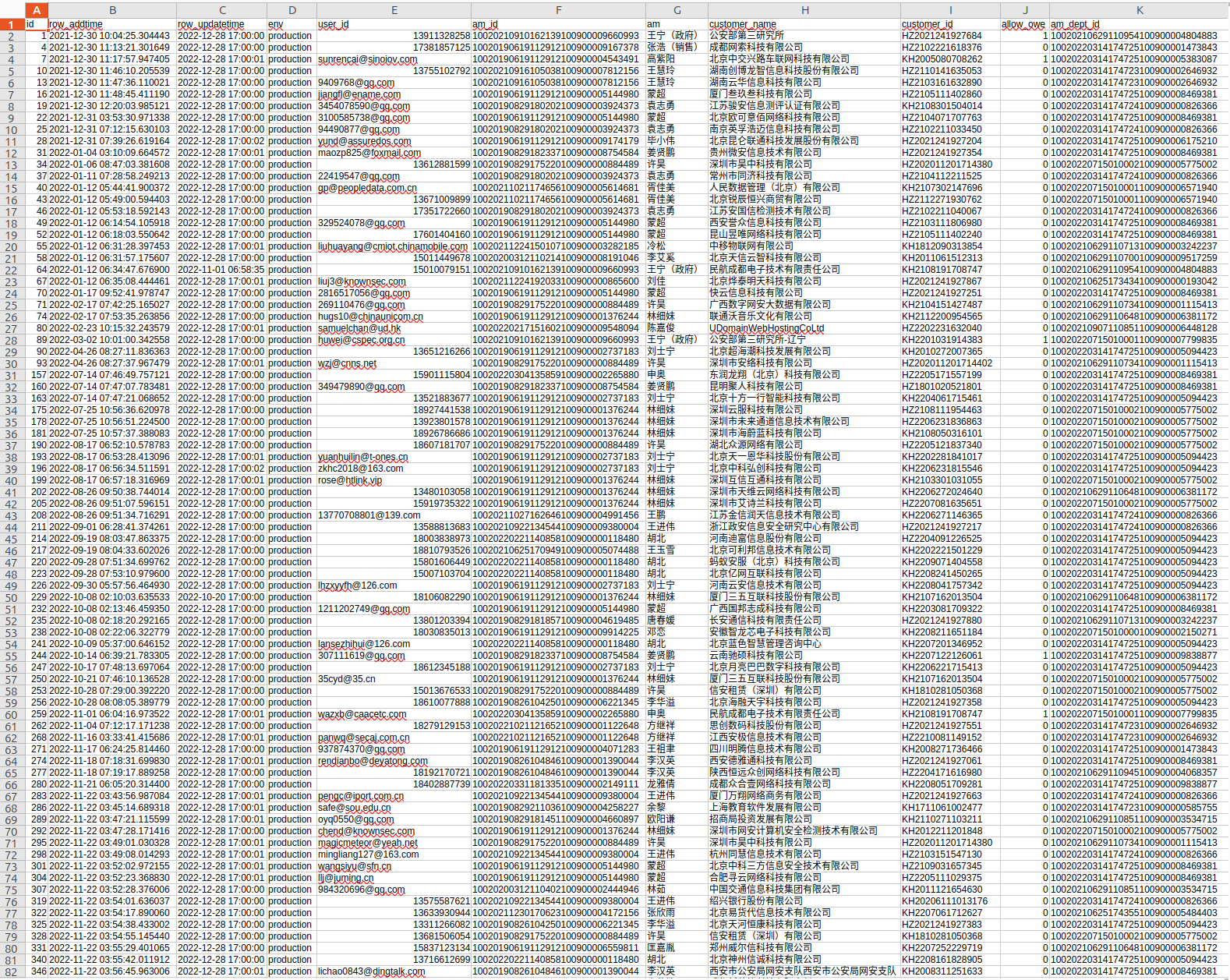
The list of Knownsec customers also includes less-known, smaller companies and Chinese internet/information technology companies, along with regional law enforcement bureaus.
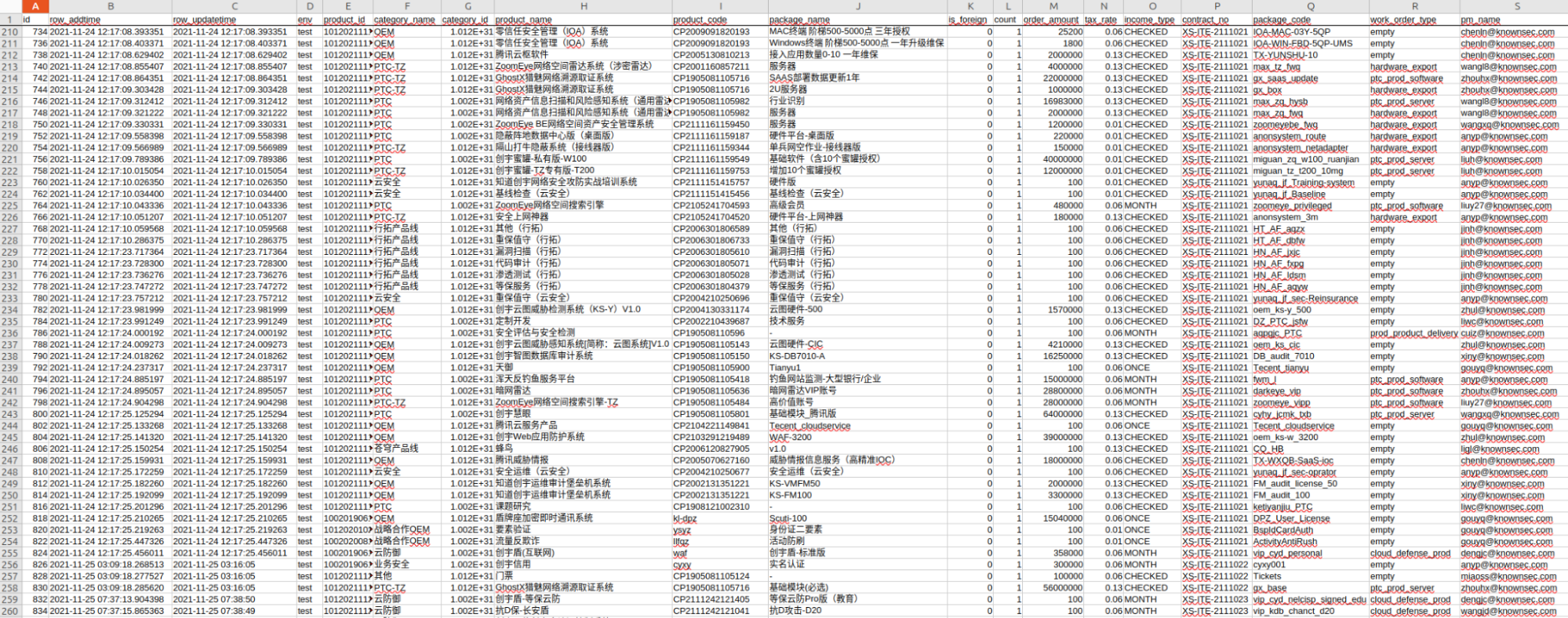
Besides public sector clients, there are identified references to private sector partners and their products, likely used in joint projects, including:
- Tencent: Tencent Cloud Security
- Tencent Threat Intelligence
- DarkWeb Radar
- KnownSec Cybersecurity Att/Def Training Systems
- Huntian Anti-Phishing Service Platform
Knownsec and Related GEOINT:
Knownsec has several locations in Mainland China:

Beijing Headquarters (HQ):
15th Floor, Tower T3-A, Wangjing SOHO Center, Fu’an West Road, Chaoyang District, Beijing

Chengdu Branch:
9th Floor, Tower C, Maoye Center no. 28 Tianfu Avenue North Section, Wuhou District, Chengdu, Sichuan

Shenzhen Branch:
Room 1505 Block C, Dachong Business Ctr, High-Tech Park, Nanshan District, Shenzhen

Shanghai Branch:
Room 22D, Zhaofeng World Trade Bldg, Changning District, Shanghai

Wuhan Branch:
Room 1908, Tower A, Fanyue Center, Pangxiejia, Wuchang District, Wuhan, Hubei
Shaanxi Branch (Xi’an):
Room 2610, Tower C, Tangfeng Intl Plaza no. 18 Fenghui South Rd, High-Tech Zone, Xi’an, Shaanxi
Hong Kong Branch:
Details not publicly provided.
Hong Kong Branch website: https://www.knownsec.com.hk/
LinkedIn: www.linkedin.com/company/knownsec-hong-kong/
The Third Research Institute of Ministry of Public Security (MPS)
The Third Research Institute of Ministry of Public Security (MPS) has been mentioned as one of Knownsec's customers:
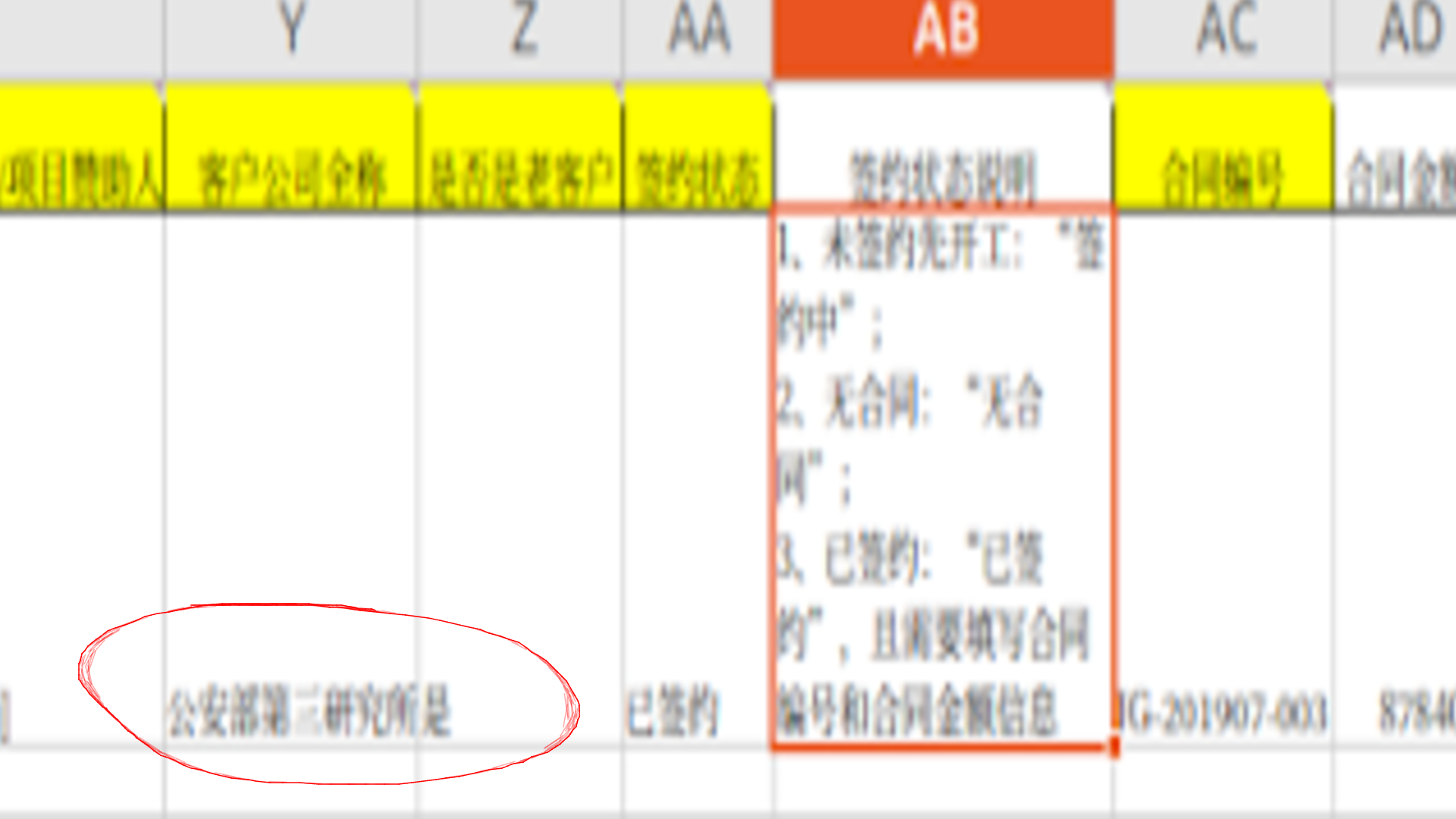
The Third Research Institute of Ministry of Public Security (公安部第三研究所) is an institute under the MPS founded in 1978. It was initially named “Shanghai Public Security Science Research Institute” (上海公安科学研究所). According to a 2024 official report, the institute consists of 2200 members (1900 field operators and technicians, 700+ members have Master’s or Ph.D degrees).
Its business scope includes computer software and hardware; wired and wireless communication equipment and image transmission equipment; specialized optical forensic technology equipment; electronic optics; security alarm equipment; design, development, production, sales, and technical guidance for security surveillance systems; and import–export operations approved by the Foreign Economic and Trade Commission.
It is located at 76 Yueyang Rd, Xu Hui District, Shanghai, China, 200031.

It also consists of 18 bureaus and departments and 6 affiliated companies.
- Research Departments:
- National Engineering Laboratory:
- National Engineering Laboratory for Cyber Incident Early Warning and Prevention Technology
- National Engineering Laboratory for Key Technologies of Information Security Classified Protection
- National Engineering Laboratory for Collaborative Security Technologies of LLM
- National Research Center:
- National Research Center on Anti-Computer Intrusion and Antivirus
- National Quality Supervision and Testing Center:
- National Quality Supervision and Testing Center for Cyber and Information System Security Products
- Key Laboratory of the MPS:
- Key Laboratory of Information and Network Security of the MPS
- Product Testing Center of the MPS:
- Information Security Product Testing Center of the MPS
- Evaluation Center of the MPS:
- Information Security Classified Protection Evaluation Center of the MPS
- Affiliated Business Departments:
- Cybersecurity Technology R&D Center,
- Cyber Investigation Technology R&D Center,
- IoT Technology R&D Center,
- Specialized Technology R&D Center,
- Data Security Technology R&D Center,
- Testing and Certification Center,
- Cybersecurity Classified Protection Center,
- Cryptography Technology Division,
- Economic Crime Investigation Technology Division,
- Intelligence and Command Technology Division,
- Narcotics Control Technology Division,
- Security Prevention Technology Division,
- Information Security Technology Division,
- Data Policing Technology Division,
- Public Safety Technology Division,
- Northwest Technical Service Center,
- Education and Evaluation Center,
- Information Network Security Journal (News) (《信息网络安全》杂志社)
- Affiliated Companies / Corporations:
- Shanghai International Tech-Trade United Co., Ltd.,
- Shanghai Chenrui Information Technology Co., Ltd.,
- Beijing Ruian Technology Co., Ltd.,
- Shanghai Public Security Equipment Co., Ltd.,
- Shanghai Netshield Intelligent Technology Development Co., Ltd.,
- Shanghai Haidun Security Technology Training Center.
Details of The Affiliated Corporations:
1) Shanghai International Tech-Trade United Co., Ltd (上海国际技贸联合有限公司):
https://www.linkedin.com/company/上海国际技贸联合有限公司
http://www.ittc.sh.cn
It is a state-owned corporation under the Third Research Institute of MPS. Founded on March 3, 1997, and headquartered in Xuhui District, Shanghai. The company focuses on security protection systems, intelligent building design and construction, and software information technology services, holding Class-A qualifications and High-Tech Enterprise certification. It has participated in the security work of the 2010 Shanghai World Expo, undertaken the construction of public security sub-control centers, and developed technical security supervision platforms. The Chief Executive Officer is Cao Ning (曹宁),
2) Shanghai Chenrui Information Technology Co., Ltd., (上海辰锐信息科技公司):
Hereinafter referred to as ‘Chenrui Company (CRTEK, CRTEK Group, Create Group)’, was founded in 1993, with a registered capital of 20 million yuan, and is a wholly owned subsidiary under the Third Research Institute of the MPS.
Chenrui functions as the institute’s primary vehicle for technology transfer and product commercialization, leveraging shared research and development (R&D) resources, facilities, and internal intelligence channels. It promotes institute-developed technologies nationwide and provides technical equipment and services to frontline public security units. Core business areas include information network security system construction, software development, security system integration, security product R&D, and system testing.
3) Beijing Ruian Technology Co., Ltd., (北京锐安科技有限公司):
Established on January 15, 2003. It is jointly owned by the Third Research Institute of the MPS (54%) and Aerospace Industry Development Co., Ltd. (航天工业发展股份有限公司) (43.34%). The company is headquartered on the 7th floor of Building B-2, Zhongguancun Dongsheng Science Park, No. 66 Xixiaokou Road, Haidian District, Beijing. The legal representative is Jin Bo (金波).
Ruian positions itself as an LLM-driven information solutions provider, focusing on LLM-based services, cybersecurity, and information-technology equipment. Its core business includes data sensing and governance, cybersecurity products (such as optical data-diode systems), and intelligent solutions. Its customers include public security, cyberspace administration, judicial agencies, and other government departments.
4) Shanghai Public Security Equipment Co., Ltd., (上海公共安全器材有限公司):
Formerly “Shanghai Public Security Equipment Factory” (上海公共安全器材厂), is a limited liability company established on February 9, 1985. It operates under the Third Research Institute of the MPS and is primarily engaged in wholesale and retail business.
5) Shanghai Netshield Intelligent Technology Development Co., Ltd., (上海网盾智能科技发展有限公司):
Wholly state-owned enterprise under the Third Research Institute of the MPS. It was established on April 30, 1993, and is registered at Room 501, No. 58 Yueyang Road, Xuhui District, Shanghai. The company has a registered capital of RMB 5 million and is structured as a limited liability corporation wholly owned by a non-natural-person legal entity. The current legal representative is Wang Yi (王毅, updated on December 24, 2024). It operates in the technology promotion and application services sector. Its main business includes computer system services, construction project design and implementation, and property management.
6) Shanghai Haidun Security Technology Training Center (上海海盾安全技术培训中心):
Founded in 2005, is a private non-enterprise entity wholly established by the Third Research Institute of the MPS. The center specializes in technical training in public safety and information systems, with more than a decade of experience in information and network security. It provides courses on network-security configuration and defense, application-security management, and related topics. As a national continuing-education base for professional technical personnel, it offers specialized programs such as legal knowledge for computer and IT professionals, taught by experts from the public-security system, universities, and research institutions. Address: No. 76 Yueyang Road, Xuhui District, Shanghai. Legal representative: Huang Zhen (黄镇).
Conclusion
Overall, the collected material points to an organization operating far beyond the scope of a conventional cybersecurity vendor. Knownsec appears to combine commercial security products with large-scale data aggregation, offensive tooling, and close collaboration with government, public security, and military entities. The breadth of datasets, the nature of the capabilities shown, and the number of state-linked projects indicate a role that aligns with national-level intelligence collection, cyber-operations support, and network infrastructure mapping.

